1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
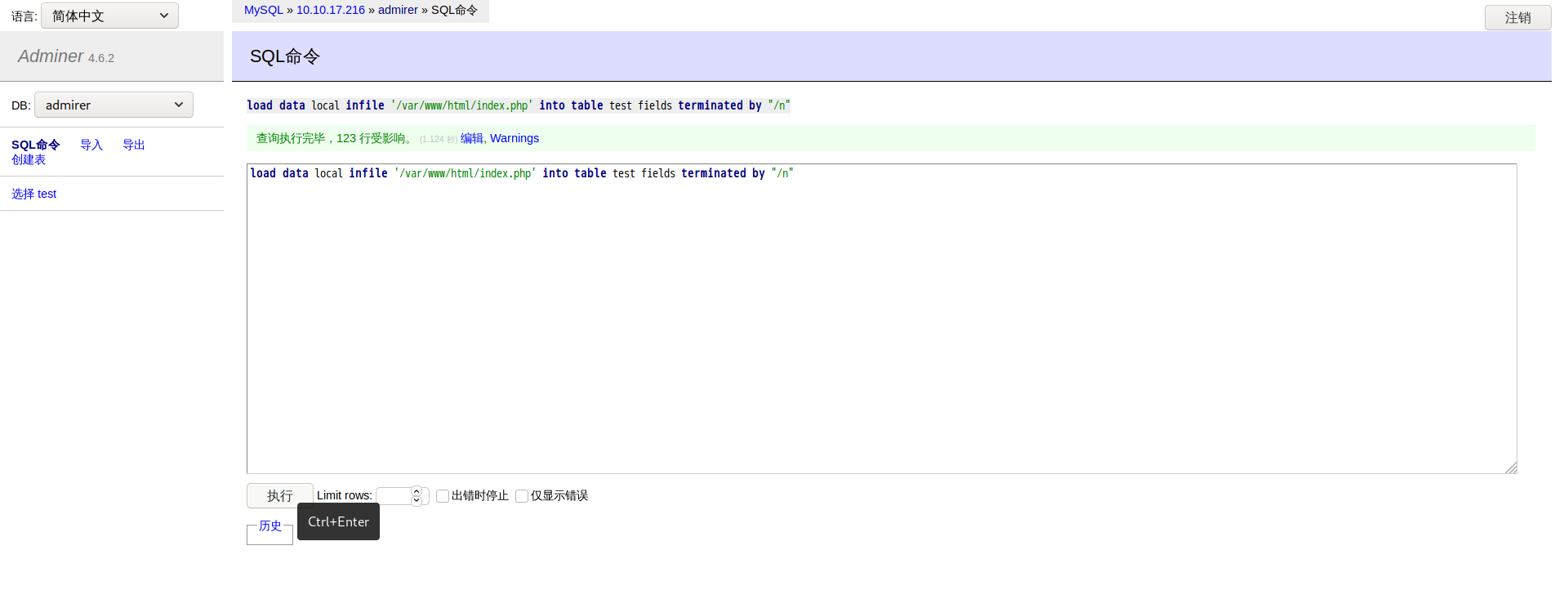
| -- Adminer 4.6.2 MySQL dump
SET NAMES utf8;
SET time_zone = '+00:00';
SET foreign_key_checks = 0;
SET sql_mode = 'NO_AUTO_VALUE_ON_ZERO';
SET NAMES utf8mb4;
DROP TABLE IF EXISTS `test`;
CREATE TABLE `test` (
`data` varchar(225) DEFAULT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
INSERT INTO `test` (`data`) VALUES
('<!DOCTYPE HTML>'),
('<!--'),
(' Multiverse by HTML5 UP'),
(' html5up.net | @ajlkn'),
(' Free for personal and commercial use under the CCA 3.0 license (html5up.net/license)'),
('-->'),
('<html>'),
(' <head>'),
(' <title>Admirer</title>'),
(' <meta charset=\"utf-8\" />'),
(' <meta name=\"viewport\" content=\"width=device-width, initial-scale=1, user-scalable=no\" />'),
(' <link rel=\"stylesheet\" href=\"assets/css/main.css\" />'),
(' <noscript><link rel=\"stylesheet\" href=\"assets/css'),
(' </head>'),
(' <body class=\"is-preload\">'),
(''),
(' <!-- Wrapper -->'),
(' <div id=\"wrapper\">'),
(''),
(' <!-- Header -->'),
(' <header id=\"header\">'),
(' <h1><a href=\"index.html\"><strong>Admirer</strong> of skills and visuals</a></h1>'),
(' <nav>'),
(' <ul>'),
(' <li><a href=\"#footer\" class=\"icon solid fa-info-circle\">About</a></li>'),
(' </ul>'),
(' <'),
(' </header>'),
(''),
(' <!-- Main -->'),
(' <div id=\"main\"> '),
(' <?php'),
(' $servername = \"localhost\";'),
(' $username = \"waldo\";'),
(' $password = \"&<h5b~yK3F#{PaPB&dA}{H>\";'),
(' $dbname = \"admirerdb\";'),
(''),
(' // Create connection'),
(' $conn = new mysqli($servername, $username, $password, $dbname);'),
(' // Check connection'),
(' if ($conn->connect_error) {'),
(' die(\"Connection failed: \" . $conn->connect_error);'),
(' }'),
(''),
(' $sql = \"SELECT * FROM items\";'),
(' $result = $conn->query($sql);'),
(''),
(' if ($result->num_rows > 0) {'),
(' // output data of each row'),
(' while($row = $result->fetch_assoc()) {'),
(' echo \"<article class=\'thumb\'>\n\";'),
(' echo \"<a href=\'\".$row[\"image_path\"].\"\' class=\'image\'><img src=\'\".$row[\"thumb_path\"].\"\' alt=\'\' /></a>\n\";'),
(' echo \"<h2>\".$row[\"title\"].\"</h2>\n\";'),
(' echo \"<p>\".$row[\"text\"].\"</p>\n\";'),
(' echo \"</article>\n\";'),
(' }'),
(' } else {'),
(' echo \"0 results\";'),
(' }'),
(' $conn->close();'),
(' ?>'),
(' </div>'),
(''),
(' <!-- Footer -->'),
(' <footer id=\"footer\" class=\"panel\">'),
