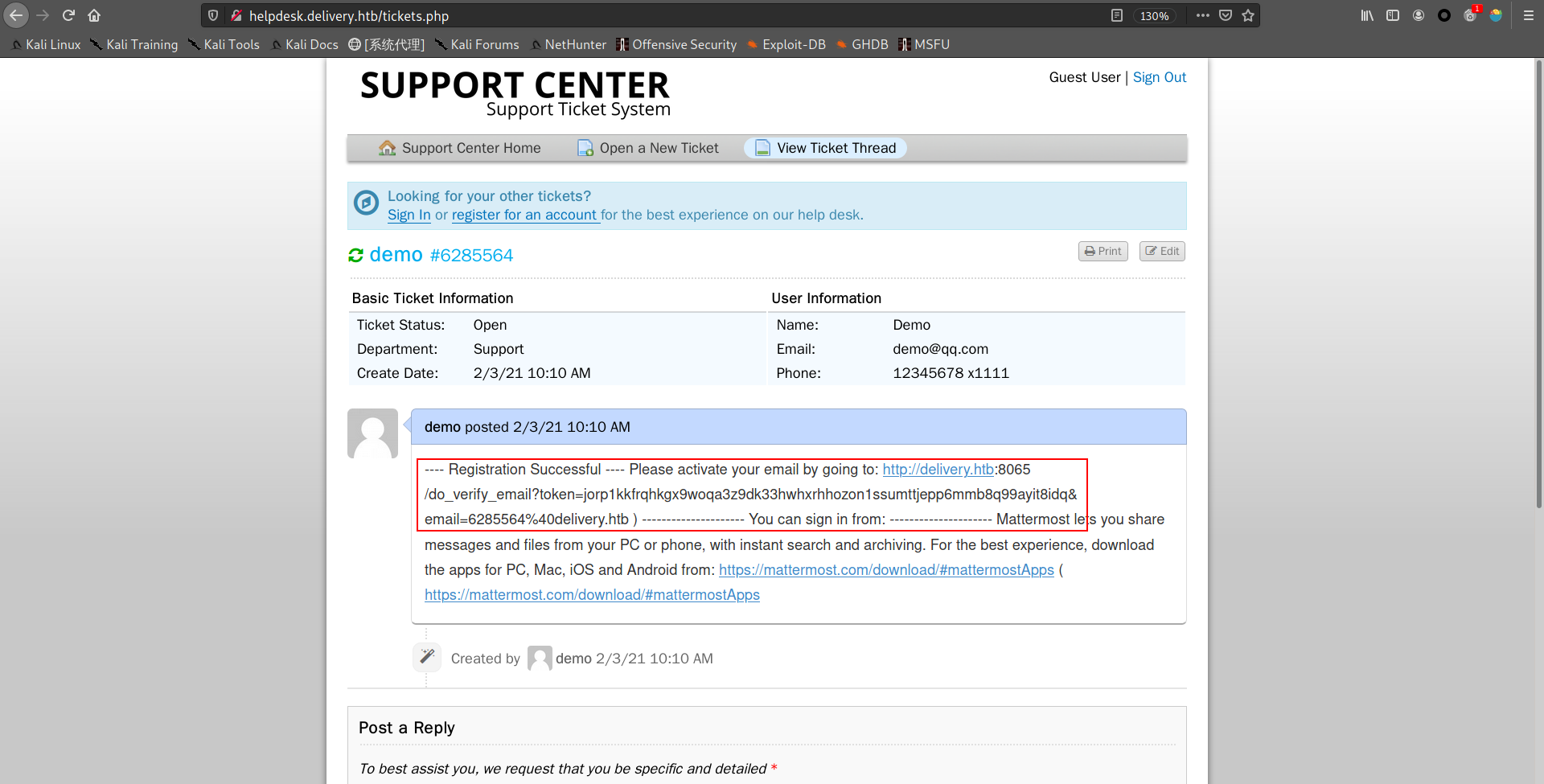
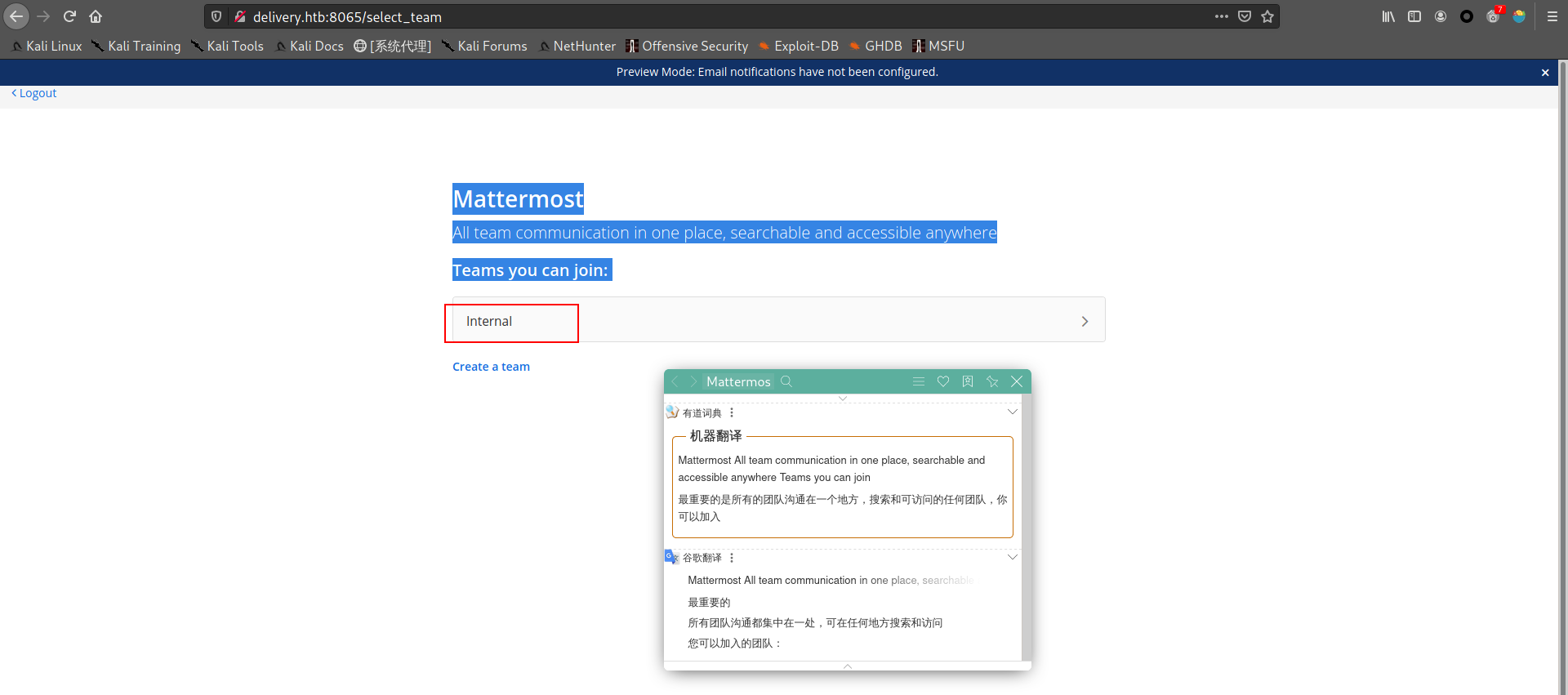
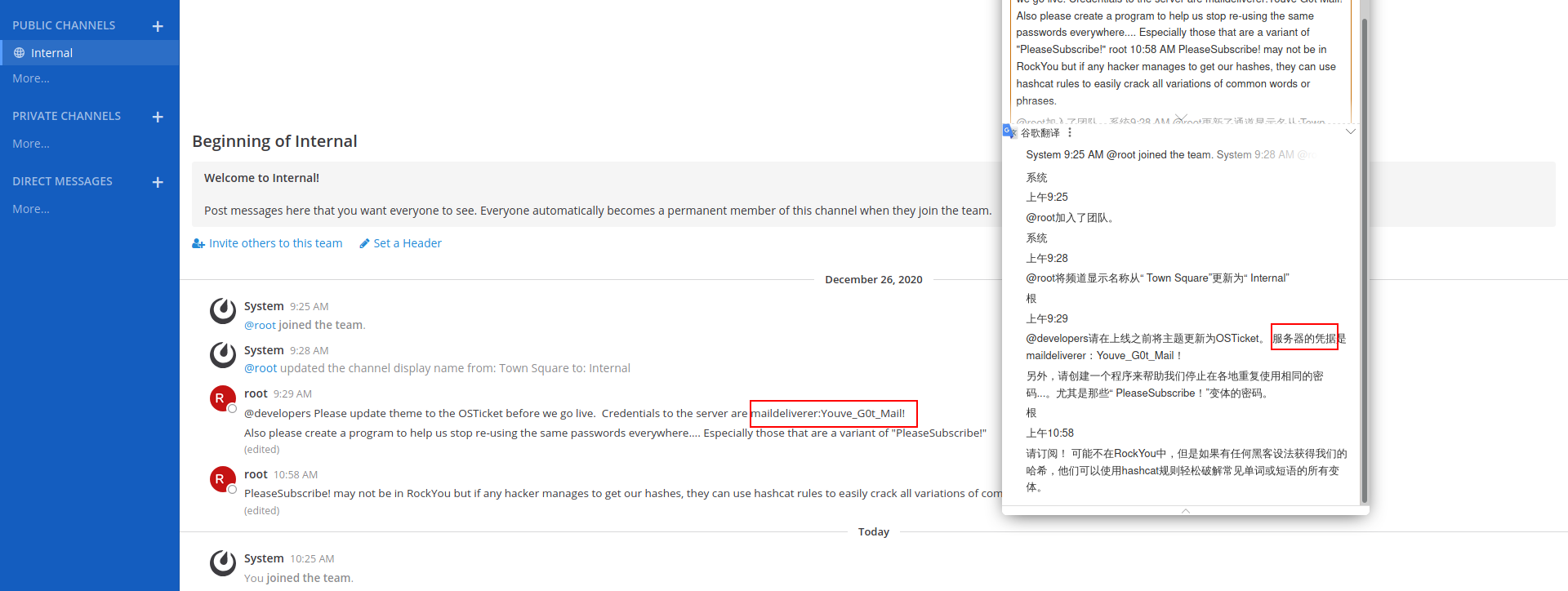
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
| root@JIYE:~/htb/delivery# hashcat -h | grep "crypt"
--truecrypt-keyfiles | File | Keyfiles to use, separated with commas | --truecrypt-keyf=x.png
--veracrypt-keyfiles | File | Keyfiles to use, separated with commas | --veracrypt-keyf=x.txt
--veracrypt-pim-start | Num | VeraCrypt personal iterations multiplier start | --veracrypt-pim-start=450
--veracrypt-pim-stop | Num | VeraCrypt personal iterations multiplier stop | --veracrypt-pim-stop=500
--scrypt-tmto | Num | Manually override TMTO value for scrypt to X | --scrypt-tmto=3
8900 | scrypt | Generic KDF
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) | Operating System
1500 | descrypt, DES (Unix), Traditional DES | Operating System
7400 | sha256crypt $5$, SHA256 (Unix) | Operating System
1800 | sha512crypt $6$, SHA512 (Unix) | Operating System
9300 | Cisco-IOS $9$ (scrypt) | Operating System
15100 | Juniper/NetBSD sha1crypt | Operating System
7401 | MySQL $A$ (sha256crypt) | Database Server
12200 | eCryptfs | Full-Disk Encryption (FDE)
22400 | AES Crypt (SHA256) | Full-Disk Encryption (FDE)
14600 | LUKS | Full-Disk Encryption (FDE)
13711 | VeraCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE)
13712 | VeraCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE)
13713 | VeraCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE)
13741 | VeraCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
13742 | VeraCrypt RIPEMD160 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
13743 | VeraCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
13751 | VeraCrypt SHA256 + XTS 512 bit | Full-Disk Encryption (FDE)
13752 | VeraCrypt SHA256 + XTS 1024 bit | Full-Disk Encryption (FDE)
13753 | VeraCrypt SHA256 + XTS 1536 bit | Full-Disk Encryption (FDE)
13761 | VeraCrypt SHA256 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
13762 | VeraCrypt SHA256 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
13763 | VeraCrypt SHA256 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
13721 | VeraCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
13722 | VeraCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
13723 | VeraCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
13771 | VeraCrypt Streebog-512 + XTS 512 bit | Full-Disk Encryption (FDE)
13772 | VeraCrypt Streebog-512 + XTS 1024 bit | Full-Disk Encryption (FDE)
13773 | VeraCrypt Streebog-512 + XTS 1536 bit | Full-Disk Encryption (FDE)
13731 | VeraCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE)
13732 | VeraCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE)
13733 | VeraCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE)
16700 | FileVault 2 | Full-Disk Encryption (FDE)
20011 | DiskCryptor SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
20012 | DiskCryptor SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
20013 | DiskCryptor SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
22100 | BitLocker | Full-Disk Encryption (FDE)
12900 | Android FDE (Samsung DEK) | Full-Disk Encryption (FDE)
8800 | Android FDE <= 4.3 | Full-Disk Encryption (FDE)
18300 | Apple File System (APFS) | Full-Disk Encryption (FDE)
6211 | TrueCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE)
6212 | TrueCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE)
6213 | TrueCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE)
6241 | TrueCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