(' <div class=\"inner split\">'),
(' <div>'),
(' <section>'),
(' <h2>Allow yourself to be amazed</h2>'),
(' <p>Skills are not to be envied, but to feel inspired by.<br>'),
(' Visual arts and music are there to take care of your soul.<br><br>'),
(' Let your senses soak up these wonders...<br><br><br><br>'),
(' </p>'),
(' </section>'),
(' <section>'),
(' <h2>Follow me on ...</h2>'),
(' <ul class=\"icons\">'),
(' <li><a href=\"#\" class=\"icon brands fa-twitter\"><span class=\"label\">Twitter</span></a></li>'),
(' <li><a href=\"#\" class=\"icon brands fa-facebook-f\"><span class=\"label\">Facebook</span></a></li>'),
(' <li><a href=\"#\" class=\"icon brands fa-instagram\"><span class=\"label\">Instagram</span></a></li>'),
(' <li><a href=\"#\" class=\"icon brands fa-github\"><span class=\"label\">GitHub</span></a></li>'),
(' <li><a href=\"#\" class=\"icon brands fa-dribbble\"><span class=\"label\">Dribbble</span></a></li>'),
(' <li><a href=\"#\" class=\"icon brands fa-linkedin-in\"><span class=\"label\">LinkedIn</span></a></li>'),
(' </ul>'),
(' </section>'),
(' </div>'),
(' <div>'),
(' <section>'),
(' <h2>Get in touch</h2>'),
(' <form method=\"post\" action=\"#\"><!-- Still under development... This does not send anything yet, but it looks nice! -->'),
(' <div class=\"fields\">'),
(' <div class=\"field half\">'),
(' <input type=\"text\" name=\"name\" id=\"name\" placeholder=\"Name\" />'),
(' </div>'),
(' <div class=\"field half\">'),
(' <input type=\"text\" name=\"email\" id=\"email\" placeholder=\"Email\" />'),
(' </div>'),
(' <div class=\"field\">'),
(' <textarea name=\"message\" id=\"message\" rows=\"4\" placeholder=\"Message\"></textarea>'),
(' </div>'),
(' </div>'),
(' <ul class=\"actions\">'),
(' <li><input type=\"submit\" value=\"Send\" class=\"primary\" /></li>'),
(' <li><input type=\"reset\" value=\"Reset\" /></li>'),
(' </ul>'),
(' </form>'),
(' </section>'),
(' </div>'),
(' </div>'),
(' </footer>'),
(''),
(' </div>'),
(''),
(' <!-- Scripts -->'),
(' <script src=\"assets/js/jquery.min.js\"></script>'),
(' <script src=\"assets/js/jquery.poptrox.min.js\"></script>'),
(' <script src=\"assets/js/browser.min.js\"></script>'),
(' <script src=\"assets/js/breakpoints.min.js\"></script>'),
(' <script src=\"assets/js/util.js\"></script>'),
(' <script src=\"assets/js/main.js\"></script>'),
(''),
(' </body>'),
('</html>');
-- 2020-09-05 08:07:51
|