6242 | TrueCrypt RIPEMD160 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
6243 | TrueCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
6221 | TrueCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
6222 | TrueCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
6223 | TrueCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
6231 | TrueCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE)
6232 | TrueCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE)
6233 | TrueCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE)
22700 | MultiBit HD (scrypt) | Password Managers
root@JIYE:~/htb/delivery# hashcat -h | grep "bcrypt"
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
root@JIYE:~/htb/delivery#
root@JIYE:~/htb/delivery# hashcat -m 3200 -a 0 root.hash word.list
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-8250U CPU @ 1.60GHz, 1408/1472 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache built:
* Filename..: word.list
* Passwords.: 77
* Bytes.....: 1177
* Keyspace..: 77
* Runtime...: 0 secs
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Wed Feb 3 19:25:48 2021 (1 sec)
Time.Estimated...: Wed Feb 3 19:25:49 2021 (0 secs)
Guess.Base.......: File (word.list)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 28 H/s (7.82ms) @ Accel:4 Loops:32 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 32/77 (41.56%)
Rejected.........: 0/32 (0.00%)
Restore.Point....: 16/77 (20.78%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:992-1024
Candidates.#1....: PleaseSubscribe!02 -> PleaseSubscribs
Started: Wed Feb 3 19:25:09 2021
Stopped: Wed Feb 3 19:25:50 2021
root@JIYE:~/htb/delivery#
root@JIYE:~/htb/delivery# hashcat -m 3200 -a 0 root.hash word.list --show
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
root@JIYE:~/htb/delivery#
|